IcedID Malware Strikes – It Starts with a Fake Yandex Form
When it comes to phishing attacks, preying on the victims’ fear has become a common practice among cybercriminals. Receiving fake warnings creates a sense of urgency, which forces users to act irrationally and click on anything. It happened with Twitter, and now it’s happening again as attackers are pushing IcedID malware using Yandex Forms.

It all starts with a fake copyright infringement complaint and ends with a modular banking trojan that can steal Windows credentials. The attackers are pretending to be Zoho in this campaign and utilizing fake Yandex forms.
With such an attack, the victims will feel obliged to act as fast as they can since violating copyright infringement can cost them a lot. So, what is the aim of this whole campaign? How are the attackers implementing it? Find out below.
IcedID Malware – From a Complaint to Total Control
Phishing scams have been skyrocketing for the past couple of months. Threat actors are upgrading their skills and targeting victims with new techniques to infiltrate their systems.
This type of attack isn’t that new, but it’s definitely different. In the past, we’ve seen similar campaigns that make use of Google Drive or Google Sites to spread the malware.
However, with this one, instead of using these popular platforms, the attackers are pushing the IcedID malware through fake complaints using none other than Yandex forms.
According to BleepingComputer, the threat actors sent them a fake warning signed by Zoho, informing them that they have been utilizing their copyrighted images:
“Hello,
Your website or a website that your organization hosts is infringing on a copyrighted images owned by our company (zoho Inc.).Check out this report with the links to our images you used at www.bleepingcomputer.com and our previous publication to get the proof of our copyrights.
Download it now and check this out for yourself: (Link Removed) I do think you’ve willfully infringed our rights under 17 U.S.C. Section 101 et seq. and could be liable for statutory damage as high as $130,000 as set forth in Section 504 (c) (2) of the Digital
Millennium Copyright Act (”DMCA”) therein.”
The message does not end here. In fact, the attackers added a lot of information that makes this campaign sound as legitimate as it can possibly be.
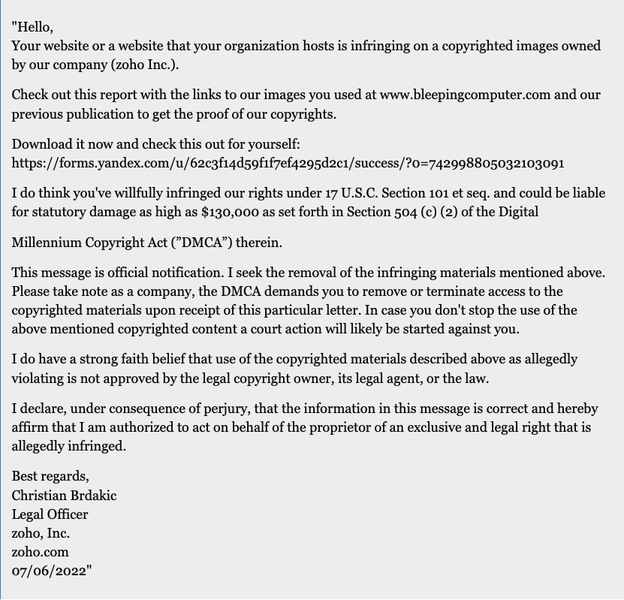
Basically, every phishing attack provides a link, and the message above does include one. Once the victim clicks on the link in the copyright complaint, it’ll redirect them to a page that states “File ‘Stolen Images Evidence’ is ready for download.’
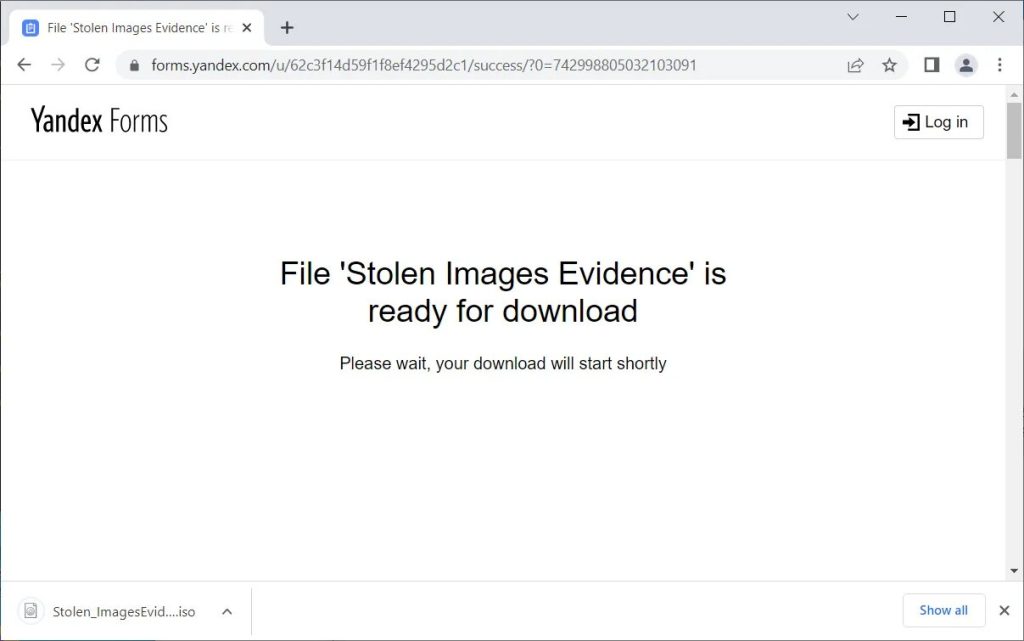
Soon after the victims reach the page, an ISO file that goes by the name ‘Stolen_ImagesEvidence.iso’ will start downloading on the device.
The Last Stage Commences
If the target is operating on a Windows device, the ISO file will mount as a new drive letter that’ll allow the users to access the enclosed files.
It’s actually a good strategy by the attackers. Why? Well, ISO files can bypass the propagating of the Mark-of-the-Web to the contained files.
In other words, the victims’ Windows devices will not warn them whether the file is risky to open or not. Once they open the ISO file, they’ll launch a new drive letter that contains a ‘documents’ folder and a randomly named DLL file.
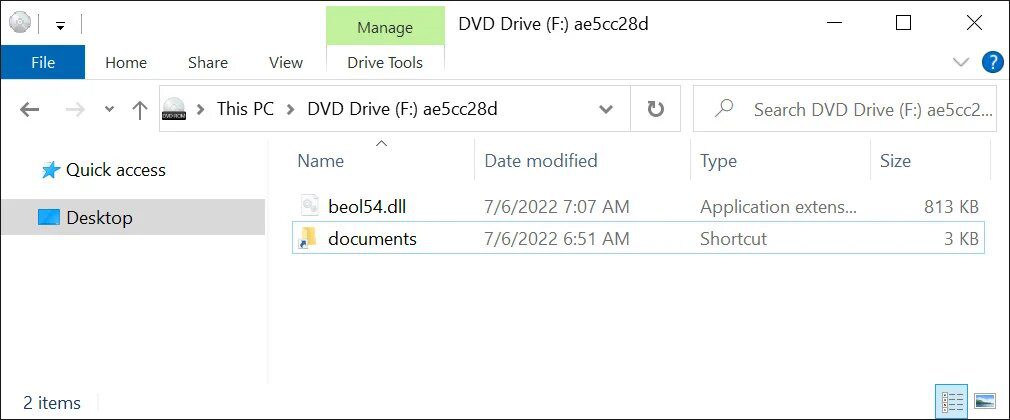
Here’s where the malicious magic begins. Opening the documents folder contains nothing actually. Instead, it executes a DLL file utilizing the rundll32.exe command.
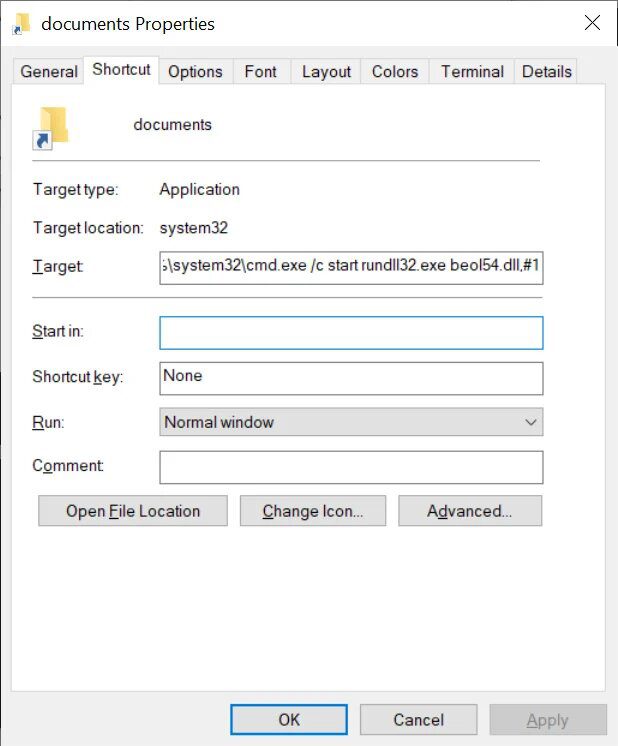
This DLL file will further execute the IcedID malware, which is where everything goes south. Once it takes root, it’ll be able to harvest Windows credentials and other sensitive data.
Not only that, but it’ll also be able to deploy additional payloads to allow initial access to networks. We’re talking about the likes of Cobalt Strike beacons.
A Complaint Better Left Unanswered
Fake complaints and warnings can create a sense of panic, which leads to irrational decisions. Anyone could fall for a trick like this actually, and a lot have in the past.
This campaign is pretty convincing. The attackers utilize threats of legal action to create urgency to the message. That’s exactly what they need to come out successful.
No matter what the warning is, you have to make sure it’s legit. Instead of a sense of urgency, try to be vigilant and cautious. If you do so, you’ll avoid this entire predicament with no harm done.





