ChatGPT’s Popularity Utilized Again – Fake Chrome Extensions Everywhere
A ChatGPT’s popularity reaches new highs on a daily basis; threat actors are not missing any opportunity to prey on it. Recently, fake ChatGPT applications surged across the World Wide Web. Now, the AI Chatbot is back in the spotlight with a new campaign spreading fake Chrome extensions that can hijack Facebook accounts.

ChatGPT is huge, and having an extension gives users the convenience they lack, as the service is only accessible through web browsers.
In other words, it’s easy to trick victims and lure them in with fake ChatGPT apps and extensions. But the question is: What can the threat actors do with hijacked Facebook accounts? We answered that below.
Fake Chrome Extensions – Very Real Hijacking Operation
When it comes to luring victims into downloading any sort of malware or info-stealer, using big names as a disguise is the way to go.
In fact, this practice has become very popular among cybercrime groups all over the world. In recent months, fake services spread across the internet. Their endgame? Harvest personal information.
Threat actors can use any kind of service, be it debuggers, plugins, and more. They even masquerade as big companies to practice phishing attacks.
As we mentioned, cybercriminals will seize the opportunity to strike, and ChatGPT’s popularity presented just that.
Now, unknown threat actors are distributing fake ChatGPT Chrome extensions that can literally hijack Facebook accounts, create rogue admin accounts, and push paid ads at the expense of the victims.
Guardio Labs observed the campaign, and according to the firm’s researcher Nati Tal:
“A Chrome Extension propelling quick access to fake ChatGPT functionality was found to be hijacking Facebook accounts and installing hidden account backdoors.
Particularly noticeable is the use of a malevolent silently forced Facebook app “backdoor” giving the threat actors super-admin permissions.
By hijacking high-profile Facebook business accounts, the threat actor creates an elite army of Facebook bots and a malicious paid media apparatus.
This allows it to push Facebook paid ads at the expense of its victims in a self-propagating worm-like manner.“
Let’s dive deeper into why this extension is attracting many people. ChatGPT (The real one) allows access through WEB BROWSERS ONLY. There are no apps, no extensions, and no add-ons.
This can be quite inconvenient for a lot of users out there. So, when promised an app or extension that would ease it up for them, they’ll come running.
The Extention and Practice
The chat extension is called “Quick access to Chat GPT,” which is said to have attracted 2,000 installations per day. That’s a lot of victims.
Users may stumble upon it through sponsored Facebook posts. Once installed, it siphons cookies and Facebook account data using an already active, authenticated session.
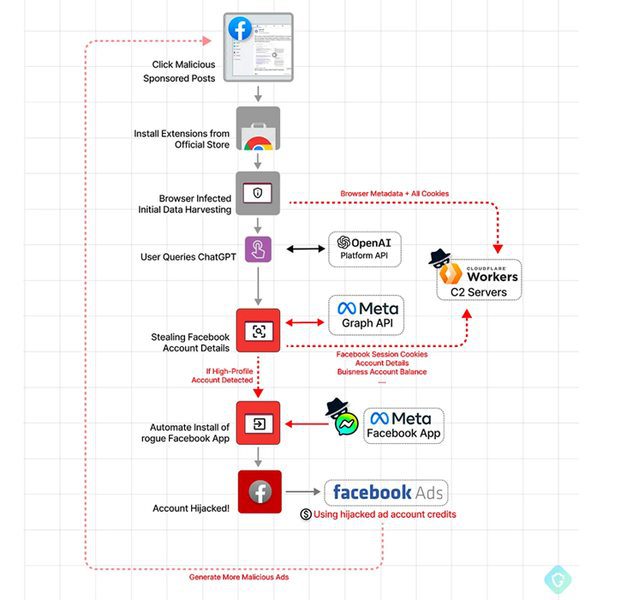
The threat actors will then gain backdoor access and obtain full control of the target profiles. Of course, once they’re in, they’ll have to expand their campaign.
And what better way to do that than to further advertise malware and take over a whole new collection of compromised accounts? It’s getting very dangerous out there with all these fake applications roaming around.
ChatGPT Utilized Again!
It’s pretty obvious that cybercriminals are capitalizing on the massive popularity of OpenAI’s ChatGPT. The service was used numerous times in the past to direct users to malicious domains that download information stealers.
Now, threat actors are back with this new campaign. According to Google, the extension has been taken down. But what about the already-done damage? Are there going to be more similar campaigns in the future? Only time will tell.





