Android Banking Trojan Infects over 300,000 Device via Apps on Google Play
Have you ever heard of the “Deceive the Heavens to Cross the sea” stratagem? Yeah, the “瞞天過海, Mán tiān guò hǎi” is a Chinese strategy, which translates to masking one’s real goals by not alerting victims who lack the proper knowledge to his/her real intentions or plans. In the cyber world, planting an Android banking trojan is one form of such a strategy.
Apparently, hackers and malicious actors are adopting this strategy to plant malware on Android devices using applications distributed on Google Play Store.
A while ago, the “Joker malware” infested dozens of Android apps. Now, new malware families have emerged, spreading trojans on almost 300,000 Android devices.
What is their goal? Simple – steal online bank credentials. We’ll shed more light on the matter as this article has everything you need to know
Zero Footprints, 300,000 Infected Devices
Banking account credentials theft has become very common in the last few years. In fact, thousands of users have been targeted with banking trojans in 2021.
The attackers use fake bank login form overlays displayed within legitimate apps’ login screens. This can easily trick the users as they have no idea that they are being targeted, mainly since the app comes from the official Google Play Store.
Once the attack is finalized, the stolen credentials end up on the attackers’ own servers. After that, they’ll use them in one of the following, if not both:
- The attackers might steal cryptocurrency and money from victims’ accounts.
- The attackers might sell the victoms’ credentials to other threat actors.
Now, let’s explain what’s going on. Based on a report by ThreatFabric, this attack consists of four different malware dropper campaigns that distribute banking trojans on the Google Play Store.
We all know that tricking Google Play into including such infected apps is nothing new. However, the App Store has upped its game with its policies and, apparently, it forced threat actors to up theirs and come up with tactics to evade detection.
The Infection Process Begins
It starts by creating an app that focuses on common themes such as PDF scanning, QR codes, fitness, as well as cryptocurrency as these gain a lot of interest from users.
To help pass reviews by Google, the attackers conjure websites that reflect what the apps are all about, making it a complete legitimate illusion that can easily users.
According to ThreatFabric, the threat actors distribute these applications within specific regions or different dates to avoid Google’s detection techniques. So far, there are four families: Anasta, Aliens, Hydra, and Ermac.
To avoid detection, the attackers distributed the apps in the following countries:
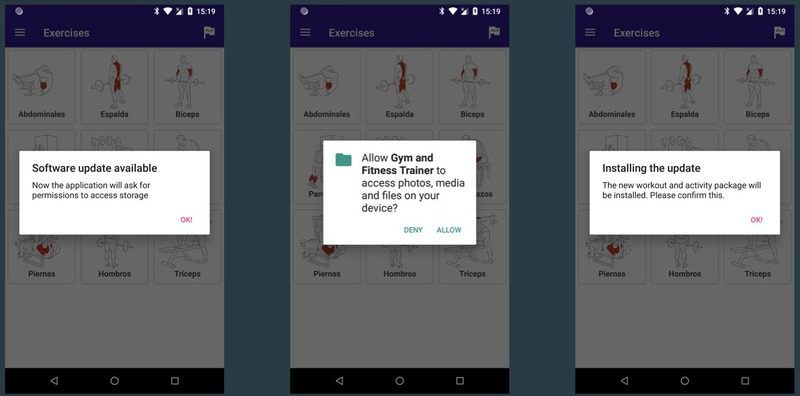
The infection process isn’t as common as the ones we’ve covered before. Instead of releasing the trojan as soon as the user installs the app, the app waits for the actor’s server to give the command.
At will, the attacker’s server informs the app to perform a fake “update.” Once installed, the app injects the malware into the Android device.
The update process is presented in the image above. As mentioned, once the installation process is complete, the malware takes root inside the victim’s device.
Into the Belly of the Beast – The Infected Apps
You can find the apps that the attackers are using in this malicious campaign in the list below:
- QR Scanner
- PDF Document Scanner – Scan to PDF
- PDF Document Scanner Free
- CryptoTracker
- Gym and Fitness Trainer
- PDF Document Scanner
- Two Factor Authenticator
- Protection Guard
- QR CreatorScanner
- Master Scanner
- QR Scanner 2021
Wait, there’s more. While not as popular as the one’s above, these apps are also distributing the banking trojans:
- QR CreatorScanner (Hydra trojan)
- Master Scanner Live (Alien trojan)
- Gym and Fitness Trainer (Alien trojan)
- QR CreatorScanner (Ermac trojan)
- PDF AI : TEXT RECOGNIZER (Anatsa trojan)
There you have it. If you have any of these apps installed, get rid of them now.
Google Play – 300,000+ Infections with Android Banking Trojan
Some users might be aware of how to avoid such malware infections, but others don’t seem to have a clue. The apps downloaded convince the target that the update is necessary for the app to work properly.
However, when the installation process begins, allowing “Downloads from Unknown Sources” is required, which is kind of shady, considering the apps are downloaded from Google Play Store.
Regardless, always make sure that the app you’re downloading has good reviews as the Android banking trojan can be anywhere. This helps a lot if you want to know how to separate the good apples from the bad ones.
Malware infection has devastating effects and dozens of types out there. And while one of the families goes by the name of Ermac, we’ll be quoting the real character from the Mortal Kombat franchise: “They are many, you are but one!” Make sure to protect yourself all the way. Stay safe.