Lockheed Martin Breach – Small USB Drive, Huge Cyber Attack
They say gifts show interest, and that’s right. However, when the gift comes from cybercriminals, the interest is shown to be not in the person, but in their data. Recently, the FBI warned that financially motivated cybercriminal groups are distributing packages containing malicious USB devices to deploy ransomware.

Usually, ransomware targets big companies in hopes of making huge amounts of money, such as the incident with Delta. Now, Lockheed Martin – one of the world’s largest aerospace and defense contractors seems to have fallen victim to a similar attack.
The threat actor that goes by the name of 1941Roki breached the company and is offering the obtained data for $999. How did this happen and how much data are we talking about? Find out in this comprehensive article.
Lockheed Martin Breach – An Unwanted Gift
A couple of weeks ago, the FBI issued a warning statement about hackers targeting defense contractors and other industries with malicious USB drives.
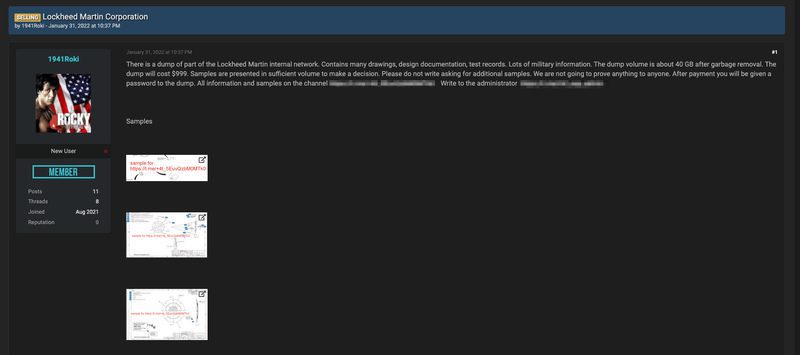
Later on, 1941Roki surfaces with a page on a popular hacking forum advertising internal documents from Lockheed Martin. The post comes with samples, in case the buyers need evidence of what they’re investing in.
Apparently, a specific client hired the group to obtain such information, but then the deal allegedly fell through. Well, that didn’t stop them. In fact, they went with the motto: “Their loss is someone else’s gain,” and offered the documents for $999 to the public.
We can clearly see the proof and documentation from this alleged hack, other past breaches, and their statement below:
“There is a dump of part of the Lockheed Martin internal network. Contains many drawings, design documentation, test records. Lots of military information. The dump volume is about 40 GB after garbage removal.
The dump will cost $999. Samples are presented in sufficient volume to make a decision. Please do not write asking for additional samples. We are not going to prove anything to anyone. After payment you will be given a password to the dump.”
Now, offering the information is one thing, and the subtlety of how the group got it is another. Apparently, the process took a lot of analysis before they executed the plan.
Take Your Gift – Give Us Your Data
They first identified who had access to technical information with no qualifications in the “information security” field.
Once they did so, they targeted them with holiday gifts in the form of USBs. Thanks to this clever approach, the threat actors were able to gather around 40 GB of internal Lockheed Martin documents, including:
- Design drawings
- Design documentation
- Test records
- Active projects (Indago 4)
- Contract details
Bleeping Computer previously reported on this trend and the FBI announced it a few weeks ago. If we’d look closer at the forum, we’ll see several posts that may relate to the incident.
We’re referring to a connection to eastern Europe as they include leaks on Russian and Ukrainian residents.
Lockheed Martin Breach – 1941Roki Strikes and Scores
Restore Privacy contacted the hacking group and they had a lot to say. You can check the entire report on their official page.
Moreover, Restore Privacy contacted Lockheed Martin for a comment on this situation, but still hasn’t received any reply.
Receiving USBs might feel nice, but it has a pretty common method to steal information. It’s not about gifts only, some hackers are dropping USBs in parking lots, waiting for the right victims to pick them up, and plug them in. Be careful.