DHL and MetaMask Phishing – One Hacked NameCheap Email Causes Cyber Havoc
So far, 2023 has seen numerous cyberattacks in the first two months of its calendar. Simply put, one hacked email can cause a lot of damage, and that’s exactly what happened recently with NameCheap. Threat actors successfully hacked the domain registrar’s email and bombarded users with a flood of MetaMask/DHL phishing emails.

Both MetaMask and DHL are huge names, and an email by any one of them can seem very legit. In other words, users can be easily fooled into submitting personal information without suspecting a thing.
Unfortunately, cybercriminals are well aware of that, and they’re using both of these companies to target their victims. What is this phishing campaign all about? What happens next? Here’s everything we know.
One Hacked NameCheap Email, A Huge Phishing Attack
Phishing attacks are simple. A threat actor impersonates a well-known company to trick users into submitting sensitive information by following a fake link within an email or SMS(Smishing).
The bigger the company is, the more successful the attack will be. For example, a while ago, cybercriminals disguised themselves as the legendary Pokemon brand to spread malware. In this particular campaign, cybercriminals made use of malvertising, social media posts, and the like.
A few months earlier, none other than cybersecurity giant, ExpressVPN was also impersonated to inject victims’ devices with the infamous RedLine Malware.
Now, a single email breach allowed threat actors to send emails in the name of DHL and MetaMask in hopes of harvesting sensitive information from numerous targets.
NameCheap’s CEO Richard Kirkendall stated that cybercriminals have compromised. Moreover, the campaign kicked off on SendGrid, an email platform used by NameCheap to send notices. Unfortunately, the Tweet was deleted, so we couldn’t include it here.
As we mentioned, the phishing campaign impersonates either DHL or MetaMask. In DHL’s case, it’s a notice that customers should pay a certain delivery fee in order to complete the process.
Within the email, the threat actors included links created specifically to redirect users to fake pages where they enter their personal information.

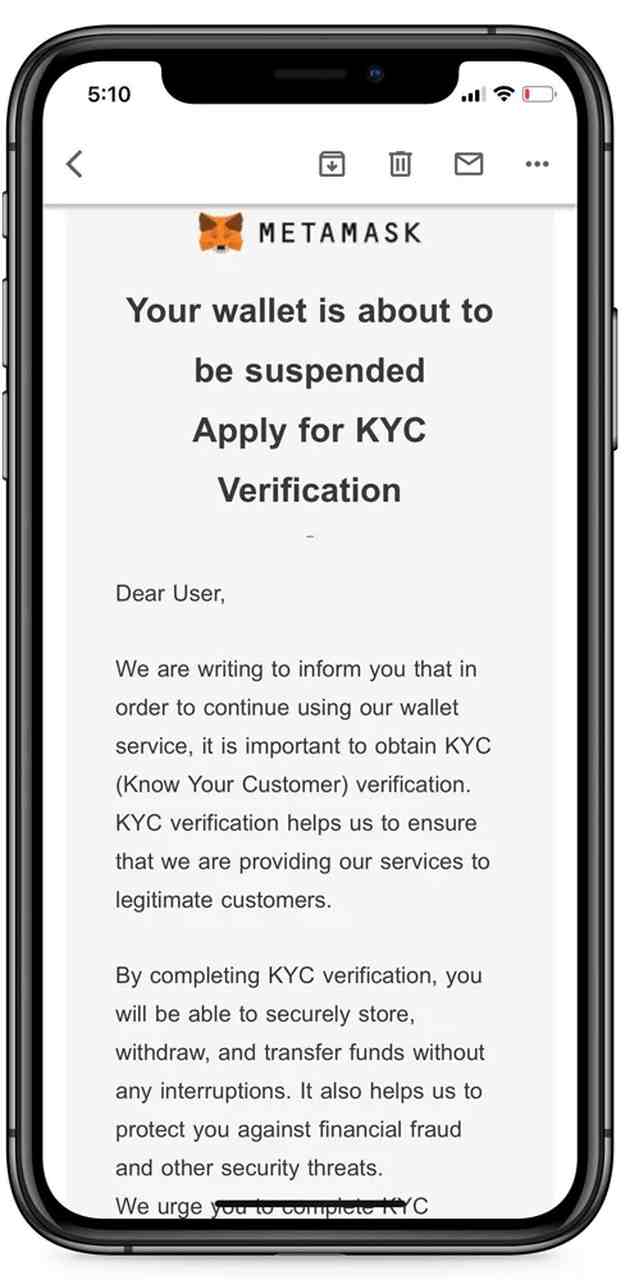
As for MetaMask’s trick, it comes in the form of KYC (Know Your Customer) verification. Since the main objective of this feature is to prevent the suspension of users’ wallets, we all know what kind of information is due to be submitted.
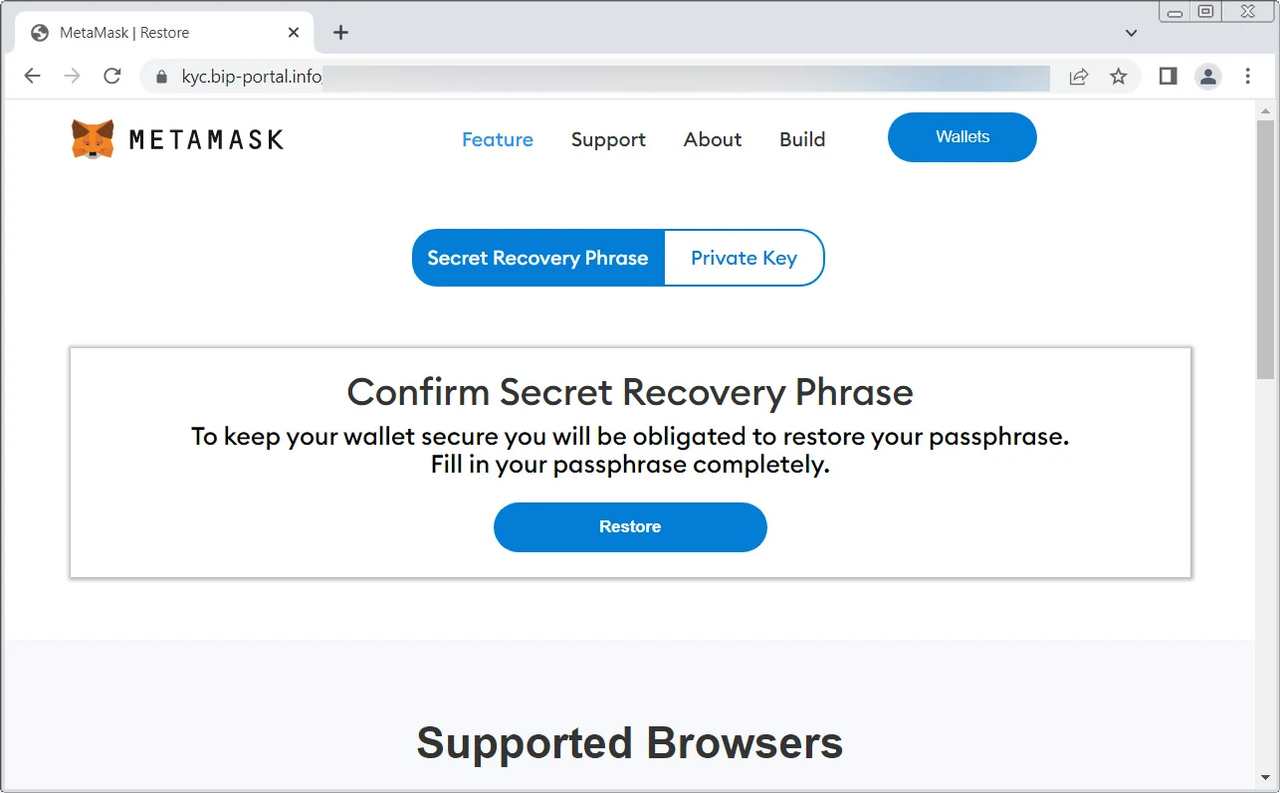
The MetaMask email provides a link from Namecheap that takes the victims to a phishing page pretending to be MetaMask, of course. Once there, users are prompted to enter their “Secret Recovery Phrase” or “Private key.”
Once the victim submits the key, the threat actors can import the wallet and siphon all the funds and assets in an instant.
A NameCheap Breach Doesn’t Come Cheap
When it comes to stopping phishing campaigns in their tracks, victims should always stay vigilant while handling received emails. No matter what company sends you an email, don’t click on the link provided within it.
To stay on the safe side, visit the official website manually. That way, you’ll be certain that no fake page lies ahead. Protecting your sensitive information is crucial. Don’t take it lightly, and stay safe.





