Google Play Store Does it Again – A Triple Threat of Malware Infiltration
Here we go again! Google Play Store is once more hosting applications that deliver malware. The official Android store has had its fair share of malware infiltration, especially in the past few months. However, this time around, it’s a bit bigger as the app store is hosting dozens of fraudulent apps propagating Joker, Facestealer, and Coper malware families.

One malware variant can cause chaos. What do you think will happen if there are three of them? Google Play Store is supposed to be a trusted source for discovering and installing apps.
But lately, trust has become a big word, considering how many slip-ups the store has gone through. From subscribing users to unwanted paid services to total device control, this is serious and we’re here to discuss it.
Another Slip Up – From Play Store to Malware Play Ground
As we mentioned, threat actors are always elevating their techniques and finding new ways for better success rates in their malicious activities.
Unfortunately, regardless of how “trusted” Google Play is, these attackers are sneaking past Google’s security barriers and luring victims into handing over whatever they want them to.
A while ago, Google Play Store hosted applications with over 3 million downloads delivering Autolycos malware. Now, three not-so-new families have infiltrated the app store.
Joker malware is well-known to be one of the most dangerous malicious entities on the market. That’s clearly stated in Zscaler ThreatLabz’s report:
“Joker is one of the most prominent malware families targeting Android devices. Despite public awareness of this particular malware, it keeps finding its way into Google’s official app store by regularly modifying the malware’s trace signatures including updates to the code, execution methods, and payload-retrieving techniques.”
The Joker fleeceware has a lot of capabilities. Once it infects a device, it can subscribe the victims to premium services without their consent. Not only that, but it can also intercept SMS messages, contact lists, and device information.
Aside from Joker, Coper, which we’ll be digging deeper into later, can also subscribe to premium services, send messages, lock/unlock the device screen, and perform overly attacks. What’s worse is that it can also prevent uninstallation attempts.
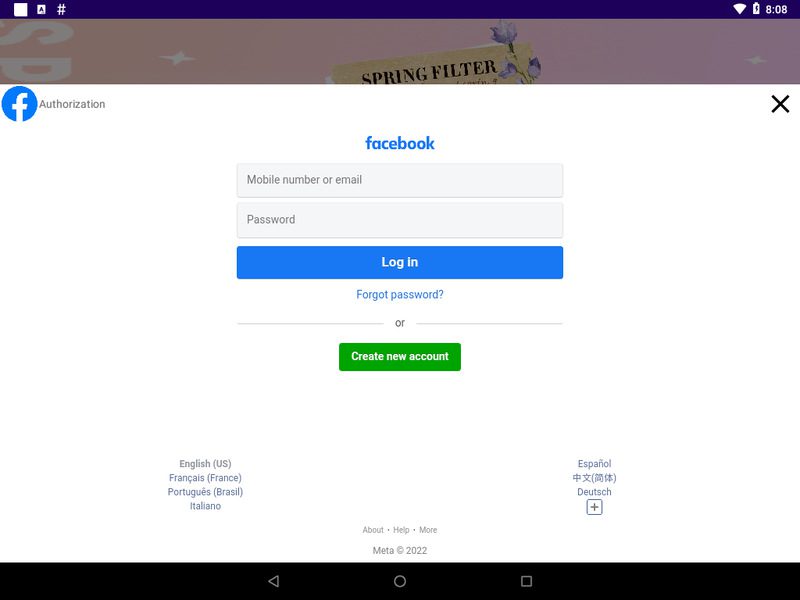
And finally, we have the FaceStealer malware that has a habit of targeting Facebook users with fake Facebook login screens.
The infected application shows a Facebook login screen and doesn’t allow the users any access unless they submit their credentials. Once they do, the attackers harvest them alongside their authentication tokens.
App Infection At Its Best
According to ThreatLabz researchers, the following malicious apps in the Google Play Store are spreading the Joker malware:
- Simple Note Scanner
- Universal PDF Scanner
- Private Messenger
- Premium SMS
- Smart Messages
- Text Emoji SMS
- Blood Pressure Checker
- Funny Keyboard
- Memory Silent Camera
- Custom Themed Keyboard
- Rich Theme Message
- Timestamp Camera
We didn’t include all the applications are there are more than 50 to mention. However, you can check the full list in Zscaler’s report.
Coper, on the other hand, is taking root in a single application – a free QR scanner called Unicc QR Scanner. This trojan is known for targeting banking apps in countries like Europe, Australia, and South America.
When the user installs the app, an update notice will pop up. That’s when the malicious practices begin.
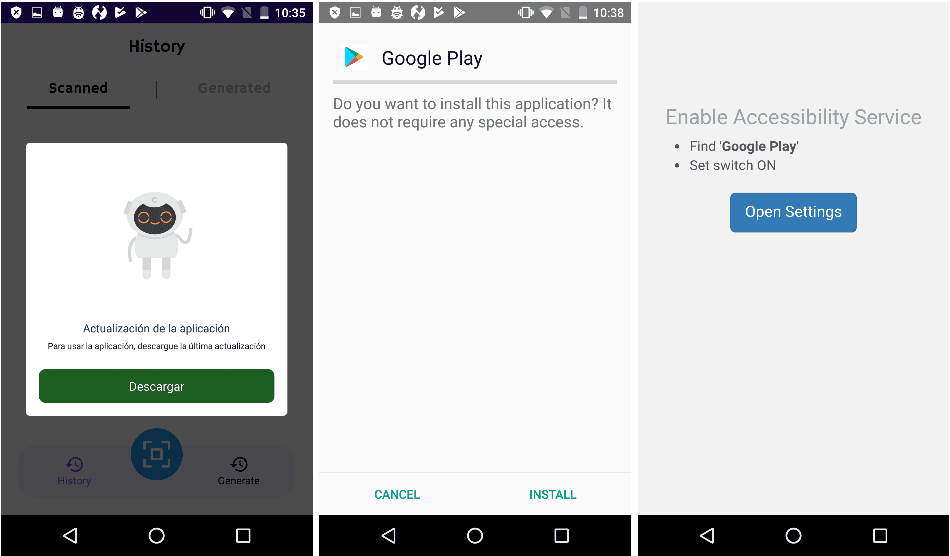
Finally, FaceStealer is more subtle in its approach. It has one goal – stealing the victims’ Facebook credentials. Once it sets root, it’ll showcase a fake Facebook login page that harvests the credentials once they’re entered.
The applications hosting these 3 malware families have harnessed thousands of downloads throughout their existence on the Android store.
When you download an app, always refrain from granting unnecessary permissions. Make sure you read well before you agree to anything.
Google Play Store Malware – x3 The Malware, x100 The Damage
A lot of applications on the Google Play Store are deemed unnecessary, untrusted, and un-vetted. You don’t have to install everything you come across.
Even on Google Play Store, threat actors will be on the hunt for new victims. In other words, if you want to install an application, make sure to check the ratings as well as the users’ reviews.
But before you make any rash decision, read the reviews well – they might be bots created by the attackers to legitimize their malicious software.





