2K Games Support Infiltrated – Redline Malware for Everyone
We have no idea what’s been going on with the gaming industry lately. Companies all over the world are being targeted by cybercriminals and it doesn’t seem to be stopping. A couple of weeks ago, Bandai suffered an attack. A few days back, Rockstar’s GTA 6 footage got leaked. And now, 2K Games discloses a hacking incident. It’s out of control.

2K Games have launched some of the biggest games in the entire industry. We’re talking NBA, WWE, MLB, and more. In other words, the impact of such a hacking incident can be huge.
The company itself is not breached, but its support department is. No, this is not good news since the support department can contact every single user – and the attackers did. What’s this about? We’ll discuss it below.
2K Games Hack – From Support to Total Control
It’s simple. The support site for 2K Games has been hacked. The attack begins with a hacking attempt on 2K help desk platform. Apparently, the threat actor was able to gain access to the credentials of one of the company’s vendors.
2K is huge as it’s behind one of the most lucrative video game franchises on the planet with the annualized NBA and WWE 2K series. In other words, that attacker can gain a lot if phishing was involved – and it is.
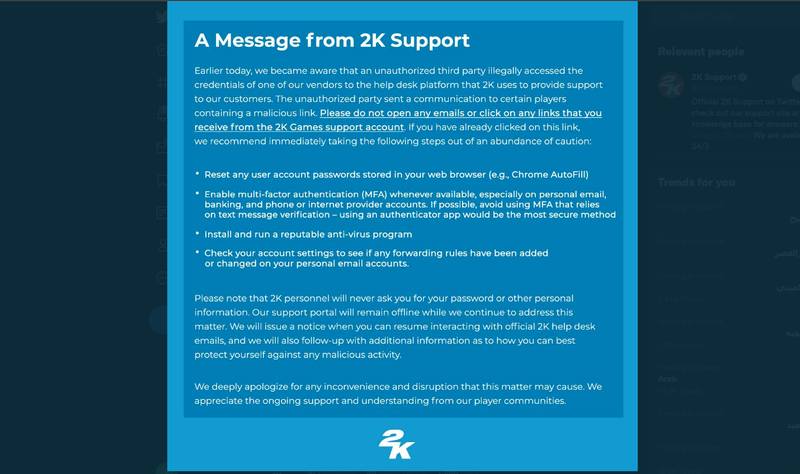
“Earlier today, we became aware that an unauthorized third party illegally accessed the credentials of one of our vendors to the help desk platform that 2K uses to provide support to our customers.
The unauthorized party sent a communication to certain players containing a malicious link. Please do not open any emails or click on any links that you receive from the 2K Games support account.”
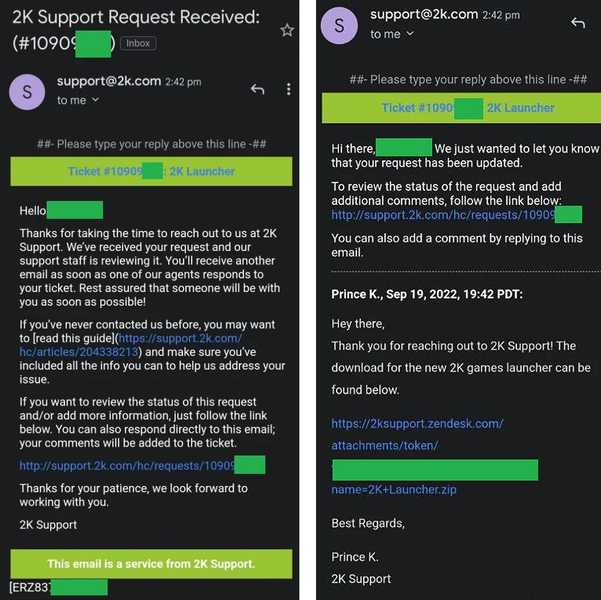
Now, the threat actor behind this is sending emails to certain players containing a malicious link. A lot of users have stated that the sender of the email goes by the name of Prince K.
As we mentioned, the email includes a link that allows the receiver to download a file named ‘2K Launcher.zip’ from 2ksupport.zendesk.com.
Unfortunately, this is no common phishing attack as the Redline info-stealer is involved. If you’re not familiar with what RedLine is capable of, let us explain.
RedLine acts as info-stealer malware. Once it infects a device, it can harvest a wide range of data. That includes cookies, passwords, credit cards, SMS content, cryptocurrency wallets, VPN credentials, as well as web browser history.
2K Games to The Rescue
To further protect its users, 2K released a statement on Twitter, providing them with steps they should take:
- Reset any user account passwords stored in your web browser (e.g., Chrome AutoFill)
- Enable multi-factor authentication (MFA) whenever available, especially on personal email, banking, and phone or Internet provider accounts. If possible, avoid using MFA that relies on text message verification – using an authenticator app would be the most secure method
- Install and run a reputable anti-virus program
- Check your account settings to see if any forwarding rules have been added or changed on your personal email accounts.
The company stated that it’ll issue a notice when the users can resume interacting with official 2K help desk emails. But we still have to ask: Does this have to do anything with the attack on Rockstar?
The timing is nothing less than suspicious. We don’t know anything yet, but we’re sure that 2K will clear things out once everything is back in place.
2K Support Breach – Is It Lapsus$?
Let’s try to connect the dots. A week ago, the actor behind Uber’s breach turned out to be none other than the Lapsus$ extortion group.
The same malicious entity claimed the Rockstar Games breach as well. So, since the last two breaches occurred at the same time targeting two companies of the same department – does that mean that it’s the individual that represents Lapsus$? We have to wait to find out.





