Google Ads Abused Once Again – LOBSHOT Malware Takes Over
Throughout the years, threat actors have found many ways to trick victims and lure them to download malware from fake sources. One of these methods would be leveraging Google Ads to promote fake websites where the users download malware onto their systems. This mechanism is now being used once more to spread the LOBSHOT malware.

This particular infection chain campaign targets users searching for legitimate software downloads on Google. Cybercriminals are well aware of this, which is why they take advantage of it.
LOBSHOT has a lot of capabilities, but it’s particularly used for financial purposes. How are the threat actors spreading the malware? What risks does it pose to Google users? Find out in the following article.
A Google Ads Scam – Fake Apps, Legit Malware
As we mentioned, Google Ads have been used in the past for various malicious practices. Fake apps and services are the perfect lures, especially if cybercriminals took the take to perfect the scam.
When users search for a specific application on Google, and it pops up on top of the search result, they’ll immediately select it. This is a basic instinct.
However, threat actors have elevated their techniques, allowing themselves to hijack these searches and appear first in Google’s search mechanism.
A normal user won’t be able to differentiate between fake and real, and he/she will fall for the scam once they visit the URL. Once they download the file on the page, malware will infect their device.
That’s exactly how this particular campaign is being implemented. The full infection chain can be seen in the following image:
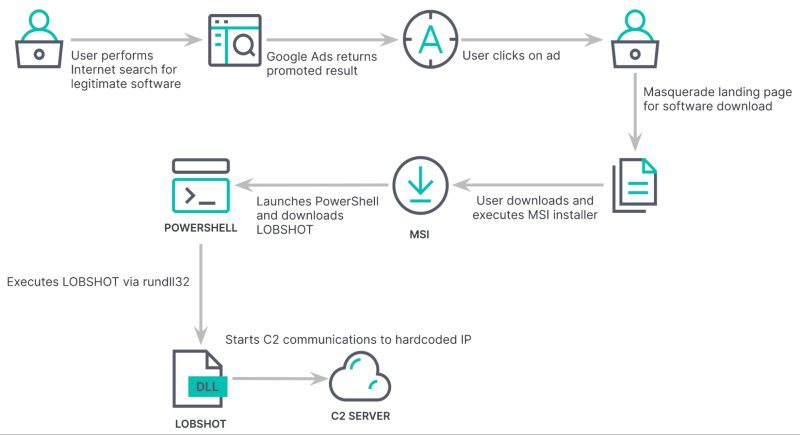
According to a study by Elastic Security Labs, researchers state that this attack resembles previous incidents with TA505, the well-known cybercriminal group associated with Dridex, Locky, and Necurs campaigns.
Basically, this malware is distributed through fake applications promoted via Google Ads. So the targets are those who are searching for official apps to download on Google.
The LOBSHOT Infection Process
Earlier this year, LOBSHOT roamed Google using fake ads impersonating AnyDesk. As seen below, the URL shows up first in the search results:
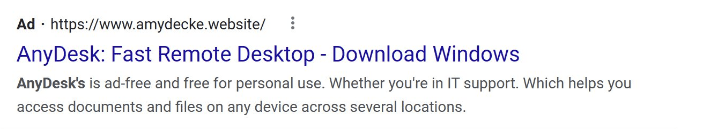
When the users click on this ad, it’ll redirect them to a fake webpage that looks very legit it can fool anyone.
Finally, once the victims download and install the “Fake” application, the LOBSHOT takes root within their device and begins its malicious activities. Those include:
Targeting 32 Chrome extensions, 9 Edge wallet extensions, and 11 Firefox wallet extensions. This allows the threat actors to harvest cryptocurrency assets.
Unfortunately, some may think that installing an antivirus tool can eliminate the threat. Well, not with this one. Its Hidden Virtual Network Computing (hVNC) component makes it very hard to be detected by antivirus solutions.
Google Ads Used Maliciously – Fake Apps, Very Real Malware
With every cyber incident that occurs, we clearly see that cybercriminals have continued to explore new techniques to expand their attacks.
Whether it’s ransomware, phishing, or as with this incident, malvertising, they’re finding new ways to target victims all over the world. Sadly, in most cases, they’re succeeding.
What you need to do to avoid this predicament is to stay vigilant when visiting websites. Don’t click on ads – just visit the actual website manually.