When Convenience Turns Malicious – 60,000 Android Apps Hosting Adware
Android users have the privilege to download content from all sorts of sources all over the web. There are just no restrictions when it comes to where they get their downloads from. However, such convenience doesn’t come without a price, and that’s their devices’ security. Those third-party websites can be hosting malware, and that’s exactly the case now, as more than 60K Android apps have secretly been installing adware for months.

Emphasis on month due to the fact that the campaign is believed to have kicked off back in October 2022. Using fake “Legitimate” applications, the threat actors are luring victims to their websites, tricking them into downloading the software and injecting their devices with adware.
With such a campaign at hand, one would ask the following; How are these fake applications distributed? How does a victim end up on the maliciously-crafted pages? What apps are in question? We’ve discussed everything below.
Android Adware Campaign – Fake Apps, Legit Infection
In the world of cybersecurity, various types of threats lurk across the World Wide Web, especially aggressive adware that might annoy users with a bombardment of ads. Not only does this cause frustration, but it’s also a complete invasion of privacy.
As we mentioned, Android users have the privilege to get their files from any source. It’s convenient and easy, but it’s also dangerous. And since threat actors keep elevating their scheming techniques, users are bound to end up on one of their malicious websites eventually.
Using multiple methods, they can easily trick their victims. In fact, they can use Google Ads to promote their fake application, even when disguised as legitimate ones. Yes, this particular campaign involves very popular tools that anyone would search for on the web.
The apps exceed 60,000, which is a huge number for fake software. According to the Romanian cybersecurity firm Bitdefender, these are some of the types of apps mimicked by the malware:
- Game cracks
- Games with unlocked features
- Free VPN
- Fake videos
- Netflix
- Fake tutorials
- YouTube/TikTok without ads
- Cracked utility programs: weather, pdf viewers, etc
- Fake security programs
Ever since it kicked off back in 2022, the campaign has targeted various countries around the world. However, Bitdefender’s study shows that most infections are reported to be in the United States followed by South Korea, Brazil, Germany, the United Kingdom, and France.
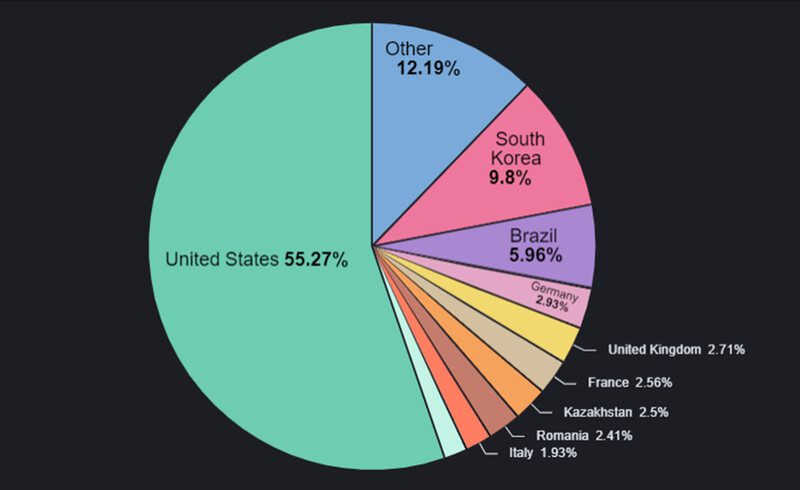
The distribution is quite astonishing, considering that none of the apps is available on Google Play Store. They’re just out there on unknown websites, spearing the adware to all those countries.
The Infection Process
So, here’s how everything goes down. The victims go to a random website promoting their desired application. They download an APK file to install the app in the next step.
To avoid detection or asking for privileges, the applications follow a different path – the one where an App prompts the users to “Open” it once it’s present on the device.
With no logo or icon, the app would be very hard to spot. So basically, it only functions when the user first installs it. On the surface, the application will present the victims with an error message, stating the following:
“Application is unavailable in your region. Tap OK to uninstall.”
Based on Bitdefender’s findings, the app doesn’t operate for a while. It takes it a few days to initiate its malicious activity to further evade detection by the user.
When everything is in place and the app launches, it’ll send information to attackers’ servers, retrieve advertisement URLs, and then displays them in the mobile browser or as a full-screen WebView ad.
While these ads are considered more annoying than dangerous, it’s a matter of time till the threat actors behind this campaign change the URLs. Users might get advertisements promoting malicious websites that deploy real malware in the future.
If you think third-party websites are the only threat here, you’re mistaken. Yes, Google Play Store might be the best and safest way to download content, but it’s not always safe. The Android app library does remove malicious content, but only after developers and researchers report it.
In other words, users would’ve already downloaded the infected apps, and the damage has already been done. Yeah, Google Play Store has had its fair share of malware infiltration in the past.
Android Adware Everywhere – 60K is a Huge Number
If you’re an Android user, you should always remain vigilant when downloading content online. Your devices are highly targeted by malware developers due to the ability to download stuff from all over the web.
Fake Google advertisement is not a new technique in the cybercrime world, and it should not be taken lightly. Also, since one of these fake applications is Netflix, you’re definitely better off installing it from Google Play.





