Windows Hit Again – The Vidar Malware Infiltrates
Windows users can’t seem to catch a break lately as cybercriminals have been targeting them for quite some time now with various campaigns. A couple of days ago, threat actors launched an attack that injects three malware trojans through fake emails. Now, they’re sending trojanized installation files to infect devices with the Vidar information stealer malware.

When users get certain notifications from Adobe Photoshop and other legitimate software such as Microsoft Teams, they’re bound to fall for the deception. Unfortunately, this is the case with this campaign and the damage is pretty huge.
The Vidar malware is dangerous and every Windows user’s private information is at risk. What’s this about and how does Vidar operate? Give this article a quick read for additional information.
Vidar Malware – Install, Infect, Harvest
Almost all malware campaigns work the same way in every attempt. First, they send a fake notification, email, or pop-up claiming to be something legit to lure the user in.
Once the user clicks on a link, the threat actors redirect them to fake websites that look convincing enough to complete the process.
Once the victim installs the file he/she’s been redirected to this whole time, the malware injects itself into the system, and starts its malicious activity.
The Vidar malware follows the same practice. As we mentioned, it disguises itself with Adobe Photoshop and Microsoft Teams to trick users into downloading trojanized installation files.
According to ZScaler– the firm that researched the malware incident:
“The spoofed sites were created to distribute malicious ISO files which lead to a Vidar info-stealer infection on the endpoint. These variants of Vidar malware fetch the C2 configuration from attacker-controlled social media channels hosted on Telegram and Mastodon network.”
The research firm was able to determine most of the rogue distribution vector domains. Appparently, the following were registered back on April 20th, 2022:
- ms-win11[.]com
- win11-serv[.]com
- win11install[.]com
- ms-teams-app[.]net
Apparently, the threat actors know what they’re doing. To avoid detection, they presented the ISO file in an unusually large size (over 300MB).
Not only that, but they also used an expired certificate from Avast to solidify the legitimacy of the file and gain the victims’ trust.
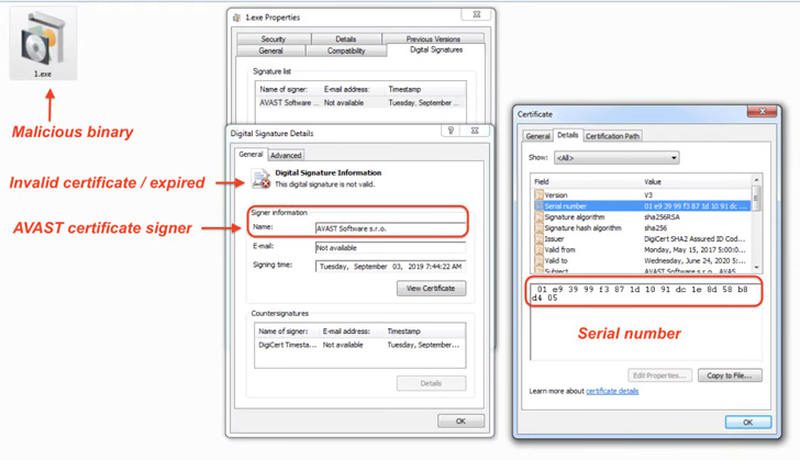
While the 300 MBs file can fool victims, security researchers won’t fall for that trick as they can see that there’s a 3.3MB-sized executable within.
According to Zscaler, that’s the Vidar malware. All the other content in the file has 0x10 bytes just to make the entire download bigger in size.
The Vidar Malware – Your Information it Seeks
The Vidar malware can pose a serious threat, especially with what threat actors can achieve at the end of the process.
With this malicious software, the cybercriminals can establish connections to a remote command-and-control (C2) server to retrieve legitimate DLL files.
We’re talking about the likes of sqlite3.dll and vcruntime140.dll. Once they finalize the process, they’ll be able to harvest valuable data from the victim’s systems.
All we have to say is that you have to make sure that what you’re downloading is official. Never click on a link or pop-up without double-checking first.
We highly recommend you visit the source’s legit website. It’ll take a couple of seconds longer, but it sure will save you a lot of trouble in the end. You should protect your data, and in order to do that, stay on the vigilant side of things.





