Another Play Store Infiltration – Enter Fleckpe
Android devices are very susceptible to malware due to the fact that they allow downloads from any available source. However, for the past couple of months, even Google Play Store has had its fair share of infiltrations. Now, the Android store is back at it again as the subscription malware Fleckpe is lurking around its library.

Threat actors have elevated their techniques throughout the years, coming up with various methods to infiltrate devices and gain whatever they deem beneficial in the process. With Fleckpe, they can earn money by subscribing victims to premium services without their consent or knowledge.
Generating unauthorized charges by subscribing users to premium services is not a new tactic, but it’s kind of uncommon on Google Play Store. So, what’s the deal here? How did the apps end up on the Android Store? What’s at risk? Find out below.
Fleckpe Malware – Premium Subscriptions… Unknowingly!
Spreading malware through unknown sources is a pretty easy task for threat actors. All the victims have to do is download the infected applications and perform their malicious activities.
That’s why we always recommend downloading content from an official source, which for Android, is none other than Google Play Store.
Unfortunately, even the Android store itself has been deemed unsafe in the past couple of months, as multiple infiltrations have occurred, and infected apps have taken over the library.
The more popular the app becomes, the more damage will be done. Well, we can say that in this particular campaign, there is damage since Fleckpe (embedded in disguised fake applications) was downloaded over 620,000 times.
One of those apps is dedicated to body slimming and has harnessed over 100K downloads on the Google Play store.
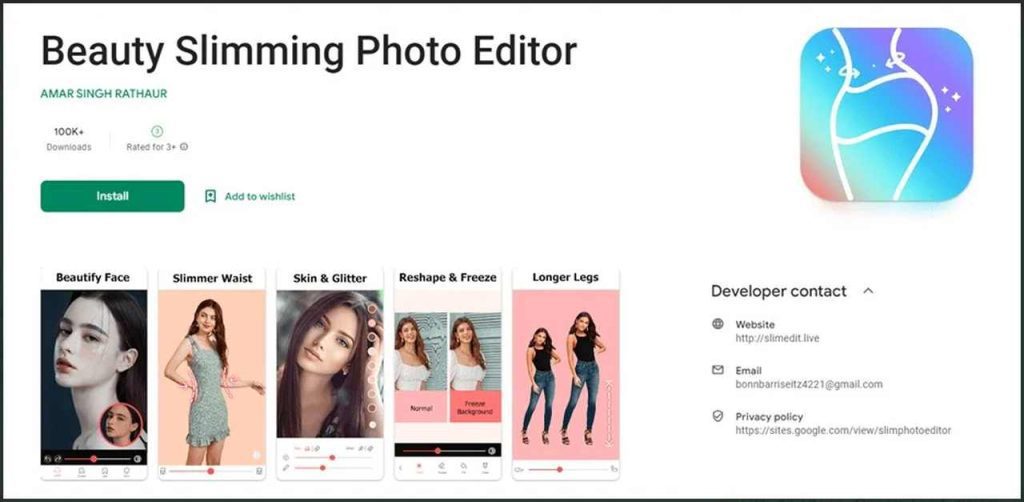
When the trojan is present on the device, the cybercriminals behind it can generate money via unauthorized subscriptions to premium services. That, of course, occurs without the victims’ knowledge or consent.
According to Karspersky’s report, Thailand is the main target of the campaign, as the trojan contained hard-coded Thai MCC and MNC values.
Not only that, but the reviews on Google Play are submitted mainly by Thai-speaking users. However, the security firm also states that a lot of victims reside in Poland, Malaysia, Indonesia, and Singapore also.
A New Threat to Android Users Emerges
When the trojan sends the information to the server, the C2 will deliver a website address of its own. The trojan will then launch an invisible browser where the premium service subscription occurs.
Unfortunately, if the subscription requires a confirmation code, the malware can retrieve it from the device’s notifications on its own, finalizing the subscription process.
Google Play has had better days, but it still represents a secure source to download content. Any store can fall victim to cybercrime, but at least it’s doing something about it.
When you download an application, make sure to check the reviews section. With that, you’ll be able to determine whether the app functions correctly or not.
Moreover, pay close attention to the permissions the app asks for during installation. If things are out of the ordinary, just block its access.





