Horabot Emerges – A Phishing Campaign Targeting Gmail and Outlook Accounts
Phishing campaigns have become a common tactic among cybercriminals to infiltrate their victims’ devices. An email that leads to malware infection – it’s a pretty basic process. However, when malware such as Horabot is capable of taking control of the victim’s Gmail and Outlook accounts, the end results can be drastic.

Phishing allows the threat actors to achieve a lot. And with compromised email accounts, they can spread their campaign even further using the contact information they harvested.
Horabot allows them to do that once it takes root within a device. But does it do that? How are the threat actors, who are believed to be of Brazilian origins, implementing this campaign? Make sure to check all the details in the following article.
A Horabot Attack – Latin American Users Beware!
When it comes to phishing attacks, that initial “Email” lure is the most important step for cybercriminals. Everything after that will fold on its own.
It takes a lot of social engineering capabilities to convince victims to click links and download fake files, but unfortunately, it’s not that hard to trick them.
The aim is to infect the device with malware, which can vary in terms of family, risk, and malicious capabilities.
While most of them tend to harvest sensitive information or encrypt the victims’ files, Horabot targets users’ Gmail, Outlook, Hotmail, or Yahoo email accounts. According to Cisco Talos researcher Chetan Raghuprasad:
“Horabot enables the threat actor to control the victim’s Outlook mailbox, exfiltrate contacts’ email addresses, and send phishing emails with malicious HTML attachments to all addresses in the victim’s mailbox.”
So here’s how it goes! Just like any phishing email, there’s a link the victims’ have to click on. It’s masquerading as some sort of tax that needs to be paid.
Once they click on the link, which is supposedly a payment receipt, it’ll redirect them to a fake website hosted on an attacker-controlled AWS instance.
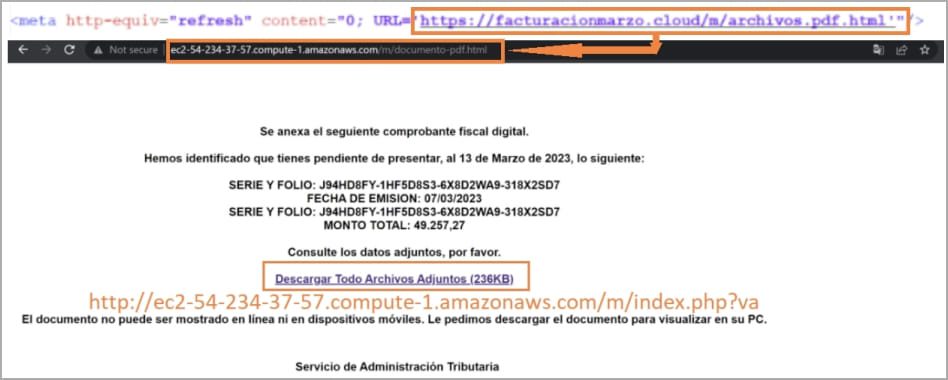
Another link is provided on the website, which upon being clicked on, downloads a RAR archive that contains a batch file with a CMD extension.
After that, this extension downloads a new PowerShell script that retrieves trojan DLLs and various other executables from the C2 server.
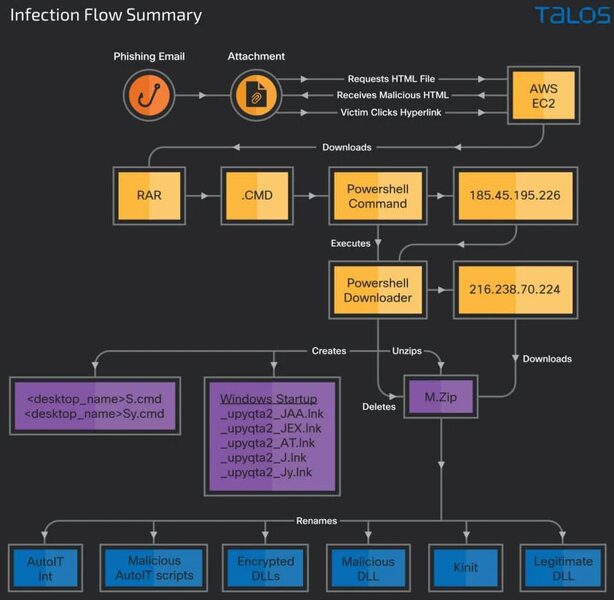
The process continues as the Trojans fetch the final payloads for the attack. The first one would be the PowerShell downloader script, and the other is the star of the campaign – Horabot.
According to the cybersecurity firm, most infections are taking place within Mexico, with limited victims identified in Uruguay, Brazil, Venezuela, Argentina, Guatemala, and Panama.
The threat actor behind the campaign is supposedly residing in Brazil. Based on the report, the attack seems to be targeting specific sectors, including accounting, construction/engineering, wholesale distribution, and investment verticals.
One important feature researchers pointed out was that the malware also fetches a banking trojan written in Delphi.
If it takes root within the device, it can harvest system info (OS version, IP address, etc…), user credentials, and activity data.
One Malware, Dozens of Possibilities
Horabot is a very dangerous malware to infect your devices. Once it compromises an account, it can use it to spread its activity to everyone on the contact list.
In other words, the campaign never stops as it continues to hop through various accounts – and the cycle never ends.
The malware spreads through phishing emails, which means you can put an end to the attack before it even begins.
All you have to do is avoid clicking the links in the emails. If you think that your bank sent you this, you can visit its official website manually.
You don’t have to take the faster route. If it’s faster, it can also be malicious. Stay safe.





