AvosLocker Ransomware – New Variant, Same Old Cyber Threat
Ransomware is very dangerous regardless of how important the target is. Big or small, the impact left by ransomware is huge. Now, imagine if new ransomware attacks are targeting critical infrastructure in the U.S., including financial services and government facilities! This has been the case recently as a new variant of the AvosLocker is in action.
A while ago, Russia managed to arrest several members belonging to the notorious REvil ransomware gang and neutralize its operations. Now, something has to fill the game and this newer ransomware family felt like it should carry the torch.
According to cybersecurity researchers, this ransomware comes with many capabilities, including disabling antivirus solutions. How big is this campaign? How does the ransomware operate? Find out below.
AvosLocker Ransomware – Antivirus Solutions No More
Ransomeware has become a very popular attack type for hackers to gain millions from big companies. Not long ago, the group behind the Conti ransomware targeted none other than KP Snacks.
Now, AvosLocker is following such attacks with one of its own, but with a twist. Apparently, the group behind the malware has come up with new ways to evade network securities, even if an antivirus is in place.
AvosLocker uses a legitimate driver file to disable anti-virus tools and evade any detention mechanisms. Past attempts by this malware followed the same algorithm.
However, this is the first time AvosLocker kicks it up a notch and targets high-profile entities such as US financial services and government facilities.
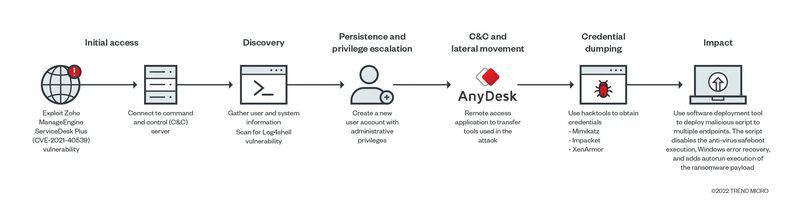
As mentioned, the new variant can easily disable any defense solution using a legitimate Avast Anti-Rootkit Driver file (asWarPot.sys). Not to mention that it’s also able to scan In addition, the ransomware multiple endpoints for the Log4j vulnerability Log4shell using Nmap NSE script.
Yeah, the Log4j vulnerability is still an issue even now. According to researchers at Trend Micro:
“There are some indications that they abused the same vulnerability previously documented by Synacktiv during a pentest, CVE-2021-40539. The gap we observed was particularly similar to the creation of JSP files (test.jsp), execution of keytool.exe with “null” parameters to run a crafted Java class/code.”
The researchers also added that the HTA executed an obfuscated PowerShell script that contains a shellcode. This has the capability to connect back to the [command-and-control] server and execute arbitrary commands.
And finally, to add more devastating results, the malware is also capable of modifying other details of the installed security solutions. One of them is the ability to disable legal notices.
AvosLocker: One Key Only – Pay Your Ransom
The new variant of the AvosLocker ransomware is a lot more dangerous than the ones that came before. It’s now targeting high-profile US facilities.
With the ability to disable antivirus solutions to evade detection after breaching target networks by taking advantage of unpatched security flaws.
Ransomware attacks are on the rise. Don’t ever think that you’re safe just because you are not a high-profile target. Anyone is a victim, so always take proper precautions when it comes to your online security.