A Contagious Attack – Punisher Ransomware Targets Chile
During the pandemic, threat actors took advantage of the chaos around the world and used COVID-19 as a hematic lure to infect users with different malware families. While such campaigns decreased in 2022, there are cyber criminals that are still on this track, particularly those who have recently utilized the Punisher ransomware.

This exact ransomware has been around for quite some time. However, according to researchers, the one used in this campaign is a new upgraded variant.
COVID-19 is the disguise and the target is Chile. The Punisher malware spreads via COVID tracking applications and locks the victims’ files. How does the process go? We’ve discussed everything below.
Punisher Ransomware – Your Files are not Safe!
As we mentioned, threat actors leveraged COVID-19 to create fake scams back in 2020. Apparently, some have remained persistent on this trick, including the Punisher ransomware.
Earlier this year, none other than Pfizer was used as a disguise to lure victims into one of the biggest recent phishing attacks. Why is it impactful? Because Pfizer has one of the most effective mRNA vaccines around the world and its name alone creates legitimacy.
In other words, users can easily fall victim to a scam that has Pfizer’s name on it. Another incident occurred with AstraZeneca.
The company was not used, but it got breached. And you can imagine the damage that cybercriminals can do with the harvested information.
Punisher, on the other hand, is lurking around within a fake website that delivers ransomware disguised as a COVID tracking application. Main targets? Chilean users.
Once the application is downloaded, the entire malicious attack begins. However, the note is personalized by adding content specific to each of its targets.
Victims will find a note in a file shortcut named “unlock your files.lnk.” Once they open it, they’ll find that the cybercriminals are demanding a $1000 Bitcoin payment for the decryption key.
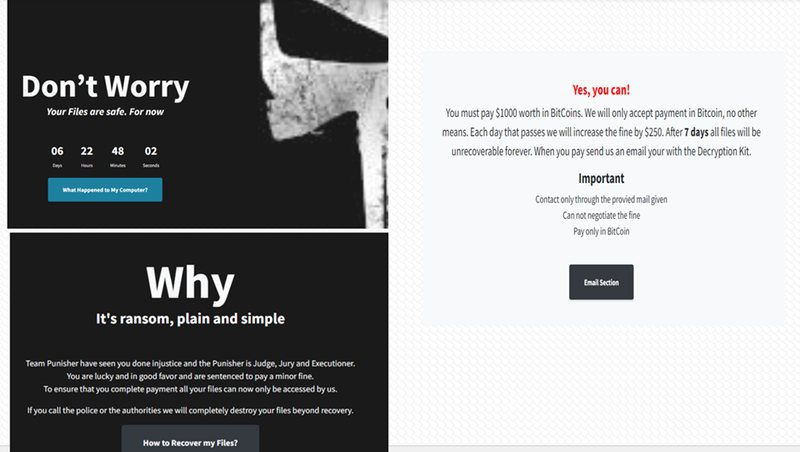
As seen in the image above, the cybercriminals’ demands are perfectly clear. Security researchers at Cyble explained the entire process in the following statement:
“After infecting a system, the ransomware appends data to ransom notes such as System ID, unique identifier of each victim, BTC address for the ransom payment, date of infection, and JavaScript codes to start the timer, which will also increase the ransom amount after a specific timeframe.”
But that’s not the end, so those who are affected should not give up hope. According to Cyble, the files encrypted by this ransomware can be easily decrypted as it uses AES-128 symmetric algorithm.
Victims Getting Ransomewarely Punished!
If you’re ever obligated to download a COVID-19 app, we highly recommend you get it from a trusted website. Not all applications from third-party websites are legit.
Just avoid such practices and you’ll be able to save yourself from such a predicament. However, that doesn’t mean you should leave your device unprotected.
Make sure you have a reputable antivirus installed. That way you can perform quick scans on a regular basis to see if anything is lurking within your systems.





