Lampion Malware Revitalized – A Phishing Scheme with a Sense of Urgency
Using the users’ haste in coming up with decisions has become a very common practice among cyber criminals. When there’s urgency, a phishing attack has a higher success rate. We’ve seen schemes with verification requests, fake promises, and ban alerts. Apparently, Lampion malware is back and it’s bringing one of the oldest tricks in the book.

Despite witnessing several campaigns in the past that prey on a victim’s “fear” factor, the scheme still works for some reason. The people behind Lampion are sending phishing emails prompting users to download a “Proof of Payment” document from WeTransfer.
As we all know, WeTransfer is a legitimate file-sharing service. In other words, by utilizing it, the Lampion malware can spread in greater volumes. How are the threat actors distributing the malware? What’s at risk? Here’s everything we know.
Proof Needed – Lampion’s Sneaky Scam
As we mentioned, creating a sense of urgency within phishing emails results in very successful scams. Not long ago, threat actors used none other than Instagram in their malicious practices to steal sensitive information.
They disguised themselves as this popular platform and sent emails to users with a promise to verify their account (Adding a blue badge next to their profile).
Of course, this might sound like just going false hope, but the email also includes a timer. As a result, the targets were hasty to click on the malicious link.
Now, Lampion is following the same steps by sending emails that urge users to download a “Proof of Payment” document from WeTransfer. It’s using previously compromised companies to kick off the attack.
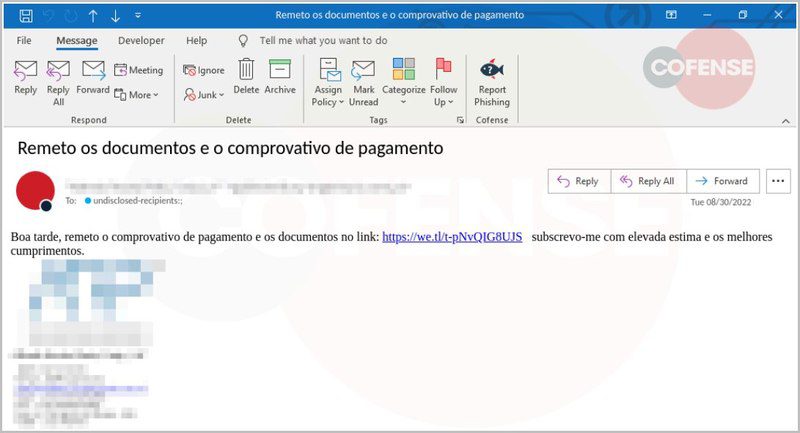
Within the email, there’s a ZIP file that the targets should download and execute. Once they do that, the attack begins.
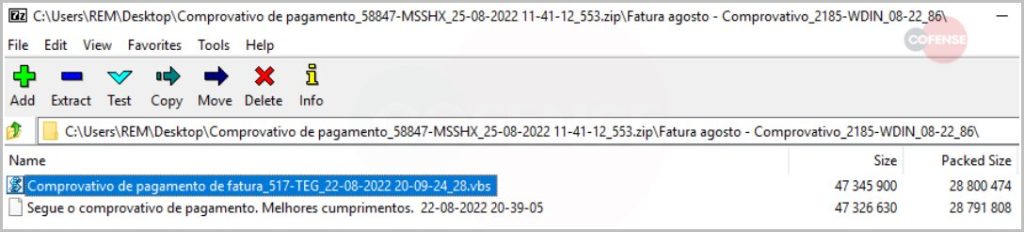
According to security firm Cofense, the script sets up a WScript process, creating around four VBS files with random naming. This technique is quite weird as most of the files do nothing.
1 with nothing inside, the other one doesn’t do much, and the third one only launches the fourth script. At the end of the process, nothing is required by the user.
In fact, even the passwords are hardcoded within the script, which means that the archives can be extracted without having to rely on user interaction.
And now, the malicious magic begins. Lampion starts to harvest data from the infected computer and targets bank accounts. Yes, it does that through injections from the C2 and overlays forms on login pages.
Finally, the attackers wait for the users to submit their credentials, which eventually they will. Once they do, these fake login forms will send everything to the attacker.
Lampion Malware is Back – Remodeled, Remasters, and Ready for Action
The Lampion malware’s operation dates back to 2019. Back in the day, it mainly focused on Spanish-speaking targets and apparently, the attackers behind it did not change this rhythm.
When it comes to phishing attacks, there’s always a way to avoid them. The emails will definitely have some sort of link or file that you should click on.
If you stay vigilant and avoid clicking on anything, you’ll be safe and the attackers won’t have the chance to infect your device. If you ever receive a link, make sure to visit the official page manually – it’s the best way to stay safe.





