Aurora Stealer is Back – A Fake Windows Security Update Scheme
Browsing the web is a daily habit for almost anyone out there with an internet connection. Some websites are very smooth to surf, while others bombard the users with ads and popups every now and then. However, as some are innocent, others can be one click away from dropping malware. That’s exactly the case now, as the Aurora stealer is back, targeting Windows users with fake popups.

Utilizing advertisements to deliver malware is called malvertising. It’s a common tactic among cybercriminals, as they pose as an easy way to trick users into doing their bidding.
Whether it is from ads on search engine results pages or via popular websites, Aurora is here, and it comes with risky capabilities. We’ll shed more light on the matter in the following article.
Update Your Windows Security – Malvertising on the Rise
When it comes to cybercrime, threat actors are not just sitting around using the same techniques over and over again to infiltrate their victims’ systems.
To guarantee higher success rates, they have to elevate what they already have, as it might be outdated or already solved in any way.
Malvertising is pretty common among cybercriminals since they can promise their victims things they might be urging for.
For example, a while back, those who searched for Youtube on Google were met with results at the top of their screens that redirected them to Youtube’s website.
Unfortunately, that wasn’t the case, as this was a malicious URL created and boosted by the threat actors disguising themselves as Windows Defender support.
The final part of the scheme prompts the victims to purchase a support license, and all the entered data would then be harvested by the threat actors.
Now, a new threat is looming on the internet, where malicious ads are redirecting users to what looks like a Windows security update.
To be honest, the group behind this campaign has put a lot of work into this. When the victim lands on the page, it’ll display a full-screen animation that replicates one Microsoft could have created.
Invalid Loader Dropping Aurora
This particular campaign is targeting adult traffic and tricking victims into thinking that their device needs some sort of security update.
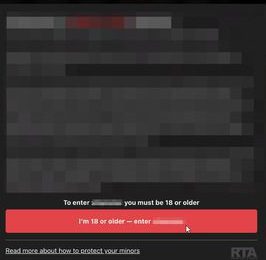
Normally, when a user clicks on the “I’m 18 or older button,” they are redirected to the website. However, in this case, a fake system update hijacks the screen.
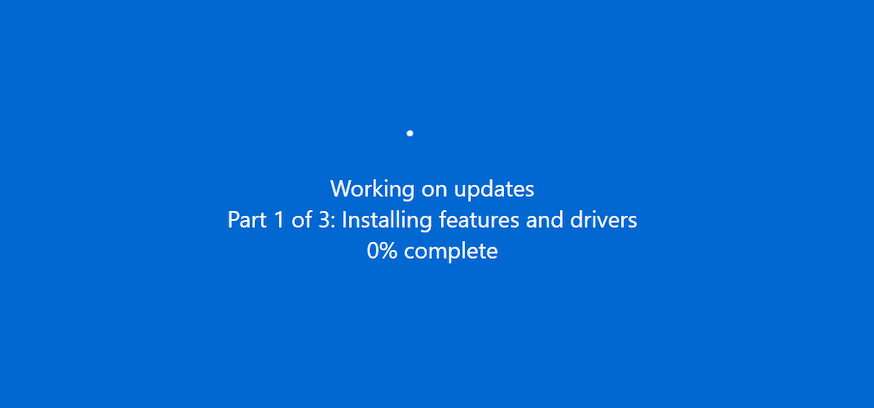
When an update is taking place, the entire device will stop operating until it finalizes. This scheme is very convincing, but it doesn’t come without flaws.
To the normal eye, the device is updating. To security researchers, it’s definitely fake due to the fact that that’s not an update page; it’s a web browser window in full screen.
If the user manages to minimize it, they’ll notice that it’s downloading the update file ChromeUpdate.exe.
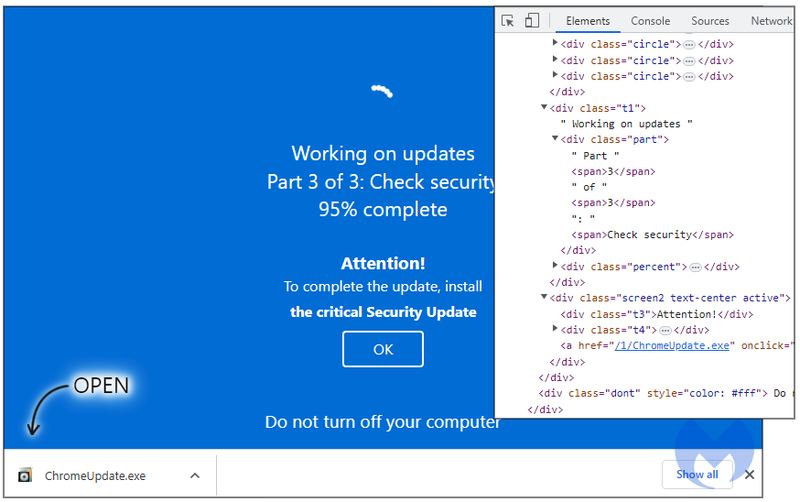
In the end, the Invalid Printer Loader drops the infamous Aurora stealer. This particular loader has a lot of capabilities, and one of them is bypassing security products.
Malwarebytes believes that a single threat actor is doing all of this. This malware author seems to take a very high interest in creating FUD malware.
The threat actor operates the same submitter profile on VirusTotal and has several videos that hype the cities and landscapes of Russia. So, basically, we have to assume that the group is definitely Russian.
Malvertising with a Loader Twist
Malvertising poses a huge threat to internet surfers. Anyone could fall victim to these schemes as they seem very legitimate.
Threat actors even pay a lot of money to appear at the top of the search results. This shows how far they’re willing to go to achieve their goals.
Fake promises can lead to devastating results. If you cherish your online privacy and sensitive information, you have to remain vigilant all the time.
Make sure to check the website you’re visiting, and never click on a button that seems shady in any way. Stay safe!





