Facebook Phishing Campaign – Using Messenger to Harness Millions
Phishing attacks are getting more popular every day as threat actors figure out new ways to commit their malicious practices. Usually, such campaigns spread through push notifications, promo pop-ups, and malvertising. However, with this new campaign discovered by PIXM, a New York-based AI-focused cybersecurity firm, the attackers are abusing Facebook and Messenger to lure millions of users to phishing pages.

While this is not the first time threat actors have used Facebook for such attacks, this campaign seems to be going on a grand scale.
It was discovered recently as it peaked in April-May 2022, but unfortunately, it has been around since late 2021. Now, what are these attackers after? How are they performing these attacks? Make sure to give this comprehensive article a quick read.
Facebook Phishing Campaign – Talk About a large-scale Scam
Facebook itself is not the safest place to be browsing, it does have its flaws, especially when it comes to handling its users’ data. Not only that, but until now, we can’t forget about the massive account exposure that occurred a few years back.
Regardless, Facebook remains one of the biggest and strongest social media entities in the world, harnessing over 2.936 billion worldwide users a month.
This number is great for Facebook, but apparently, it also poses a beneficial opportunity for threat actors. Now, a new phishing campaign is targeting millions of Facebook users through the social media platform itself or its Messenger feature.
Basically, just like most phishing attacks, the threat actors lure their victims into clicking on some sort of link, redirect them to a fake page, and trick them into entering their account credentials and seeing advertisements.
We all know what happens here. The threat actors harvest the credentials and start their malicious practices.
Peaked Twice, Doubled in Size
The research lab PIXM managed to discover the campaign, but little too late. The only reason they were able to do so is due to the fact that the attack peaked in April-May 2022. However, it has been around since September 2021.
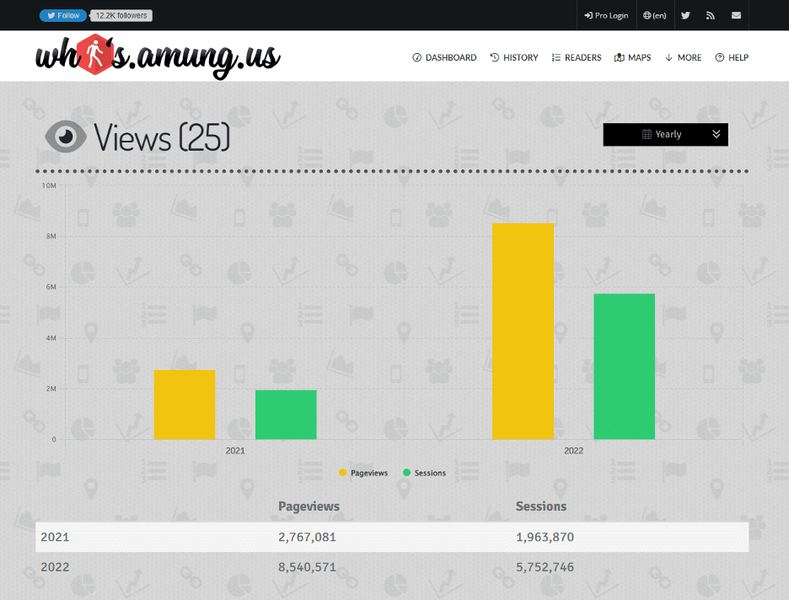
The peak isn’t the only hint PIXM needed to discover the attack. In fact, the researchers were able to trace the threat actor as one of their phishing monitoring apps (whos.amung.us) was publicly accessible with no authentication needed. (The image above showcases that)
To further spread the attack, the threat actors focus on contacting the victims’ friends once they have their credentials. In other words, the more they steal, the bigger the attack is:
“A user’s account would be compromised and, in a likely automated fashion, the threat actor would log in to that account and send out the link to the user’s friends via Facebook Messenger,”
Tou might ask: Where are Facebook’s security measures in all of this equation? Oh, they’re there alright, but the threat actors are outsmarting them.
Facebook can stop the dissemination of phishing URLs. So, the attackers used legitimate URL generation services such as “amaze.co,” “famous.co,” and “funnel-preview.com.”
In other words, Facebook won’t block these as legitimate apps use them. Sneaky! It gets worse, unfortunately. The researchers also found 405 unique usernames under this campaign.
Not only that, but they all operate using separate Facebook pages. Talk about determination. One of these pages has as high as 6 million page views.
New Facebook Phishing Campaign – Click Me, Give Me
PIXM really dug deep into this, even identifying one of the threat actors. They found a reference to a website that has been seized and is part of an investigation against a Colombian man.
He goes by the name of Rafael Dorado, but they still don’t know who seized the website or issued the notice. Simply put, phishing campaigns are growing every day.
You have to protect yourself. Just stay vigilant all the time and never click on random links. You never know who’s behind everything, waiting for the right moment to snatch your data.





