Banking Data At Risk: Anatsa Trojan Invades Google Play Store
When it comes to downloading applications, it’s always recommended to do so via a trusted source. For Android users, that’s none other than Google Play Store. Unfortunately, the Android App library has seen better days, as multiple malware infiltrations have occurred recently. The latest one would be the invasion of a dangerous banking trojan called Anatsa.

With over 30,000 installations, we can deduce how big of an impact this campaign can have. The threat actors behind this are quite consistent and very capable.
Google removed several apps with the same malicious activity in the past. However, the actors came back with an elevated one to target even more users. How is this campaign spreading? What is at risk? We explained everything below.
Google Play at It Again – Anatsa with 30K Downloads
Android users have been battling malware attacks for a long time now. The worst part about this is that the campaigns are coming from Google Play – the safest place where Android operators can download their apps from.
Cybersecurity is evolving, and so are the threat actors’ methods and capabilities. That’s why their able to infiltrate Play Store regularly.
In fact, it has only been a week since Google Play was seen hosting apps embedded with Spyware thanks to DoNot APT.
Android users were targeted by Anasta in the past. Back in 2021, a similar campaign saw threat actors spreading the banking trojan via fitness tracker apps, PDF scanners, QR code scanners, and Adobe Illustrator apps.
Now, they decided to stick to their theme by also using the office/productivity category. They’re targeting users via PDF viewer and editor apps and office suites.
According to Threat Fabric, the cybersecurity firm has previously reported similar incidents to Google. As a result, the malicious applications were removed on the spot.
However, every time Google removes such apps, the threat actors would return to upload a different dropper with a new disguise.
Apparently, the attackers would submit the app to Google Play in clean form and then update them with malicious code at a later date.
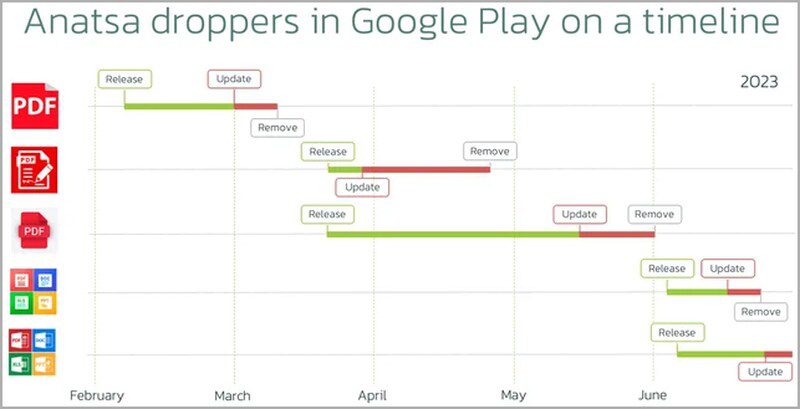
As seen in the image above, the threat actors take their time before they update their applications with malicious droppers.
Also, it takes time for Google to identify them as a threat to remove them. The damage could be done by then.
What Can the Android Trojan Do?
Now the most important question is: What can Anatsa do once it takes root inside the device? Basically, the banking trojan harvests financial information.
That includes bank payment information, account credentials, and credit card details. Using keylogging and overlaying phishing pages, Anatsa can easily siphon everything submitted.
According to the report by Threat Fabric, the banking trojan targets 600 financial apps of banking institutions from around the world.
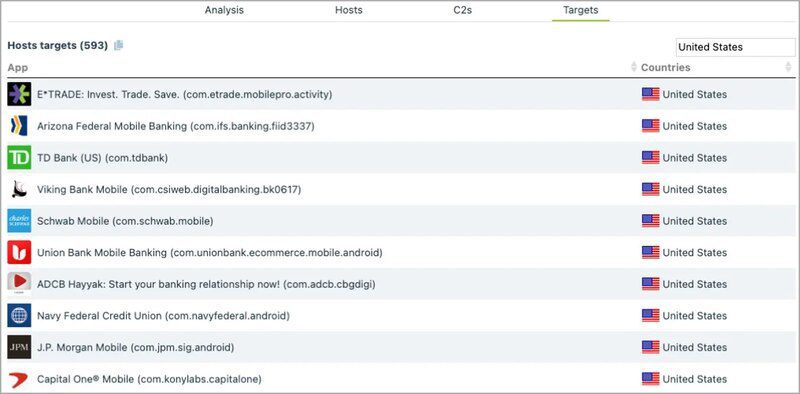
Most of these banking applications belong to institutions in the US. However, the campaign is much bigger than that.
Anatsa targets online banking customers in the U.S., the U.K., Germany, Austria, and Switzerland. If you think you’ve fallen victim to Anatsa, delete any suspicious application immediately.
Once that is done, run a full device scan to determine if there’s any malware residue lurking around.
If Anatsa is on your device, it can perform transactions on your behalf, automating the money-stealing process for its operators.
Money-Stealing at Its Best
Anatsa is very dangerous. The banking anti-fraud systems could have a challenge detecting this as the transactions are made from the same device that the victims regularly use.
Whenever you want to download anything, make sure to download it directly through Google Play. Don’t depend on search engines, as malvertising has been taking over recently.
Also, even if it’s through Play Store, give the review section a thorough read. That way, you can make sure that the desired app works as intended and that no one has any problem with it.





