0mega Ransomware – Relatively New, Definitely Impactful
In the world of ransomware, groups tend to cause as much damage as they could in hopes of making a name for themselves. You either start big or cease to operate – that’s it. A few weeks back, Malibout wreaked havoc among Android users. Now, another new ransomware operation is using double extortion to target organizations worldwide – enter 0mega.

Spelled with a zero, the omega operation back in May 2022, which makes it relatively new. To make it in this industry, these threat actors attacked numerous victims since then.
This time around, their sight is set on big organizations as they target them with sophisticated attacks, resulting in demands for millions of dollars in ransoms. What is 0mega and how do they operate? Let’s dig a little deeper.
0Mega Ransomware – A Certain Mega Threat
Ransomware gangs have been upping their game when it comes to infiltrating their victims’ systems. Speaking of games, not long ago, Ryuk managed to make its way into one of the most popular gaming platforms – Roblox.
This shows that there’s no particular target, anyone is fair game when it comes to ransomware. 0Mega is still new and how it operates remains a mystery – a ransomware sample for the 0mega operation is still non-existent.
But the proof of its functionality is, which Bleeping Computer recently reported. Just like any ransomware attack, 0mega alters the encrypted files’ names. It adds .0mega extension and creates DECRYPT-FILES.txt ransom notes depending on the target.
What does that mean? Well, usually when threat actors are using ransomware, they leave common notes informing the victims that their systems have been breached.
The note also includes some sort of payment link to be paid via cryptocurrency (Most of the time). However, with 0mega, each target gets a customized note.
That’s mainly due to the fact that it contains the companies’ names. Not to mention a description of the files the attackers have stolen.
Aside from that, 0mega also includes something extra in some of its notes. Several companies might receive threats on how the operation might make the breach public if the ransom goes unpaid.
Beyond the Note
As mentioned, ransomware notes usually include a link that redirects the victims to a payment website – usually through Tor. It’s no different this time as the link in the note takes the target to a Tor payment negotiation site with a “support” chat.
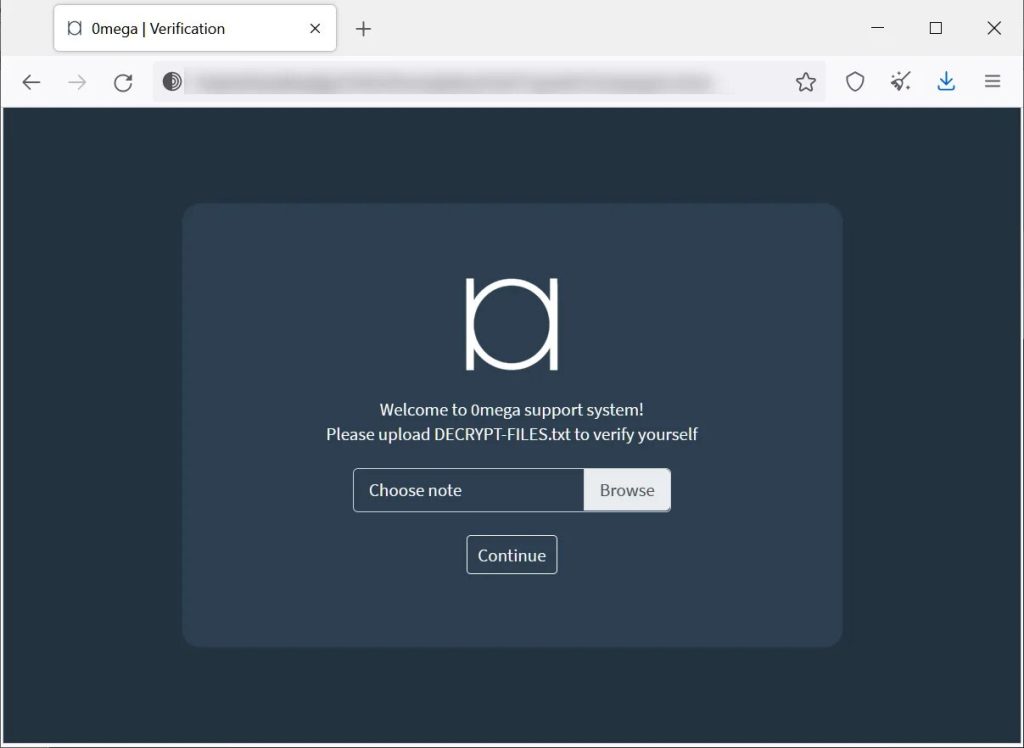
The process here is quite different. Apparently, the ransom note isn’t the only thing in this campaign that works on an individual basis.
In order to access the website, the victims are prompted to upload their ransom notes and hit continue. These notes have a unique Base64-encoded blob which the site uses to determine the victim.
Finally, just like most ransomware operations, 0mega does have its own hacking forum where the threat actors publish stolen data if a ransom is not paid.
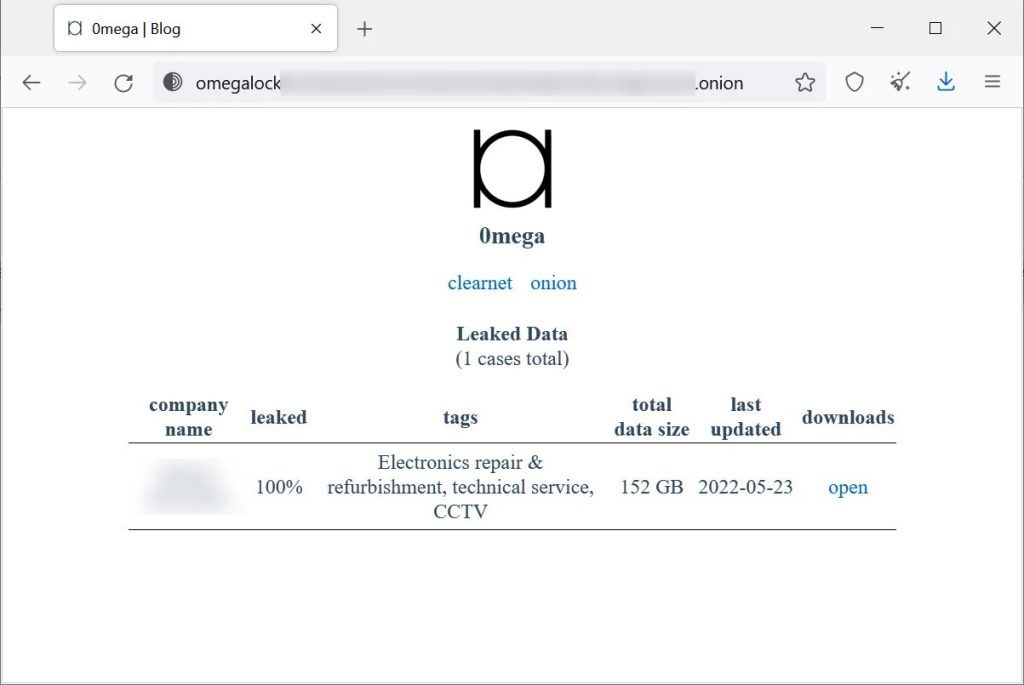
0mega’s inception took place in May, with a huge attack on an electronics repair company. As seen in the image above, the 0mega’s leak site hosts 152 GB of data stolen from the organization.
Soon after that, another victim was added to the site. However, 0mega then removed it, which might indicate that the company has paid a ransom.
0mega Ransomware – New Family, Mega Impact
0mega struck major companies and has done major damage. The ransomware is still new, but we expect future attacks shortly.
Companies and organizations should take proper precautions as ransomware attacks are on the rise. Whether it’s 0mega or any other form of attack, anyone is susceptible.





