Dark Herring – Android Hit With Yet Another Premium Services Subscription Scam
Android devices are being targeted over and over, and they don’t seem to keep up lately. Apparently, an attack has slipped under Google Play’s radar as more than 105 million users have suffered a premium services subscription scam for close to two years.

If Google Play wasn’t able to detect such a campaign for that long, we should imagine how grand this attack is. Zimperium zLabs – Google partner and member of the Google App Defense Alliance – discovered the threat, and we’re here to shed more light on it. Here’s everything you need to know about Dark Herring and how it can infect your Android device.
Dark Herring on Android: You Download, You Pay
Using Google Play Store’s applications to infect Android devices with malware isn’t a new strategy. In fact, it has become pretty common as hackers and threat actors find new ways to cloak their presence.
A while ago, a similar attack involved a banking Trojan that affected more than 300,000 devices through apps from Google Play Store.
Unfortunately, Dark Herring also has some pretty solid AV anti-detection capabilities that allowed it to propagate through more than 470 apps on the official store.
The apps themselves don’t contain any malware, but they do include a hard-coded encrypted string that points to a first-stage URL hosted on Amazon’s CloudFront.
When the server responds, Zimperium reports that it contains links to additional JavaScript files hosted on AWS instances. These are also downloaded on the infected device.
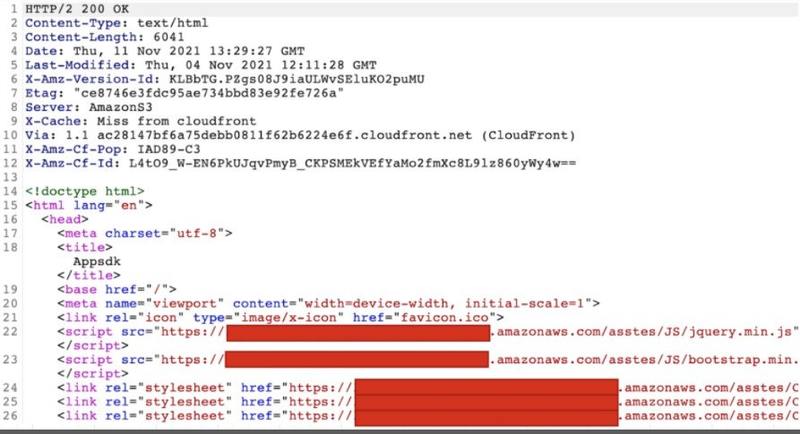
The script allows the apps to determine a lot of information about the user. That includes the language and country details, and the DCB platform (Direct Carrier Billing) that is applicable in each case.
When all of the above is done and the user proceeds to log in, the apps ask for a phone number. The victim might receive an OTP as well to finalize the signup process. Then, the scamware truly begins.
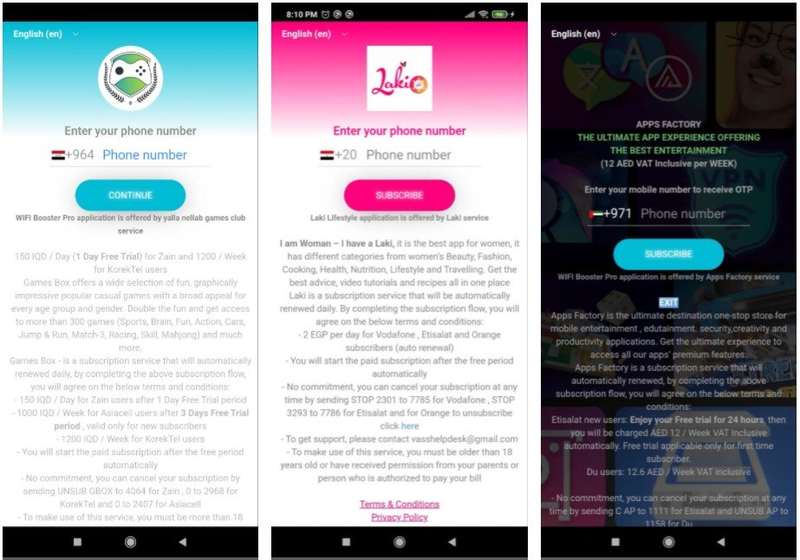
As seen above, the apps present a customized page for the users to submit their numbers. Once the process is complete, the malware starts working in the background, subscribing the victims to premium services that charged $15/month through Direct Carrier Billing – a digital payment that lets people purchase digital content from the Play Store
The Global Spread – Countries & Apps
The scam used apps that appeal to any user out there, which is why it has reached global status. Not to mention that it has been around for around 2 years, allowing its focus to spread to several countries, including Egypt, Greece, Finland, Sweden, Norway, India, Pakistan, Saudi Arabia, Bulgaria, Iraq, and Tunisia.
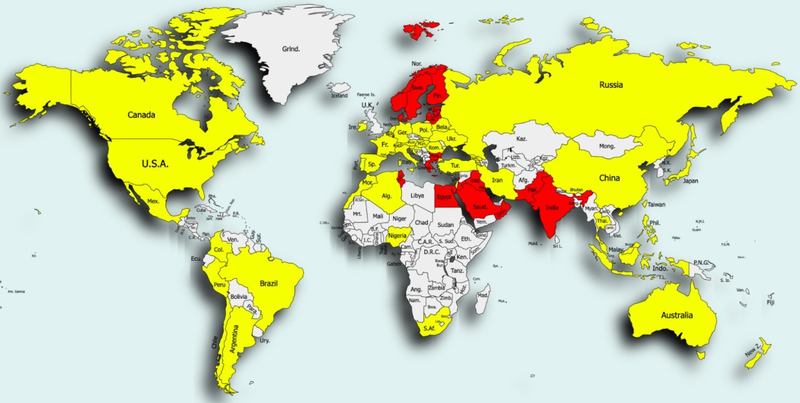
With millions of downloads, the scam has spread all over the world. The apps are used for all sorts of tasks, which guarantees them getting so much interest.
Aside from entertainment, the downloaded apps fall into the photography tools, casual games, utilities, and productivity apps genres. Below, we’ve listed a couple, but this GitHub page provides every single one of them:
- My Translator Pro
- New Mobile Games
- Smashex
- Upgradem
- Stream HD
- Vidly Vibe
- Cast It
- StreamCast Pro
- Ultra Stream
- Football Legends
- Football HERO 2021
- Grand Mafia Auto
- Offroad Jeep Simulator
- Smashex Pro
- Racing City
- Photograph Labs Pro
- Speedy Cars – Final Lap
- Connectool
- City Bus Simulator 2
- VideoProj Lab
- Drive Simulator
This is nothing compared to what the list actually includes. We’ve shared a link to the official GitHub page, you’ll find everything included there.
Dark Herring Gets Darker – Millions of Victims
Scamware is kind of common, but what makes Dark Herring so rare is the fact that it combined several techniques in one campaign.
Aside from subscribing users to premium services, without their knowledge or consent, the malware can easily detect their exact whereabouts by examining their IP address.
We know that we should trust Google Play Store while downloading apps, but several incidents proved that this is no longer the case. Cybercriminals will always find ways to infiltrate the store, and you should always stay vigilant.
Don’t give an app permissions it doesn’t need or submit any information that reveals too much. Be careful and stay safe.





