BYOD: How to Deal with Risky Devices Employees Connect to Your Network
Your organization may have or have not Bring-your-own-device (BYOD) policies in force. However, in both cases, your employees are connecting numerous and varied devices to your enterprise network.
An average business does not operate like a maximum-security prison or a state service agency where both employees and visitors cannot carry devices that are not explicitly allowed.

Nonetheless, bearing in mind the consequences arising from an infected mobile gadget being plugged into your business systems, you might need to revise your cyber-security policies in place.
With that in mind, here’s everything you need to know about BYOD, its risks, and how to fix them.
What Is the Problem with BYOD?
Actually, there is no problem with employees bringing their own devices to perform their work in your office or connect remotely to your corporate network.
A comprehensive BYOD policy and adequate IT security measures, implemented within a properly built and maintained IT infrastructure, give you an acceptable level of overall data security.
The problem lies with what your employees exactly connect to the corporate network.
If you have a working BYOD policy, it should specify what devices your employees are allowed to connect up to specifying device models and brands.
Over Half of CIOs Consider BYOD and Cloud Apps a Threat
Back in 2016, IT security professionals conducted a survey in the United States. According to the results, BYOD device practice was one of the biggest threats to endpoint security based on 56 percent of respondents.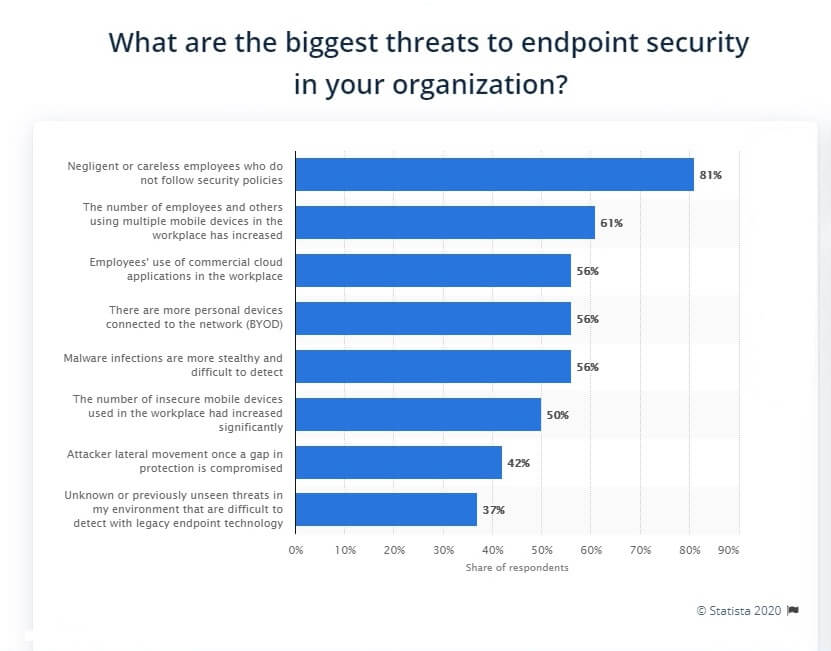
Employees, however, tend to plug whatever they carry with them into an organization’s network.
Those include devices such as smartwatches, fitness trackers, digital home assistants, IP cameras, and other consumer-grade devices that have little or no built-in protection.
How Do These Devices Work?
These devices communicate with the outside world over plain text channels to transmit data, which in turn puts your entire network at risk.
Actually, four out of five IoT devices like smartwatches still send data in plain text, which in turn requires very fine firewall rules adjustments if you stop this traffic from leaving your in-house network.
Sometimes it is actually impossible as these devices communicate over ports used by other legitimate business applications, which need these ports open in order to operate.
On the other hand, numerous malicious actors are listening to these networking ports to intercept any data they can catch or perform a man-in-the-middle attack against your data servers and applications.
Intrinsic Weaknesses of BYOD
Regardless of the level of sophistication of your cyber-security policies, the very BYOD approach has weaknesses you cannot cope with at this stage of IoT development.
New IoT products come to life almost daily, and all of them are capable of connecting to a network and transmit data.
A good number of these devices lack even the basic capabilities to protect the data they store and transmit, which in turn makes them a good target for any hacker to start exploring for further weak points across your network.
What is worse is that many of these gadgets are compromised at the firmware level, and there is no way for anybody to rectify these problems embedded by the device manufacturer even before the respective device has left the factory.
Firmware issues are common across a broad range of devices ranging from IP cameras to printing devices to smartwatches.
Let Us Summarize
While BYOD can make working more convenient, it sure does a lot of damage to companies.
Yes, it does allow employees to work freely and in a more comfortable way. However, employers are always looking over their shoulders.
Check out why below:
Data Leakage
Mixing work and personal life together on one device is a very dangerous thing. You don’t know what applications the employee has installed on his/her device.
Malware is everywhere towards, and hackers target those who install applications blindly.
On the other hand, there’s a high possibility of losing or misplacing the device outside work premises.
This grants whoever finds it full access to the data on the device. Reports state that 28% of Americans don’t lock their phones using passwords and the likes.
So, basically, if a phone is lost, it’s an open invitation for whoever holds the device to check the private data freely.
Lack of Management
Following up with employees outside the workplace can be hard. You never know whether they’re connecting to public networks or not.
This is very crucial, considering the rise of hacking attempts in public places such as Coffee shops, Cafes, and airports.
Also, you don’t know if they’re going places where they might lose the device containing the important data.
So, basically, the lack of control can result in devastating effects on the company’s data. You should put some ground rules, or cancel the BYOD system, to begin with.
Using Jailbroken Devices
This is pretty common among users with technical knowledge. Most mobile users jailbreak their phones to bypass the manufacturer’s limitations.
This allows them to install unauthorized applications, which you might find popular among iOS users.
However, this increases the risk of installing malicious programs on the device. In fact, back in 2015, more than 225,000 people fell victim to data theft while using a jailbroken iOS device.
Outdated Software
We can deduce that not all of us are “IT specialists.” Updates exist for a reason, which is to fix previous problems certain software had in its previous version.
Updates happen frequently, especially on smartphones. The problem is that your employee doesn’t always keep up with these updates.
For example, they might not install the latest version of their anti-virus or firewall. A poorly updated device makes hacking much easier and leaves a company’s data vulnerable.
Stuxnet – The World’s First Digital Weapon
Malware does not spread only through online connections, though. In the past, a number of high-level cyber-attacks against, take a note, nuclear power plants in Iran occurred.
Attackers performed such attacks through planting malicious code by the means of infected flash memory sticks and within networks that are not connected to any outside network. End to the myth of protected closed networks.
Your business is barely an NPP, but the attack vectors are all the same. This means you should have an idea of how to deal with employee devices that easily connect to your business-critical systems day in and day out.
Methods to Deal with Risky Employee Devices
Connected mobile devices are the new favorite target for cybercriminals and government hackers alike. We’ve already discussed the major reasons for that above.
The problem is that you need a very well-thought BYOD policy if you are to minimize the risks associated with employees’ mobile devices.
Many people think that an antivirus suite and a firewall are sufficient to prevent connected devices from leaking data or otherwise exposing your network to prying eyes.
It is not the truth, though. You need proof, and we understand that. Nothing speaks louder than statistics. And that’s exactly what you’ll be getting next.
BYOD – Statistics
In the first half of 2019, Kaspersky Lab issued a report to address the matter. It shows that IoT-specific attacks reached 105 million attacks from 276,000 unique IP addresses.
To compare, the year before showed a huge difference in numbers. In fact, in 2018, reports indicated that there were “only” 12 million attacks at IoT devices originating from 69,000 IP addresses.
This means one thing for your BYOD infrastructure. Technically, you have a big problem associated with the need to block close to 300,000 unique IP addresses in your firewall.
Moreover, you still need to know which these addresses are before you even try to block them.
One more thing, any mobile device your employees bring to work is actually working most of the time outside the guarded perimeter of your corporate firewalls and antivirus systems.
Top Tips for BYOD Systems
The solution? You can take some measures to limit or illuminate the risk of using BYOD in your company. Below, you’ll find a couple of tips you can follow:
First Time Connection Technique
Treat all these devices as if they are connecting for the first time. This might frustrate the employee, thinking that it’s a lack of trust.
Well, it is, but it’s not in the employee; it’s in the device they’re operating. Experts call it Zero-trust policy, but it extends not only to physically connecting to the internal network.
Limit Employee’s Access
A thorough BYOD policy should also deal with the access rights of each and every user. That includes a power user or administrator account.
It should also explicitly ban such devices from getting administrator privileges unless you are 100% sure the user needs such login credentials and connects through a safe and checked device.
Ban Certain Applications
Using personal phones for work can be very dangerous, as we mentioned. Therefore, it’s up to the company to limit the usage of certain apps.
Blacklisting certain software on devices used for work is a very good step towards better security.
We’re talking about apps such as file sharing and social networking. If we were to follow what Appthrority stated in their report, companies should ban the likes of WhatsApp, Wickr Me, and Facebook Messenger.
All the company has to do is use a mobile device management platform. There are a couple of those on the internet, allowing admins to enforce strict policies on enrolled devices. VMware or AirWatch are two top examples.
However, since it’s an employee’s own device, they have to draw the line somewhere. Their privacy is included here as well.
Enhanced Security
The company has to ensure that BYOD devices are protected with reputable antivirus software.
That way, no malware or virus infections can target the employee’s device. As a result, the company’s data and the user’s own will be safe all the time.
Malware prevention is a great step towards protecting personal information, and all companies should abide by it.
Enforce Monitoring Practices
Now we have mixed emotions about this part. It does allow the company to keep a keen eye on its information, but at the same time, it’s an invasion of privacy.
A lot of companies implement such practices as part of the BYOD agreement. A certain app is installed on the employee’s device, allowing administrators to keep track of everything done.
That includes suspicious activity, the device’s location, and app installation. But as we mentioned above, we have mixed emotions about it.
It’s crucial to keep a balance between securing the companies data and respecting the privacy of your workers.
Data Backup
Finally, there’s the backup solution. It’s a very good policy to minimalize the damage caused by losing the device or the data itself.
If malware managed to slip past the antivirus and monitoring process, you’d still have the data safe and sound elsewhere.
You can later restore it after taking the right precautions for preventing such an incident from occurring again.
Educate your staff about security and use data back up on a regular basis. It can help a lot.
Concluding Words
The above paragraphs sound a bit paranoid, but these are today’s cyber-security realities.
You just need to realize that connected devices are still an easy target for a knowledgeable hacker, while most device manufacturers are yet to offer an acceptable level of security and hacking protection for their IoT devices.
Having a policy that deals with hardware and software protection is a must. Still, you need a thorough BYOD in place stipulating strict rules: who, when, from where, and how can connect to your corporate network remotely or through a mobile device.
Connecting to a network now means not only plugging an advanced device such a laptop, it means plugging any device that can store or transmit data.
Was this guide helpful? Share your thoughts in the comments below.





