AbstractEmu Android Malware Resurfaces – Device Rooting Activated
Android is now the world’s most commonly used platform and is used by many different phone manufacturers. However, recently, Android devices have become a popular target for malware, spyware, as well as trojans.
Android allows you to download and install apps from nearly any source. Convenient? Yes. Secure? not quite. Recently, new Android malware surfaced infecting devices and rooting them to take complete control and silently tweak system settings.
The malware was distributed through various stores, including Google Play, Amazon Store, Aptoide, and APKPure. What is this malware? What data does it harvest? Find out in this article.
Inject and Harvest – Enter AbstractEmu
Android mobiles have suffered their fair share of malware throughout the years. The recent one would be AbstractEmu, nicknamed by Lookout Threat Labs security researchers who found it.
According to their report, the malware is bundled with 19 utility apps distributed through official stores and several other third-party ones.
Most of the apps that are bundling the malware are password managers, data savers, as well as app launchers. Unfortunately, the malware distributors knew what they were doing so they managed to avoid detection.
In fact, the infected apps were fully functional. They did exactly what they promised to avoid triggering suspicion. And boy did they succeed at first by harnessing more than 10,000 downloads on Google Play.
The apps are downloaded for a reason, which means that the user will activate them as soon as they’re installed on the device, making the malware infection process easier.
Once installed, AbstractEmu will start harvesting and sending system information to Command and Control (C2) server as it waits for further commands.
So, what does the malware collect in terms of system information? Check the list below:
- Manufacturer, model, version, and serial number.
- The package name of the app.
- Status of permissions/capabilities granted to the app.
- Mac address.
- IP address.
- SIM information (carrier name, IMEI/device ID, and number).
- Account information.
- Root status.
- Command numbers that are supported by the app.
- Timezone.
- Package name of installer of the app.
As you can see in the list above, all the information that the malware collects can easily identify any user. It can also easily pinpoint the user’s location since it already harvested the IP address of the device.
How Are They Doing This?
The attackers have a lot to gain, and you Android users have a lot to lose or risk exposing. But how are they doing this? What are the commands they’re using?
With so many tools at their disposal, the attackers can easily infect the device. For example, they’re using CVE-2020-0041, a bug never exploited by Android applications before.
Another tool would be CVE-2020-0069. This one targets the MediaTek Chips, which are used by dozens of smartphone makers. Not to mention their ability to exploit CVE-2019-2215 and CVE-2020-0041 adding more risk to the mix.
Apparently, these activities are new and evolved. According to Lookout researchers:
“This is an important discovery because widely distributed malware with root capabilities has become scarce over the past five years,” Lookout researchers said. By using the rooting process to gain privileged access to the Android operating system, the threat actor can silently grant themselves dangerous permissions or install additional malware, steps that would normally require user interaction.”
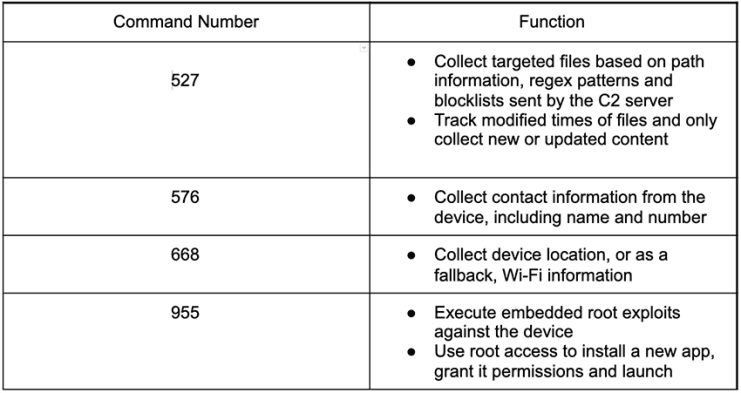
AbstractEmu waits for commands from its C2 server in order to begin its malicious actions. We’ve included an image below showing what each command does:
As you can see, every command has a different purpose. However, there’s one thing they have in common – full control over your device.
Aside from harvesting data and gaining complete control over apps, the researchers added that AbstractEmu can obtain elevated privileges which also allow malware to access sensitive data from other applications, which is not possible under normal circumstances.
AbstractEmu – The Ostrich is All Up in Your Business
Even if the malware is rare, you should always take proper precautions to protect your device. One of the basic steps to do so is to keep your OS up to date.
Other than that, make sure to have a solid antivirus tool. It’ll fend off any malware infection that might occur. AbstractEmu is not a joke, nor is your private information. Keep a keen eye on the applications you install to avoid such predicaments.