What are DDoS Attacks: Everything You Need to Know
For as long as there has been a digital realm (the internet), there have been hackers. As long as there have been hackers, there have been DDoS Attacks. DDoS attacks are one of the most common forms of hacking out there: they’re simple, easy to launch, and effective. Tell me, though, do you really know what DDoS attacks are?
While IT and cybersecurity experts deal with DDoS attacks on a regular basis, most everyday Internet users don’t really understand what they are. Consider this the Average Joe’s Guide to DDoS Attacks, and let me help you understand what’s really going on behind the scenes of a hack in Layman’s terms.
DDos Explained – Content Index

What are DDoS Attacks: Everything You Need to Know
Terms You Should Know
This guide is written for internet users who don’t have a background in IT or cybersecurity, so some of the terminologies might be very new for you. There are a few things you need to understand first to make everything a little easier. Please keep in mind that these are very simplified explanations.
Definitions
- Server: A server is a computer that has a program or some form of hardware that can “communicate” with other computers (clients). A computer with a printer connected to it can be considered as a server. Servers can be digital, too. A web server, for example, can communicate with other servers with a series of protocols.
- Host: A computer or other device connected to a network.
- DNS: Short for Domain Name System, a DNS is the phone book of the internet. This is how IP addresses are assigned user-friendly (read by humans) domain names, and how the internet can keep track of all of them.
- Malware: Malware is short for “malicious software”. It’s software that is built to damage or disable devices. Malware includes viruses, spyware, adware, and a few other classifications.
- Protocol: Protocols are the rules used by telecommunication connections to communicate with each other.
- Traffic: Traffic online is the same as traffic in person, kind of. Online traffic is simply the amount of data that’s moving across a network at any given time. The same as the number of vehicles moving across a location at any given time.
- Client: Also known as users. Clients are usually your PCs, laptops, and other devices that you can connect to the internet with.
- Packet: A packet is the unit of data read by all of the internet’s different parts (ports, protocols, servers,etc..).
- Botnet: When malware infects your device, it leaves a small bot hidden. The hacker that infected your device with the bot can call on your bot and on all of the bots in the devices he/she has infected and launch an attack using them. The network of bots is conveniently called a botnet.
What is a DoS Attack?
Someone with no background in anything IT may see “DoS” and “DDoS” and get a little confused.
DoS is short for “denial-of-service”. It’s an umbrella term for cyber-attacks that make a particular service (or website, or network, etc.) unavailable for people who are trying to use it. DDoS is simply the most common type of DoS attack.
The way this is done is by flooding the target website (or connection, or network, etc) with useless traffic. The point is to overwhelm it in a way where it can’t respond to regular users. Thus, denying users access to the “service” they’re looking for.
What is a DDoS Attack?
As a “sub-section” of DoS Attacks, DDoS Attacks are short for distributed denial-of-service. The way you differentiate between a DoS attack and a DDoS attack is by the number of computers and internet connections used in an attack. DDoS attacks use multiple computers and internet connections, flooding a target’s network or server with botnets. You can usually stop a DoS attack as there’s on IP that you would need to block (one internet connection = one IP). A DDoS Attack, on the other hand, is almost impossible to stop since it’s very difficult to figure out which traffic is coming from legitimate users and which is coming from the attack.
Categories of DDoS Attacks
There are three basic categories of DDoS Attacks: Traffic attacks, bandwidth attacks, and application attacks.
Traffic Attacks
These are sometimes also referred to as “Volume-based Attacks” or “Protocol Attacks”. A traffic attack floods the target with huge volumes of TCP, UDP, and ICMP packets. Transmission Control Protocols (TCP) and User Datagram Protocols (UDP) are protocols used to transfer information. TCP makes sure that the packets of data are sent in order and as a whole. UDP, on the other hand, send data packets faster because the order isn’t really relevant, and data is not sent out as a single unit. The Internet Control Messaging Protocol (ICMP) deals with the network itself, not the data being sent. It’s considered a “control” protocol and carries information about the state of the network itself.
Traffic attacks effectively aim to flood these 3 protocols, making it difficult to understand the data coming in, both as a whole or not, and to exchange information about the network as a whole.
Bandwidth Attacks
Also known as “Network-centric” or “Volumetric” attacks, bandwidth attacks target available bandwidth with packet floods. Here, the attack isn’t targeting the way a site or network communicates with incoming data. It’s targeting server resources, the network’s infrastructure, and its management tools.
In this kind of attack, the whole network could stop responding, leading to a genuine denial of service.
Application Attacks
An easy attack to launch, since it doesn’t cost the attacker much bandwidth, Application Attacks target the part of the network service you (a human) use. In other words, it targets the “applications” found in a network. Flooding a network’s application layer can also result in a complete denial of service.
I’ll give you an example of what an application layer is. If you log into your email account, you communicate with the application layer of the network service you’re using (Gmail, for example). If more than a billion IPs are trying to communicate with that specific application, it’s going to get a bit overwhelmed.
As you can see, all three categories aim to do the same thing: cause the network enough stress to incapacitate it. Traffic attacks deal with flooding the tools a network uses to communicate data with other networks, bandwidth attacks flood the infrastructure of a network, and application attacks flood the tools a network uses to communicate with its human users.
Common Types of DDoS Attacks
Of course, there are many ways to implement any one of the above three categories. To make things a little worse, our tech is evolving so fast that new types of attacks are being used more often. However, the most common DDoS attacks are listed below. Keep in mind that all of these attacks can also be done by using botnets.
SYN Flood
A SYN Flood is a Traffic-based DDoS attack that targets the TCP. When a client and a server are in communication, something called a “TCP three-way handshake” should occur for both parties to understand each other. Usually, the client will send the server a synchronize message (SYN), the server will then acknowledge the synchronize (Syn-ACK), and the client will acknowledge that acknowledgment (ACK). So, effectively:
- Client requests connection from server (step 1)
- Server acknowledges the connection request (step 2)
- Client acknowledges that the server is ok with connecting (step 3)
When these three steps happen, a connection is established between the client and the server.
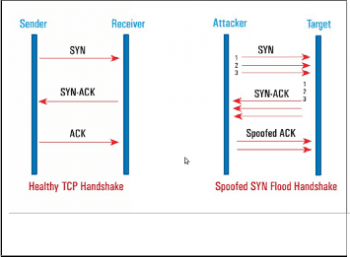
A SYN Flood is when an attacker floods the server with SYN messages without giving it a chance to reply (or without having a visible IP address the server can reply to). The server will send out the SYN-ACK, but won’t get an ACK back in return, even though it will wait for one. The issue is, the server can’t really close down this connection, and needs to wait for it to time out on its own. The attacker, though, won’t give the server that luxury. Before the connection times out, another SYN request would have reached the server. Now, you have a bunch of open-ended connection requests, and a server over-saturated with data. Normal users won’t have the space to try and connect to it, causing a denial of service.
UDP Flood
As I mentioned above, UDP is similar to TCP in that it reads data packets coming into the network. Unlike TCP, no three-way handshake is needed to established any kind of connection. UDPs usually are at work when you want faster connections, so calling someone on WhatsApp or Skype would utilize UDP not TCP.
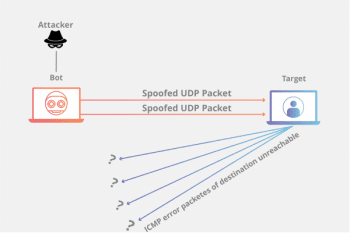
Because of the chaotic nature of UDP, it is actually very easy to launch a UDP flood attack. An attacker will send packets of data to the UDP that don’t really refer to anything. When the UDP reads those packets to find which application the “client” wants to connect with, it won’t find anything legible. The UDP will then send the client an ICMP “Destination Unreachable” packet. The more gibberish the UDP has to read, the more “Destination Unreachable” packets it sends out, the less it’s capable of handling genuine user requests.
HTTP Flood
This is a form of Application attack. In this attack, an HTTP client (like a web browser) will flood the application with requests that are so resource-consuming, it will eventually stop being able to process them.
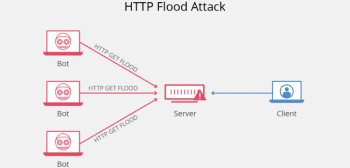
HTTP requests are how an HTTP client communicates with an application or a server. There are two types of requests, each one referring to a different type of resource. A GET request is the HTTP client asking for standard content, like images or text. A POST request, on the other hand, is a request for dynamically generated content or resource. Both GET and POST requests can be used in an HTTP Flood. GET request floods scale better if the attacker is using botnets, while a POST request flood can trigger complex processing on the end of the server. Either way, an HTTP flood will block a server or application from being able to reply to all of the HTTP requests.
Ping of Death
Also known as PoD, a Ping of Death attack works on the idea of asking the server to re-assemble packets beyond its capacity. All the attacker needs to know is the IP of the machine (computer, server, etc..) that he/she wants to shut down.
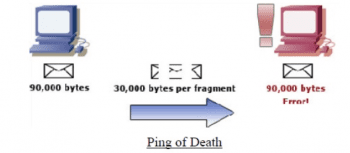
An attacker will send malformed ping packets in fragments to the server. When the server tries to reassemble the packets (which is normal for a server), the server will end up with a packet that’s too big for it to read. This will overwhelm the system, causing a memory overflow that can cause the system to crash.
Smurf Attack
This attack is a little different to the ones I’ve described above. In a smurf attack, the hacker uses a type of malware called DDoS.Smurf malware and targets the IP broadcast network a server belongs to.
Usually, a host will contact another host by sending an ICMP Echo (ping) request. This request triggers an automatic response from the second host, and the time it takes the response to arrive measures how “far” the hosts are to each other virtually. In an IP broadcast network (think networks connected via LAN), the request is sent to all the hosts on the network at the same time, prompting each individual host to send back a response.
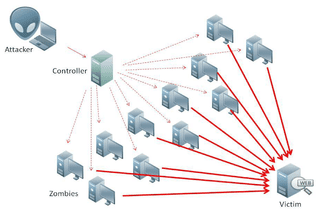
A smurf attack takes this a step further by amplifying the effects of this form of communication. The malware is used to generate a fake ping request using the spoofed IP of the target server address. When the request is sent to the broadcast network, instead of the replies coming back to the sender, they all go to the target server. The more ping requests sent, the more replies go to the target, the more the target gets overwhelmed with replies to ping requests it didn’t send out.
Slowloris
In this DDoS attack, the attacker will periodically send out partial HTTP requests to the target server until the server can’t handle new connections anymore.
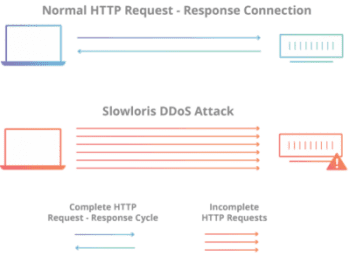
What happens here is that an HTTP request, even if it’s partial, still forms a connection between a host and a server. The attacker will send a partial HTTP request, the connection will open, the attacker will never finish the request. This leaves the server with an open connection waiting for a request that won’t be completed. The hacker continuously does this, sending out more and more partial requests. With each request, the server will form a connection and wait for the request to be completed. Eventually, the server will exceed its maximum concurrent connection limit (how many connections it can have at the same time) and won’t be able to handle any more requests, even if they’re legitimate.
DNS Amplification
Another traffic-based attack, a DNS amplification attack uses the DNS to amplify small queries into huge quantities of UDP packets, which flood the target’s server.
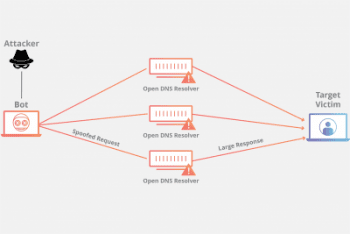
Here, the attacker sends a DNS query to a DNS resolver using the target’s spoofed IP. The DNS resolver will reply back to the target’s server with a DNS response. The attacker sends out so many requests that the number of responses (in UDP packets) will overwhelm the target’s server. The twist here is that the DNS queries sent out are amplified using a specific protocol extension. The protocol extension will amplify the message size, and will usually lead to a 70:1 amplification ratio.
Advanced Persistent DoS
APDoS for short, this is an attack that utilizes many of the types of the attacks described here. An APDoS attack usually lasts for long periods of time, and switches from one type of attack to another. The attacker can switch from HTTP flooding to SYN flooding to Smurf attack, etc. These types of attacks are usually used by an attacker that wants to cause serious damage, which means they aren’t usually targeting individual internet users.
Zero-day DDoS Attacks
Have you heard the stories of mega-tech companies hiring kids who hacked into their system? I remember people going crazy over these stories, but it does make sense in a way: If someone was able to find the vulnerability in the system you previously thought didn’t have any, you’d want them on your team. Right?
Zero-day DDoS attacks have nothing to do with the attacker’s future career trajectory. They have everything to do with the idea of an attacker knowing the vulnerabilities in a system before the target does. They’re called zero-day DDoS attacks because they’re new, they haven’t been used before.
Not every Zero-day attack is 100% new. Small changes to attacks are considered zero-day attacks. If a hacker uses a known attack in a new way, it’s considered a zero-day attack. Why? Because it’s not that easy to shut down a tweaked attack.
Why Would Someone Launch a DDoS Attack?
Easy. It’s simple, not very sophisticated, and effective. DDoS attacks are legitimate threats in this day and age, and a big enough network of botnets can bring down just about anything.
As for the reasoning behind launching a DDoS attack, it can be anything from boredom to activism. Let me explain.
There are categorizations out there for hackers based on their morality, because believe it or not, not every hacker is bad. I’m taking this a step further and saying that not every attack is “evil”, either:
Script Kiddies
Script Kiddies are new “hackers” who won’t really become full-fledged hackers. These guys will use copied code as a virus or watch a YouTube video on how to use some older, overused hacking software and try it out for themselves. Unlike the other categories of hackers, Script Kiddies won’t hack with the intention of stealing data or information. These are people who are testing it out “for fun”.
In other words, they’re new, they’re trying it out, but they’re not opting for the lifetime subscription.
White Hats
You might know White Hats with their other description: Ethical hackers. These are the good guys of the hacking community (yup, even hackers have good guys and bad guys). Usually, these kinds of hackers end up in internet security positions and use their skills to find the problems in the system and fix them. White Hats can also help defend a system against a malicious attack on their own.
White Hats can be interested in hacking as a process, but they don’t use it as a tool for malice.
Grey Hats
The most common type of hacker, the Grey Hat, isn’t really good or bad. These guys will usually spend their time playing around with systems and testing out their limits, but they won’t actually cause any harm. They won’t really do any good, either.
Grey Hats are the average hacker: the middle ground.
Green Hats
Green Hats are like Script Kiddies in the sense that they’re new to the hacker community. Unlike Script Kiddies, though, Green Hats have every intention of becoming fully-fledged hackers.
Green Hats are baby hackers, and they can “grow up” to be whatever different color hacker they choose.
Blue Hats
Ever pissed someone off then found out they “hacked” into your social media accounts and changed all your passwords? That person would, kind of, be considered a Blue Hat. Blue Hats are people who use hacking techniques to get back at someone, but they resemble Script Kiddies in the sense that they “follow instructions” instead of trying to learn for real.
Blue Hats are the brats of the hacking world, they’ll pick their target for “revenge” purposes but won’t actually continue down that path.
Black Hats
Black Hats are what the general public thinks all hackers are. These are the “bad guys” of the hacking world. They know they’re tricks and are ready to use them for personal gain without hesitation.
When you think dangerous hacker with no moral compass, you’re thinking only of Black Hats.
Red Hats
The easiest way to explain this category of hacker is a White Hat who uses the same “tools” as a Black Hat. Red Hat hackers are the vigilantes of the hacking world. They’ll utilize whatever tool is in their arsenal to catch the bad guys (Stop a Black Hat hack), even if it’s targetting their own malicious attack at the Black Hat hacker.
Batman. Red Hats are the Batman of the internet.
Hacktivists
Remember this, when Anonymous took down state emails and websites for up to 4 hours in the US? This was part of their #OpUSA movement, which was a way of protesting the US’s political inclinations (it didn’t really take off much). Hacktivists, like Anonymous, hack government, big brands, and even influential people for the purpose of showing their political (or environmental, or social) disdain.
In other words, Hacktivists are online activists.
Examples Throughout History: Famous DDoS Attacks
To really explain how heavy a DDoS attack can be, here are a few examples of some of the most famous attacks in modern history:
- Mafiaboy: This is considered to be one of the first and largest DDoS attacks of all time, and it was launched by a 15-year-old Canadian (Michael Calce) who went by the name of Mafiaboy. The attack lasted about a week in early-February, 2000. Mafiaboy managed to knock out websites as big as CNN, Amazon, Yahoo, and eBay. Now, Mr. Calce is a White Hat hacker who runs a security company called Optimal Secure.
- GitHub: This year, the code sharing website GitHub was hit with what was then considered to be the biggest DDoS attack in history. The traffic thrown at the website measured up to 1.35Tbps. This is a monumental amount of traffic, and GitHub (obviously) wasn’t able to handle it. The website was only offline for a few minutes but started a new hacking trend called memcrashing.
- Estonia: In April 2007, Estonia was hacked. Yup, the whole country. Reportedly thousands of computers launched a DDoS attack on government, banks, media outlets, telecommunication networks, and name servers. Up until then, Estonia was at the forefront of digital enterprise.
How to Stay Safe from a DDoS Attack
DDoS attacks are very difficult to stop, but they aren’t impossible to safeguard against. For average internet users, there are a few things you can do to make sure that you’re attacked yourself or used as part of an attack (as part of a botnet).
- Have a solid anti-malware software installed on your devices. Malware is the simplest and most used method of turning unsuspecting people’s computers as part of a botnet army. Remember to only download links off of trusted websites and to run regular checks for malware.
- Minimize your use of public WiFi connections. Public WiFi can be very dangerous, and many hackers use these networks to hack into random people’s devices and to install malware.
- Get a VPN and use it. Frequently. A VPN will spoof your IP and tunnel your traffic through a secure connection. If you’re using a VPN, a hacker won’t be able to find your IP and any excessive traffic will be filtered out by the VPN. Take a look at these top VPNs for DDoS protection.
DDoS attacks aren’t really used on individual users as much as they’re used to take down websites.
For Website Owners
If you happen to be a website owner (it could be for your business or your blog) and you want to make sure that you’re protected against DDoS Attacks, here are a few things you should keep in mind:
- Over-do-it with the bandwidth. Make sure your website has more bandwidth than it would need. This way, your website would be able to handle fluctuations in traffic.
- Have your Web Hosts’ contact information ready. You should make sure that you can contact your web host whenever needed. If you suspect a DDoS attack is happening, contact your web host, they should be able to drop the traffic to your website and filter out the botnets’ requests.
- Be ok with removing pressure off of some of your systems, like your logging files. When a DDoS attack is happening, the system that logs requests and user activity will get overwhelmed, and fast. You need to be ready to drop those files to release the pressure a little.
- Have a pre-defined plan. Understand that being hacked is a possibility and have an action plan ready for it. There are a lot of great resources that you can find online to help you out with that. The truth is, it’s better to have a plan- even if it’s a small one- than to be caught off-guard.





