How You Can Fail Victim of Multiple Hacking Groups at Once
Someone penetrating your network or hacking your systems is never a pleasant experience. In fact, it’s predicted that cybercrimes will cause damages up to $6 Trillion By 2021. A single cyberattack is devastating enough. However, it can get even worse if multiple hackers exploit vulnerabilities in your cyber defenses. What are the possibilities? How can you fall victim to multiple hacking attempts? Find out in this guide.

Multiple Hackings – The Devastating Scenarios
There are basically two scenarios in which more than one hacker can gain access to your connected systems. Not to mention that they can easily plant malware on your computing devices in the process.
In the first scenario, multiple hackers and/or ill-intended actors find a vulnerability in one or more of your IT systems. That’s when they start exploiting them.
Three-fourths of firms with over 1,000 employees have been a target for cyber-criminals in 2019.
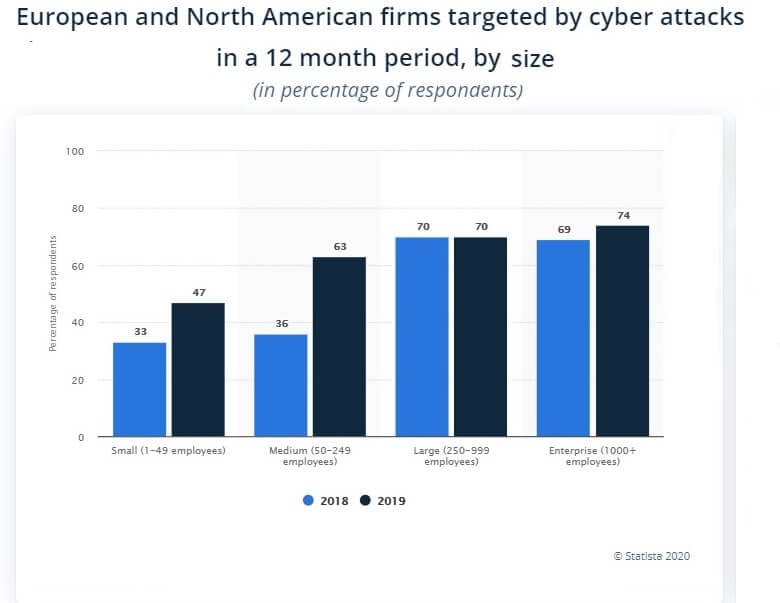
Source: Statista
Another possible scenario involves a hacker taking advantage of another hacker. This method compromises your systems and gains access to sensitive data without spending any resources.
This happens through the use of hacking tools, which are, in turn, are hacked. They enable the original malware maker to actually infect the systems of the parties that are using the software to hack you.
How Multiple Hackers Can Land on Your Systems Independently
Now, let’s see how these two scenarios could develop in practice. Multiple malicious actors penetrating your business-critical systems or snooping on your online connections is a very likely scenario if you leave unaddressed one or more critical vulnerabilities.
The same applies to not updating and patching your systems on a regular basis. We’re referring to when you are using a software that has security holes such as nonsecure firmware.
If such security vulnerability exists, rest assured the hacking community will be aware of it. That’s when more than one hacking group or an individual hacker will try to exploit the vulnerability.
This is made by simply scanning the online ecosystem for the presence of traces from this software. Evidently, it needs to be connected for the vulnerability to be exploited.
A Common Scenario
This one involves a system administrator leaving vulnerable communication ports open on one or more machines within a network.
In fact, any communication port on any of your computers can be vulnerable to a certain attack type. Hackers routinely scan the entire Internet for such open ports on both servers and end-user computers.
This explains why both individual and corporate users still fall victim to ‘outdated’ malware that is roaming the Internet since the early 2000s.
In most cases, these are malware tools that run automatically and connect to a remote command-and-control center once they find an open port or a specific configuration vulnerability.
Furthermore, these are both basic yet fundamental hacking tools that some underground groups operate. That’s why there is a good chance that more than one hacker will detect such an exploitable vulnerability in your systems.
These hacking groups, however, are in fierce competition to get access to your precious data and penetrate your communications, so they are hacking each other as well.
Hackers Infect Hackers to Gain Access to More Systems
Hacking computer systems for profit or in order to gain other benefits is a crime by any standard. But it is not as easy to hack the average computer system as it may seem on the surface. The average business user tends to have at least a firewall and a reliable antivirus suite.
The most lucrative cyber-attacks are ones that target a specific business, government agency, or municipality. These attacks, in turn, involve more than one hacking tool and can be a costly business. It becomes more expensive if the victim happens to have proper cyber defenses in place.
That is why a number of more advanced hacking groups took it a bit further. They have started planting malware inside the very malware that is used to hack a victim’s systems.
This way, hackers gain access to other hacker’s systems that, in turn, eventually gain access to corporate or personal computing systems and networks.
Hacking the Hackers
For instance, security researchers Cybereason are reporting about a year-long campaign during which hackers are planting njRat, a Remote Access Trojan virus, on multiple hacking tools that end up at other hackers all over the world.
As a result, if one of those hackers manages to penetrate your computing systems, those behind the widespread campaign will also get access to your systems.
This is an entirely new attack vector, which is aided by the proliferation of hacking tools and the emergence of hacking-as-a-service offers on the underground Internet.
Thus, a hacking group that has more resources and know-how can effectively penetrate the systems of other hackers. After that, they gain control over numerous systems hacked by others, saving both resources and expanding their network of remotely controlled machines from which they can also extract valuable, sensitive data for use in further attacks.
A specific scenario, related to the above, is the existence of secret backdoors in software apps whose proprietary software code does not allow independent researchers to audit it.
There are little to no confirmations for such backdoors in popular business software. However, it is a viable possibility, and it is a chance higher than zero for an organization to run such software.
It doesn’t matter if a software vendor has placed such a feature for the purpose of remotely configuring the app or if they planted it under orders by a government; you end up with a built-in tool for someone to snoop on your communications and/or access the data you consider private.
Concluding Words
The war for gaining access to digital assets and respectively protecting digital assets from unauthorized access is intensifying as the recent news about hackers infecting other hackers’ system suggest.
You should take action once you experience any sort of malicious attacks against your systems. Analyzing the “attack vector and the possible origin of the attacks” doesn’t cut it anymore. You should also check if the attack involves multiple hacking parties.
A clever hacker can even intentionally uncover an attack from a competitor, which you are able to stop and fix. However, this may leave another piece of undetected malware to run on your systems. Be careful, and keep a keen eye on your devices. If you have any more questions, drop them in the comments below.





