Google Play Store Breached Once Again – Enter DawDropper
Google Play Store has seen better days. In less than two months, the Android app store has been breached around 5 times. Now, it happened again as it’s hosting apps with banking malware.

We have no idea what’s going on with Google Play’s security measures, but we do know that it’s getting riskier to download applications every day.
More than a dozen malicious applications have infiltrated Google Play’s library. From document scanners, QR code readers, and VPN services, to call recorders, these apps make 17 droppers – codename: DawDropper. What is this about and what are the attackers after? Find out below.
Malware by the Dozen – Play Store Slips Again
Google Play Store has been targeted by such campaigns for quite some time now. The store is practically the only trusted source to get applications.
But with everything going on and the constant lack of security, we can’t help but doubt it now. The number of infiltrations in 2 months only shows that Play Store’s measures are not on par with the attackers’ newly developed skills.
According to researchers at Trend Micro:
“DawDropper uses Firebase Realtime Database, a third-party cloud service, to evade detection and dynamically obtain a payload download address. It also hosts malicious payloads on GitHub.”
The study shows that 17 applications have infiltrated the Android store. And when one of these apps is a Virtual Private Network, the attackers can easily trick their victims into installing it.
The threat actors made sure to use tools that are always in demand. That’s why they settled for document scanners, QR code readers, VPN services, as well as call recorders. We’ve provided the full list below:
- Call Recorder
- Rooster VPN
- Super Cleaner- hyper & smart
- Document Scanner – PDF Creator
- Universal Saver Pro
- Eagle photo editor
- Call recorder pro+
- Extra Cleaner
- Crypto Utils
- FixCleaner
- Universal Saver Pro
- Lucky Cleaner
- Just In: Video Motion
- Document Scanner PRO
- Conquer Darkness
- Simpli Cleaner
- Unicc QR Scanner
These are called droppers for a reason. Their main purpose is to sneak past Google’s Play Store security checks and inject the device with malware.
The Infamous 4 Droppers
In this campaign, the droppers are using some of the most dangerous ones – Octo (Coper), Hydra, Ermac, as well as none other than TeaBot.
The DawDropper malware establishes connections with a Firebase Realtime Database. During the process, it receives the GitHub URL, which allows it to download the malicious APK file.
The security firm explained the entire process in the following image:
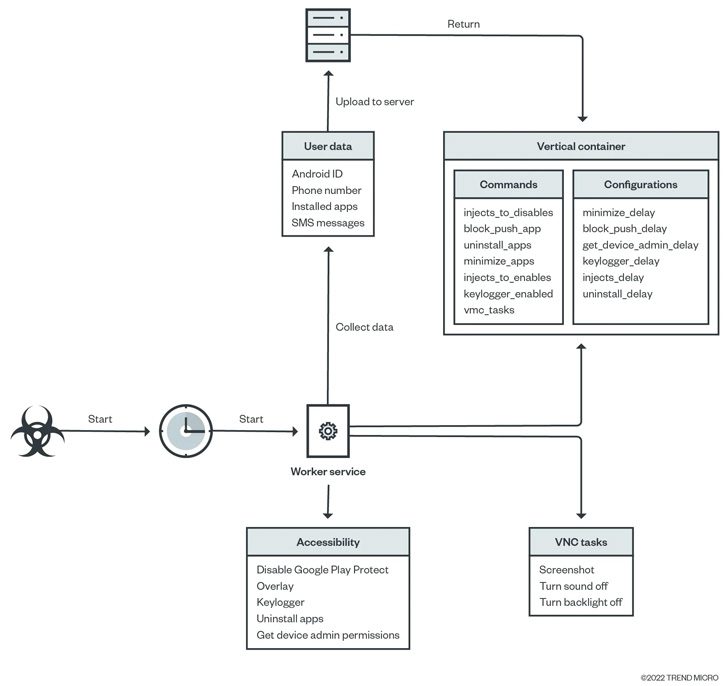
Google Play Store’s security measures are without a doubt top-notch. However, as we’ve seen in the past few months, threat actors have evolved their attacks, especially banking droppers.
With malware such as Octo, they can easily disable Google Play Protect and pivot their way into anyone’s device through Google Play Store.
Another Google Play Store Breach – DawDropper Strikes
Dropper-as-a-service seems to be very popular nowadays. With the capabilities to infiltrate Google Play Store with such ease, we never know what impact it will have in the future.
For those who have already installed the apps, remove them immediately. Not only that but make sure to install a reliable antivirus tool to scan your device and eliminate any remaining threats.
Finally, before you download any application, give the review section a read. It’ll give you a heads-up on whether you should get the app or not. No source can be trusted, not even Google Play apparently.





