The New Phishing Attack – Impersonate Pfizer, Inject Malware
Battling constantly surfacing new variants of the Coronavirus is a hard task on its own let alone worrying about cyberthreats that come with it. The fear of the galloping spread of new COVID-19 variants has made it very easy for threat actors to give a sense of urgency in the new campaign involving Pfizer phishing emails.

As a globally known pharmaceutical company that has one of the most effective mRNA vaccines around the world. Unfortunately, the company’s reputation came back to haunt new individuals and companies.
Unfortunately, the threat actors are exploiting the brand’s name to steal business and financial information from victims. What is this about? How are the emails distributed and what do the attackers gain? Find out in the following article.
Pfizer Phishing Attack – An Unwanted Injection
Phishing emails have been a main type of attack for threat actors lately. You get an email from a well-known company, and minutes later, you become the latest victim in the scheme.
Basically, impersonating one of the biggest pharmaceutical companies could make the job even easier. That’s exactly what the hackers are looking for – easy targets.
According to researchers from INKY, the phishing email campaign started around August 15, 2021. This time around, hackers are being very careful and crafty in their methods.
They’re combining “clean” PDF attachments with newly registered domains that look like official Pfizer online pages. The attackers have thought it through very carefully.
They created the domains through Namecheap. Why? Because it accepts cryptocurrency as a payment method. In other words, the perfect way for them to remain anonymous. INKY found some of the websites the attackers are using. Here they are:
- pfizer-nl[.]com
- pfizer-bv[.]org
- pfizerhtlinc[.]xyz
- pfizertenders[.]xyz
The first one clearly reflects a website in the Netherlands. This can easily trick victims mainly since the Pfizer organization has an office in the country.
As we mentioned, the hackers send emails with a sense of urgency, and according to INKY, the subjects mostly reflect the following:
- RFQ.
- RFQ URGENT CARE.
- Pfizer Request For Quotation.
- Request for Supply.
- Invitation.
- RFQ URGENT.
- Invitation to Bid.
- Request For Quotation.
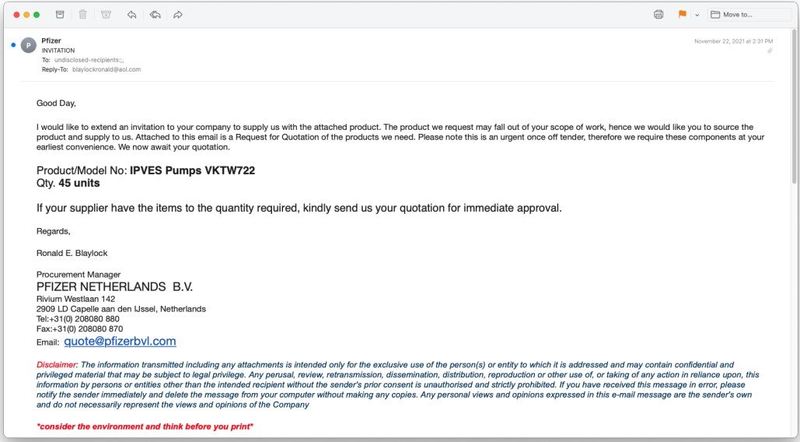
The following email includes all the information users need to know about the phishing attack. Not to mention the direct approach these attackers are practicing.
Again, we should note that urgency is a phisher’s ultimate approach to perfect the attack. It forces victims to make ill-considered decisions.
The emails include a very professionally crafted 3-page PDF. It includes everything the victim needs to know about due dates, payment terms, and other factors that show legitimacy.
During the process, the emails prompt the receiver to send his/her quotes to the provided domain addresses. For example, users might find one such as this quote@pfizerbvl[.]com.
Pfizer Phishing Attack – Reading Between the Lines
It’s still unclear what the motivation behind this attack is. However, the threat actors did include payment terms in the PDF, which indicates that, at some point, recipients might be asked to submit their banking information.
Now, once the company/organization shares its payment info, the attackers can start planning for future BEC campaigns. Who would be the target then? Well, the company’s customers of course.
Moreover, not asking for personal information from the start might seem like a safe approach to some recipients. In fact, they might lower their shields for further questions during the process.
Be careful. Replying to these emails will get you deeper into the scheme. The attackers are preying on your thoughts of signing a deal with a well-known firm.
Pfizer Email Scheme – A Malicious Dose
Whenever you receive an email from any source, be it a reputable company or not, always make sure to contact them through their regular numbers.
Never share private information or click on any link unless you’re sure of the source. If not, it’s better to visit the company’s official website manually without having to use the provided link.
You always have to keep an eye on such attempts as they’re on the rise. Be careful and stay safe.