Luna Moth Phishing Attack – Fake Subscription Renewal, Very Real Threat
Ransomware has become a common way of earning a living for a lot of threat actors out there. To deploy their malicious software and encrypt their victims’ data, the attackers resort to several techniques, especially phishing attacks. Targeting big companies to steal confidential information is the goal, and that’s exactly what this new phishing campaign involving Luna Moth is all about.

Phishing attacks work by spreading fake claims, but the victims don’t know that. A couple of days ago, a fake job offer cost Axie Infinity millions. Now, Luna Moth’s campaign is breaching organizations using fake subscription renewals.
Luna Moth has been around since last March, and the group has been highly active ever since. What are they after and how are they implementing their malicious practices? We’ll discuss that below.
Luna Moth – The Not So Silent Ransom Group
As with most phishing attacks, threat actors target their victims with some sort of email or text that include fake promises of anything that might be of interest to them.
They usually disguise themselves as a reputable company to ensure a 100% success rate in infiltrating the targets’ devices.
Within the text/email, the attackers include a link, which practically redirects the users to a fake webpage where they can download the intended malicious software.
Once the users download the malware, the attackers will gain full access to their data, and later threaten them to make the files publicly available unless they pay a ransom.
That’s exactly how this new group operates. On the surface, these threat actors go by the name of Luna Moth. However, based on a study by cybersecurity company Sygnia, Luna Moth has been building a reputation using the name Silent Ransom Group (SRG). They’re also tracked as TG2729.
The main focus is to gain access to sensitive information, and phishing emails are the group’s way to achieve that. By impersonating reputable brands such as Zoho, MasterClass, or Duolingo, Luna Moth managed to trick a lot of users in the past three months.
Luna Moth Phishing Attack – The Full Process
It starts with a message informing the victims that their subscription is about to end and that it will be automatically renewed within 24 hours.
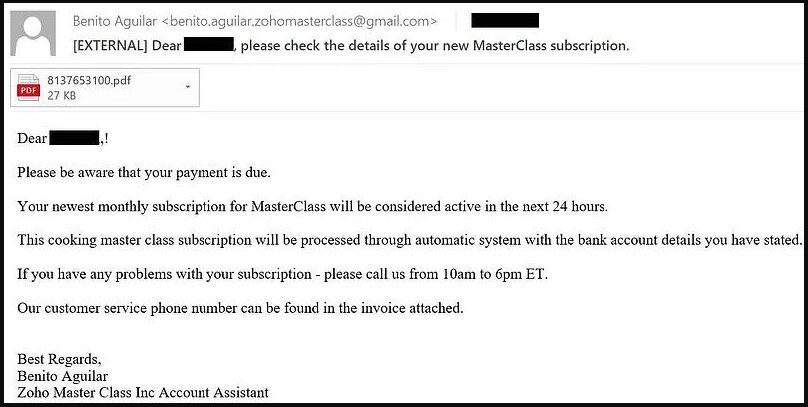
The email includes a fake invoice. This is yet another trick to show the victims that this email is as legitimate as it can be. It’ll give them the impression that the company is trying to provide them with more information.
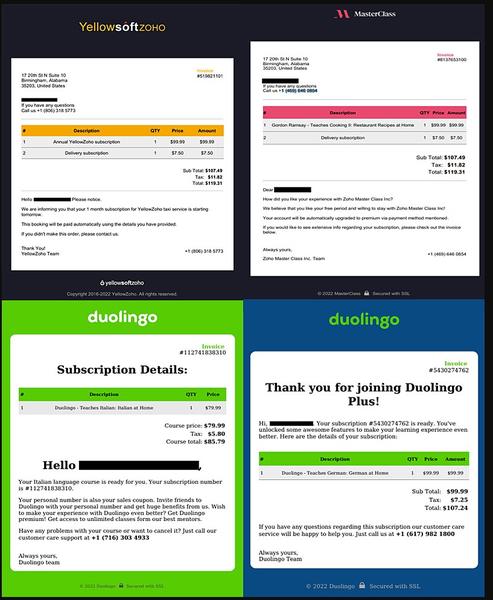
The attached invoice includes a phone number. If the victims call it, they’ll be in direct contact with the attackers. During the call, the threat actors will provide the users with the instructions to install a remote access tool on the system.
According to Sygnia, Luna Moth installs more than one RAT on the victim’s machine for redundancy and persistence.
For non-tech savvy users, this might be a normal email, resulting in a 100% successful scam. For those with a keen tech eye, the scam is obvious since the messages come from Gmail accounts.
Luna Moth Phishing Attack – A Total Data Lunar Eclipse
Phishing attacks have one thing that makes them successful, the victims’ lack of knowledge, which leads them to click on any link or follow any steps provided in the fake email.
If they avoid this step, they can prevent this whole predicament from happening. It’s easy. If you receive an email from a service you’ve subscribed to, take a good look at the writing, the email, and tone.
Moreover, if any action is required, it’s better to do it on the service’s official website directly. We don’t recommend following any link within the email.





