The Lazarus Group Effect – Lockheed Martin Phishing Scam
The internet is advancing, we can’t deny it. However, as it reaches new levels, threat actors are coming up with new ways to target their victims. Unfortunately, most of these new techniques involve phishing campaigns and ransomware.

Recently, groups that are generally financially motivated have been responsible for major attacks such as the one that hit Lockheed Martin. Now, the companies name is back to the mix, but as an impersonating operation targeting job applicants.
Back in 2020, Lockheed Martin generated over $65.4 billion in sales, which makes it the perfect entity to disguise as and fool highly-motivated candidates. Now, who is behind this new attack? What are their intentions? Find out everything below.
Lockheed Martin Phishing Attack – The Malicious Job Offer
Lockheed Martin is probably the biggest company that specializes in mission systems, aeronautics, military technology, and space exploration.
Recently, the threat actor, 1941Roki, breached the company and offered the obtained data for $999 on a personal domain. Now, the company’s name is back, but as a method to trick new victims.
According to Qualys Senior Engineer of Threat Research Akshat Pradhan, the threat actors are none other than Lazarus. Apparently, the group is using the company’s reputation to targets phishing documents pretending to offer employment opportunities.
Here’s what he said in the statement:
Qualys Threat Research has identified a new Lazarus campaign using employment phishing lures targeting the defence sector.
The identified variants target job applicants for Lockheed Martin. This blog details the markers of this campaign, including macro content, campaign flow and phishing themes of our identified variants and older variants that have been attributed to Lazarus by other vendors.
Lazarus sends job applicants two kinds of documents:
- Lockheed_Martin_JobOpportunities.docx
- Salary_Lockheed_Martin_job_opportunities_confidential.doc.
We’ve presented an example of one of them below:
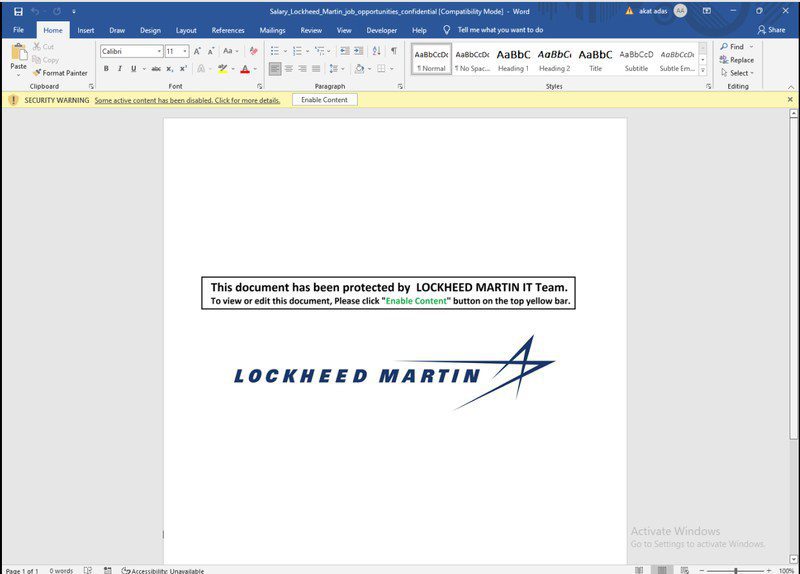
An email from Lockheed Martin would mean so much to individuals as it’s a perfect opportunity for the future. That’s why it’s easy to trick them with such an impersonation tactic.
Unfortunately, what victims think is a dream come true actually contains malicious macros that directly infiltrate their device.
The Malicious Act – Inside the Lazarus Pit
Once in, they trigger shellcode to hijack control flow, retrieve decoy documents, and create scheduled tasks for persistence. It doesn’t end here.
The malware can cause serious damage, especially since it abuses Living Off the Land Binaries (LOLBins). With those, it can compromise a lot more within the target’s machine.
However, there’s one thing that the researchers find weird. Apparently, Lazarus seems to have not perfected the scripts.
Why? Well, when they attempt to pull in a further payload, nothing comes out but an error. Therefore, Qualys could not and cannot confirm what the final malware package existed to achieve.
Lockheed Martin Phishing Attack – A Perfect Selection for Perfect Deception
Such phishing attacks are increasing day by day. Threat actors are impersonating big companies to lure clueless victims into their traps.
The Lazarus group has proved how dangerous it is when it comes to cybercrime. In fact, Outpost24’s Blueliv cybersecurity team has named Lazarus, Cobalt, and FIN7 as the most dangerous groups that target the financial industry today.
Lockheed Martin didn’t just standstill. They do state that they remain confident in the integrity of their robust, multi-layered information systems and data security.
Well, the attack later that day does prove that there are some flaws. However, the company is doing its best not to fall for that again.
As for you guys, you should always be careful. While big companies may pose as better targets, you’re not in the safe zone. Cybercriminals don’t differentiate if they find the data useful. Stay safe.





