A New Windows Flaw, A New Target for QBot
The QBot malware seems to be on a roll these past couple of months, making a name for itself in the industry. This banking trojan with worming capabilities has achieved a lot in the past and recently teamed up with one of the rising ransomware operators – Black Basta. Now, threat actor TA570 is exploiting Windows’ Follina CVE-2022-30190 security flaw and infecting recipients with Qbot.

QBot works using phishing campaigns, where victims receive fake emails with a malicious link inside. This time around, the attacker is using hijacked email thread messages that eventually end up with malicious Microsoft Office .docx documents.
QBot execution has evolved, and apparently, TA570 knows how to elevate the malware’s capabilities. How does this work and to what end? We’ve discussed everything in the following article.
QBot Hits Again: A Windows Flaw that Costs A lot
Follina is a critical Windows zero-day vulnerability, which everyone is waiting for Windows to fix. Unfortunately, there are some entities that benefit from such flaws, particularly hackers and other kinds of threat actors.
Security research firm Proofpoint has been monitoring this large cybercrime threat actor since 2018. Now, it’s 2022 and this attacker is still on the loose causing so much damage using the QBot malware.
The CVE-2022-30190 is being actively exploited using phishing attacks. That’s not new as QBot is known for being distributed through phishing emails.
Proofpoint saw #TA570 exploiting CVE-2022-30190 to deliver #Qbot malware. Actor uses thread hijacked messages with HTML attachments which, if opened, drop a zip archive.
— Threat Insight (@threatinsight) June 7, 2022
Once the victims click on the attachments, they will download ZIP archives containing IMG files. Finally, they’ll find within the IMG 3 different file types in the form of DLL, Word, and “shortcut.”
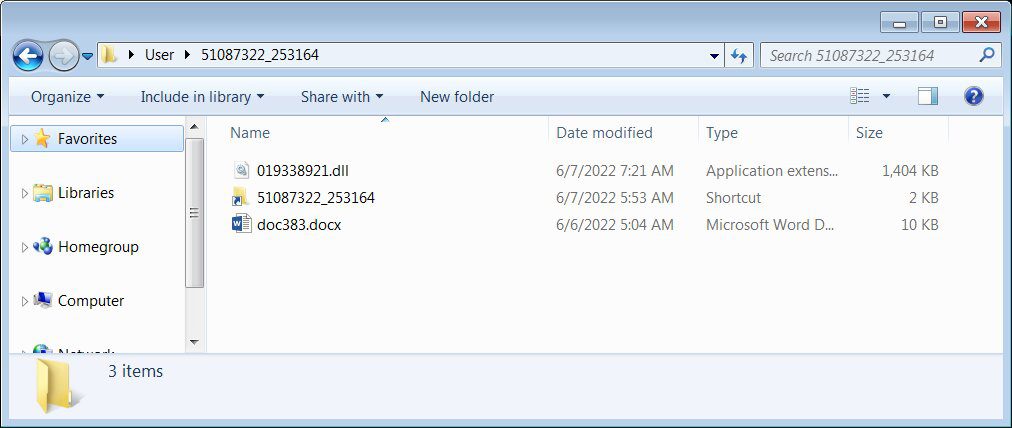
As seen in the image above, there are three files with different objectives. The shortcut file is the one that directly loads QBot to the system. However, what really exploits the Follina flaw is the .docx document.
Once the users open it, PowerShell code will run and downloads a different Qbot DLL payload. Apparently, TA570 is using two separate ways to infect the users’ devices.
This only means that the threat actor is running an A/B testing campaign to see which tactic would get them the best results and fulfill the task. You can see further information about additional indicators for this campaign by checking a report conducted by malware analyst ExecuteMalware.
QBot Strikes Again – Final Words
QBot has been around for quite some time now, attacking Windows devices for at least 15 years. The information stealer can do a lot of damage, including stealing banking credentials, financial data, as well as personal information.
Not only that, but it can also deploy Cobalt Strike beacons in the process and aid ransomware operators fulfill their tasks easier.
QBot can infiltrate your systems through phishing attacks. In other words, you can avoid it by staying vigilant all the time. Never click on a link that seems out of place, you’ll be saving yourself a lot of trouble in the process.





