Fake E-Shop Platforms – Customers of Malaysian Banks Beware
There are no words to describe how online shopping has made our life much easier. The practice is very popular across the globe as more than 2.14 billion users shop online. However, as good and convenient as this might be, it doesn’t come without drawbacks, particularly being used for cybercrime.

A while back, threat actors pretended to be Maid4u, a legitimate cleaning service brand to lure victims in. Now, three more websites have surfaced that follow in the latter’s steps.
Apparently, the campaign is still ongoing as these websites host 3 different apps that are targeting customers who belong to eight Malaysian banks. What is this all about and how can users avoid it? We’ve discussed everything you need to know below.
Fake Android Shopping Apps – Simple Click, Drastic Consequences
As mentioned, online shopping has made everything easy for billions of users around the world. All they have to do is sit back on their couch and buy things from the comfort of their homes using their Smartphones.
However, what’s convenient isn’t always the safest option, especially when the mobile device operates on AndroidOS. Unfortunately, the Operating System is always targeted with malware campaigns, even through its official Google Play Store.
This time around, several security firms have reported fake apps impersonating online shopping platforms. First, MalwareBytes shared three malicious websites, followed by ESET with four additional ones.
The apps are a total of 7 and they include the following:
- Grabmaid
- Maria’s Cleaning
- Maid4u
- YourMaid
- MaidACall
- PetsMore
- Maideasy
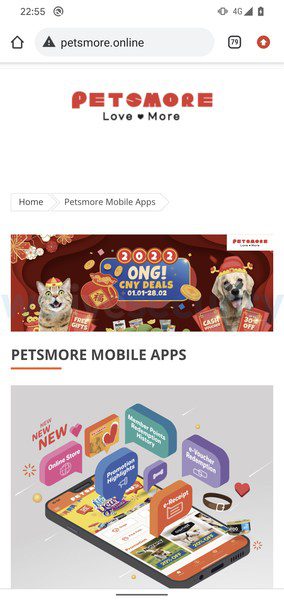

Since 5 of these apps are not distributed through Google Play, the risk of spreading can be contained due to their unofficial status. However, they’re still getting to users and targeting their banking credentials.
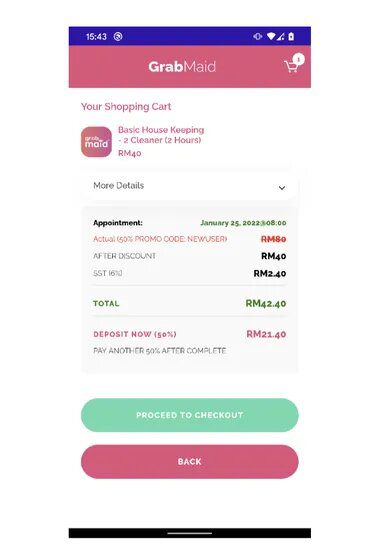
The apps’ resemblance to the real ones is uncanny, but the difference is that they don’t allow the users to checkout (purchase) directly.
The users have to click on a button that links to Google Play (Fake), where they’ll think that they’re paying through the official repository.
However, as the report states, the apps are linked to the attacker’s servers, and users have to allow “Install unknown apps” for the malicious process to work.
If they don’t enable the feature, the infection phase ceases to commence. If they do allow it, they’ll be shown different payment options to use through the apps.
The malicious domains don’t allow customers to purchase products or services directly. Instead, the attack vector is a button that claims to link to Google Play, Google’s official app repository, for customers to pay through.
The Malicious Purchase
On the fake apps, the victims can purchase the product through either a credit card or directly through bank transfers. But the threat actors know best, which is why the first one doesn’t work.
Instead, users can only complete their transactions through bank transfers. Once they click on that, they’ll head over to a fake payment page that shows eight Malaysian banks to choose from:
- Maybank
- Affin Bank
- Public Bank Berhad
- CIMB Bank
- BSN
- RHB
- Bank Islam Malaysia
- Hong Leong Bank

Now, it’s time for the users to submit their credentials (typical payment process). But instead of finalizing the checkout phase, these credentials go straight to the attacker’s C2 server and an error pops up. According to the researchers:
“To make sure the threat actors can get into their victims’ bank accounts, the fake e-shop applications also forward all SMS messages received by the victim to the operators in case they contain two-factor authentication (2FA) codes sent by the bank,” the researchers added.
The research also states that the malware info-stealer isn’t as sophisticated as other ones on the cybercrime scene – it’s very simplistic.
This can be seen as the infected apps cannot hide, hijack, or even delete the 2FA SMS messages from a victim’s handset. In other words, users can know that someone is trying to access their bank account.
The Real Ones Break Silence
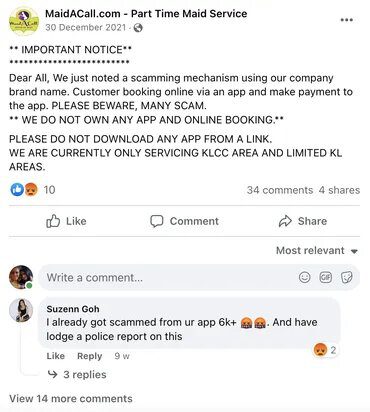
Impersonations are bound to be called out, and that’s exactly what happened when one of the impersonated companies addressed the issue on Facebook.
MaidACall published a Facebook post to warn all of its customers that hackers are attempting to steal their banking credentials by creating a fake app for their service:
“Dear All, We just noted a scamming mechanism using our company brand name. Customer booking online via an app and make payment to the app.
PLEASE BEWARE, MANY SCAM. WE DO NOT OWN ANY APP AND ONLINE BOOKING. PLEASE DO NOT DOWNLOAD ANY APP FROM A LINK. WE ARE CURRENTLY ONLY SERVICING KLCC AREA AND LIMITED KL AREAS.”
ESET did state that the campaign is currently running exclusively in Malaysia. However, they’re warning of an expansion to other countries, as the threat actors might be targeting more banks in the near future.
Fake Android Shopping Apps – You’re Paying Big Time
Cybercriminals are always finding new ways to target your sensitive information. While this attempt using fake Android shopping apps targets your banking accounts, the next one might also feature credit card theft.
You should always know what apps to trust, especially those from an unofficial source. If you’ve already used the service, you should know if it uses apps or not – just like with MaidACall.
Make sure you don’t submit your credit card information where they’re not supposed to be entered. Stay vigilant, stay safe.