Roaming Mantis is Back – French iOS/Android Users Beware
Phishing attacks are now everywhere. Everywhere we hear of an incident that involves phishing – that’s how common these practices have become. When we speak of such attacks, Roaming Mantis comes to mind as one of the most dangerous on the market. A couple of months ago, the mantis targeted iOS and Android users in Europe. Now, it’s a similar campaign but the attackers narrowed it down to France only.

The phishing campaign is pretty sophisticated and well-thought-of. Each operating system has its own form of infiltration technique. For Android, it’s a banking trojan – for iOS, it’s credential harvesting landing pages.
Roaming Mantis is a huge threat to people all over the world. To hit France specifically after months of expanding its targeting to include European countries, it’s quite unusual. Here’s what we know so far about this operation.
Android and iOS Users – There’s a Mantis in Your Device
Roaming Mantis has been around for quite some time now, wreaking havoc among Android and iOS users all over the world.
Don’t mistake this malicious operation for another Mantis that goes by the name of Luna Moth. This is quite different but as effective.
Basically, the entire campaign revolves around SMS phishing (Smishing). Oh, trust us, that’s an effective approach. According to the study by Sekoia researchers, more than 70,000 Android devices are said to have been infected during this active malware operation.
First, the victims receive a phishing SMS, which contains a link for the user to follow. If the victims are Android users, the link will proceed to download a malicious APK.
Once installed, the application will request permission to read and send SMS messages. But how does it gain the users’ trust? Well, the study states that it mimics the Chrome application to lure the victim into giving permission.
As for iOS users, we all know that no APK is allowed to be installed on the device. That’s why the intended link redirects them to credential harvesting landing pages that mimic the iCloud login page.
But before it does any of that, it examines the user’s location to determine whether he/she is in France or not.
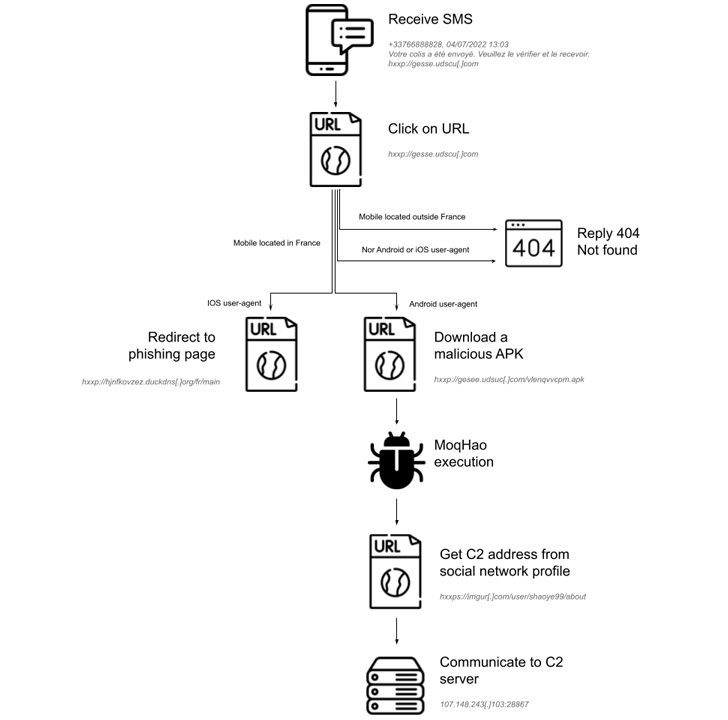
Now, we did mention that the threat actors examine where the victims reside before deploying any further practices. If the target is outside France, the server responds with a “404 Not Found” status code.
Unfortunately, the campaign is bigger than we think it is. It’s not just using SMS phishing – some users have reported that they’ve seen its practices on Twitter as well.
This Mantis is Roaming the French Region
Roaming Mantis is a financially motivated Chinese group, with a history of targeting developed countries. The past campaign was able to infiltrate users’ devices all across Europe.
Can you imagine the impact it can do when it sets its focus on one country only? The attackers can easily harvest sensitive data such as iCloud data, contact lists, call history, and SMS messages. So best be vigilant and avoid following any link you come across.





