The Lazarus Effect 3: BloxHolder’s Fake Crypto App
The North Korea-sponsored APT group “Lazarus” needs no introduction. By now, and based on their malicious activities, everyone should be acquainted with the name. The threat actors have been wreaking havoc among companies such as Lockheed Martin and all the way to the crypto market.

Now, Lazarus has come up with a new scheme to deploy the previously undocumented version of the AppleJeus malware and steal its victims’ cryptocurrency.
This time around, the group is using fake applications under a made-up brand called “BloxHolder.” How is the group implementing its tactics? What is AppleJeus? Here’s everything we know.
Lazarus Strikes Again – Fake Crypto Apps Everywhere!
Lazarus is one of the oldest active cybercriminals groups. Also tracked as ZINC, this North Korean hacking group is pretty capable, especially when it comes to harvesting cryptocurrency.
Targeting victims’ crypto has become very popular among threat actors. The methods might vary, but the end results are the same.
Some hackers use phishing, and others exploit present vulnerabilities in systems. Lazarus takes advantage of all the aforementioned, but this time, they’re resorting to fake applications.
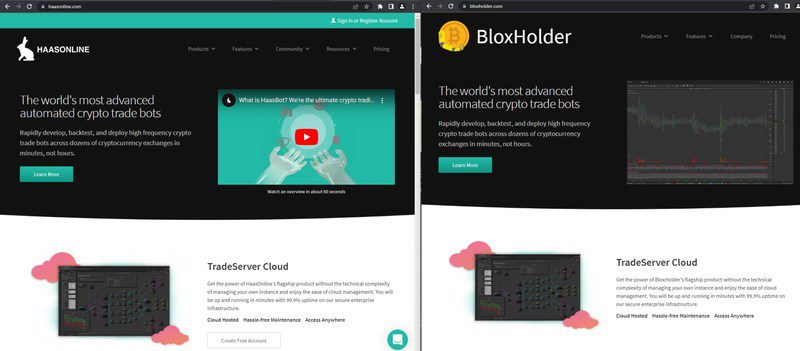
AppleJeus has been around since 2018, but the group has upgraded it since. The group is using a phishing tactic by leading users to a fake website that goes by the name of BloxHolder.
The website promotes itself as a place for automated cryptocurrency trading. In reality, it’s a clone of a legit website – HaasOnline. You can check the similarity in the following images:
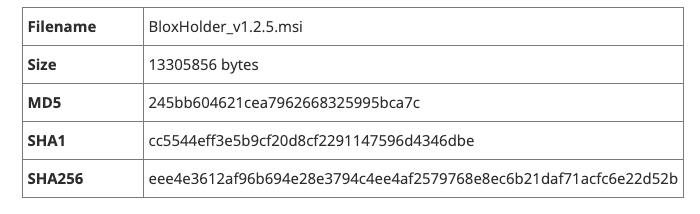
According to Volexity, the malware is embedded within a Microsoft Installation file. The users are prompted to download the BloxHolder application. That’s when all the malicious activities occur. Here’s what the firm’s statement had to say:
“Volexity discovered the fraudulent BloxHolder website after identifying a new AppleJeus malware sample that was bundled as part of a Microsoft Installation (MSI) file.
This discovered file, the “BloxHolder application”, is actually another case of AppleJeus being installed alongside the open-source cryptocurrency trading application QTBitcoinTrader that is available on GitHub.
This same legitimate application has previously been used by the Lazarus Group, as documented in this report from CISA. The MSI file is used to install both the malicious and legitimate applications at the same time.”
Once the AppleJeus malware sets root on the infected device, it can harvest information about the targeted system as well as download shellcode from a C2 server. For the full technical analysis, make sure to check the study conducted by Veloxity.
Lazarus is Back – A Very Sour AppleJeus
The fake website includes a 12.7MB Windows MSI installer that installs the infected BloxHolder app. This campaign is as dangerous as they come, especially since Lazarus is behind it.
Unfortunately, this particular group is persistent, which explains its long run in the industry. Lazarus is after your information as well as your cryptocurrency.
We highly recommend double-checking the website you’re visiting before downloading any of the provided content. You never know what the website could be hosting.