Targeted Hacking Attacks Can Penetrate Any Computer System
We all know that the internet has made the world much smaller. However, it has also made our personal information a lot more vulnerable. In 2018, cyber-criminals managed to steal close to 450 million consumer records containing sensitive personal information. This is a massive number of compromised personal records. But what is more alarming is the fact that this is a 126% growth as compared to 2017. Can you imagine such a record within a single year? It doesn’t matter what motivates a hacker. Whatever the case is, the results can be devastating. Targeted hacking attacks are dangerous which leads us to this guide. Proceed and learn everything about them.

Targeted Hacking Attacks Can Penetrate Any Computer
Sophisticated Hacking – The Rise of the Two Forms
Organizations of all kinds and sizes should prepare to withstand targeted attacks and prepare well. If you are running an expanding and successful organization, someone will be after you trying to steal your data or snoop on your professional communications.
The same is true to an even greater extent if you hold a middle management position within such an organization. Also, be on constant alert for hacking attacks even if your business is small.
Municipalities, hospitals, and universities around the globe are also a target for hackers. By “targeted,” we mean attacks designed to penetrate a specific computer system, not malware roaming freely online and looking for random prey.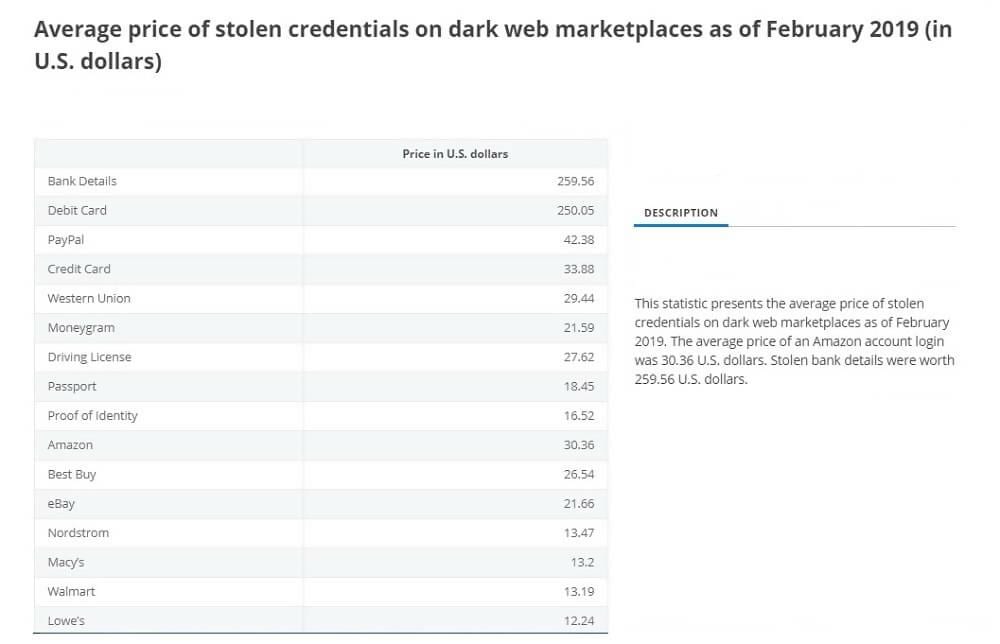
For good or for bad, targeted hacking attacks are getting increasingly sophisticated. To demonstrate, we’ll be talking about two main ones – social engineering and custom-made malware.
Social Engineered Spear Phishing
 One of three Americans has been a victim of cyber-attack. In fact, almost 65 percent of hacking attacks are against small and medium-sized businesses, a report by IT security consultants Kelser Corporation reads.
One of three Americans has been a victim of cyber-attack. In fact, almost 65 percent of hacking attacks are against small and medium-sized businesses, a report by IT security consultants Kelser Corporation reads.
Although the numbers are alarming, these are not targeted attacks with the bulk part of those falling victim to malware being hit with various types of Trojan viruses and other banking malware.
Creators of such viruses, including ransomware virus families, create the malware and let it circulate the online space in search of a victim with little to no supervision.
Spear phishing attacks are another beast. Back in 2015, the world witnessed the first targeted cyber-attack that led to power outages and affected up to 225,000 customers in Ukraine.
How Did It Happen?
This very complicated targeted attack involved specialized malware such as Black Energy 3 and the use of a combination of VPNs and internal communication tools to penetrate the command-and-control dashboard of the energy operator.
But as sophisticated as these attacks had been in terms of malware used, it started simple. How? By sending a meticulously crafted spear-phishing email message to the inbox of a “low to middle-level” technician who used to work for the Ukrainian power grid operator.
Attackers used a combination of two phishing techniques that persuaded the victim to share information by convincing him that the malware-infected email message is coming from a trusted contact.
They were not after a C-level executive, in this case. Any employee with credentials to log in to the power grid’s network was a target worth exploring. The hackers even profiled former company employees to craft a message the target will open, read, and respond to.
Whether to place a malware link into the spear-phishing messages was up to the hackers to decide, depending on the response by the targeted person.
Does It Take Time?
 To perfect it, yes. It is a highly sophisticated method to penetrate an organization. First, you should be patient enough to research potential contacts within the company.
To perfect it, yes. It is a highly sophisticated method to penetrate an organization. First, you should be patient enough to research potential contacts within the company.
Second, you have to profile them based on information available on social media and other public and private databases. Consequently, you can convince almost anybody that he/she is getting legitimate emails from a colleague or partner.
It is only a matter of time for them to get access to shared credentials or hack the victim’s email. Next, they’ll continue penetrating the organization’s networked systems even further.
In any case, you need specific software tools to pass through the cyber defenses once you have low-level network credentials.
Hackers Now Make Custom Malware to Penetrate Your Network
 If you thought “getting the credentials” for a targeted networked system was terrible, think again. Obtaining this information was just the beginning. The hackers use even more sophisticated attack methods to penetrate the system further.
If you thought “getting the credentials” for a targeted networked system was terrible, think again. Obtaining this information was just the beginning. The hackers use even more sophisticated attack methods to penetrate the system further.
The Australian National University learned it the hard way after someone hacked their systems and gained access to data records going back to 2000.
Their report on the targeted data breach is even more amazing as there is no clear motive behind the attack. It was only someone with extensive skills testing penetration techniques to use against a far more significant target.
In this case, the hackers went on to tweak the signatures of common malware. The plan is to plant it on the university’s systems undetected.
Then, they assembled a sort of their own network of malware tools operating inside the ANU network and using virtualization software to emulate legitimate workstation and server behavior.
It Gets Darker
What is more, the hackers did not extract sensitive data by using application-level access. No, they did that by extracting data directly from the underlying databases. Such a method bypasses app-level logging and is harder to detect by common cyber-security tools in place in most organizations.
As a side gig, the penetrators attempted to disable ANU servers’ spam filters. This also hints at someone experimenting. It’s not a kind of action that gives the penetrator any further benefits or advantages.
Australian security experts and ANU’s cyber-security officials openly admit they have no clue who is the actor who infiltrated their systems. Neither did they figure out what motivated attackers to steal 19 years’ worth of data. The data consists mostly of files involving information about human resources, financial management, student administration, and “enterprise e-forms systems.”
What if the hackers were after access to data about former students? What if these students are now being profiled as potential targets for future spear phishing attacks?
Is There A Bottom Line Though?
In short, we ask ourselves this: Will the trend go downwards? Doubtfully. The problem is that cyber-attacks are getting more “personal” and more sophisticated.
This leaves cyber-security experts scratching their heads how to protect you against concerted hacking attempts by government actors who are after your data.
Not to mention the cyber-criminals who look for innovative ways to install ransomware on your computing systems. The bottom line is, stay alert at all times. You don’t want your private information falling into the wrong hands.
Targeted Hacking Attacks – Concluding Words
Both nation-state and organized-crime hackers have the tools and the motivation to compromise any given computing system through the means of a complex targeted attack.
It is not important whether an attacker is politically or financially motivated. What’s important to address is that the outcome is destructive. Did you learn something new today? Is there anything more I can add? Let me know in the comments below.





