Apple At It Again: In with 3 New Zero-Day Vulnerabilities
When we speak of Apple, we directly acknowledge how safe the company’s devices are. With extra security features and the inability to download content from untrusted sources, users are well-protected. However, when the manufacturer itself slips up, things tend to go south pretty quickly. That’s right! New Apple flaws are at hand.

The company had a rough year back in 2022, as its devices encountered over nine vulnerabilities that allowed malicious practices. Now, three new ones emerged, giving hackers the opportunity to hack iPhones, Macs, and iPads if they exploit them.
These flaws are limited to the multi-platform WebKit browser engine, but they pose a real threat to the device’s security. What can threat actors do with these vulnerabilities? How is Apple handling this? Find out below.
Another Vulnerability – Detect, Exploit, Hack
As we mentioned, Apple is no stranger to major flaws and vulnerabilities. A while back, the company disclosed a flaw that allowed malicious actors to damage and disrupt iPhones and iPads’ functionalities.
After that came CVE-2023-28205 and CVE-2023-28206, these vulnerabilities led to the corruption of valid data and the execution of arbitrary code with kernel privileges.
Well, yeah! Apple did not have a good 2022 as more than 9 vulnerabilities saw the light throughout the year. Not to mention that one incident where Apple seemed to be spying on us?
We’re referring to that one time when macOS contained network-based spyware that’s always on even when all Apple services are disabled.
Now, Apple is in the spotlight again as three new vulnerabilities have surfaced, risking data exposure and full control of its users’ devices.
The vulnerabilities are tracked as CVE-2023-32409, CVE-2023-28204, and CVE-2023-32373. They’re all within the multi-platform WebKit browser engine.
The Exploitation Predicament
If exploited, threat actors can easily hack into iPhones, Macs, and iPads. To be exact, here are the devices affected by these vulnerabilities. Please note that the bug affects older and newer models, including:
- iPad Pro (all models), iPad Air 3rd generation and later, iPad 5th generation and later, and iPad mini 5th generation and later
- iPhone 6s (all models), iPhone 7 (all models), iPhone SE (1st generation), iPad Air 2, iPad mini (4th generation), iPod touch (7th generation), and iPhone 8 and later
- Apple TV 4K (all models) and Apple TV HD
- Macs running macOS Big Sur, Monterey, and Ventura
- Apple Watch Series 4 and later
CVE-2023-32409 allows remote attackers to break out of Web Content sandboxes. On the other hand, the other two vulnerabilities enable threat actors to access sensitive information on the device.
Not only that, but they also allow them to achieve arbitrary code execution on compromised devices.
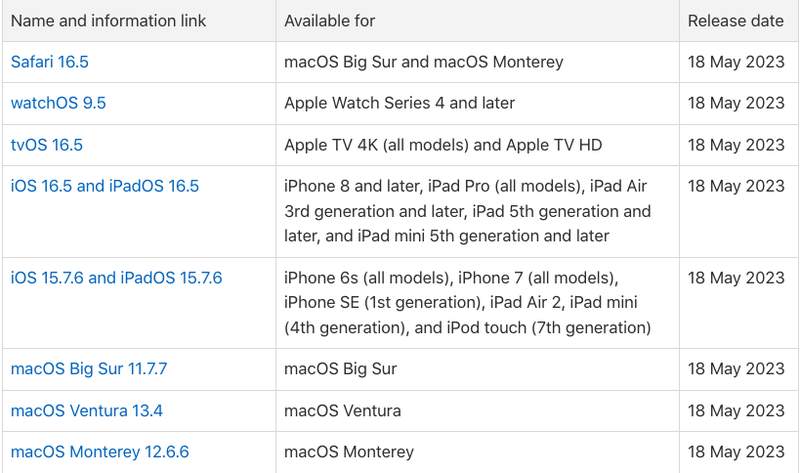
Apple released fixes to the bugs on all the affected devices. The company advises its users to update their software immediately to prevent any future problems with these flaws.
Another Apple Flaw – Update Now
Apple is a very secure brand of devices, but vulnerabilities are inevitable. The most important thing is that when the company rolls out updates, you should immediately implement them.
Keeping your devices up to date is one of the most important things you can do to maintain your security and privacy. Do that, and you’ll be just fine.





