Android Malware Revive – Using Two-factor Authentication Maliciously
In the past few months, the number of online data breaches, RAT attacks, and phishing campaigns has increased drastically, showcasing the abundance of cyberthreats. One of the best ways to fend off such breaches is by enabling 2FA (Two-Factor Authentication). Unfortunately, it’s also one of the best ways to trick victims into lowering their guard – enter Android malware Revive.

The Revive malware earned its name as it’s one malicious software that definitely shows determination. Using a phishing scam involving a 2FA application, Revive operators are targeting BBVA bank accounts in Spain.
The entire process starts with this scam, but the question is: How is it carried out? We’ve discussed everything in this comprehensive article.
Android Malware Revive – 2FA to Fall As Prey
Phishing attacks have skyrocketed in numbers during the first half of 2022, making regular occurrences in so many different forms.
According to recent studies, one in every 99 emails is a phishing email. The study also states that attackers send over 3.4 billion fraudulent emails on a daily basis.
Threat actors prey on the victims’ fears and needs. These two factors urge the user to act before thinking, especially when it comes to their online security.
Now, the people behind Revive are targeting users in Spain who wants to add an extra layer of security to their BBVA bank accounts with a 2FA tool.
Through a website that sports a professional appearance, the attackers try to convince their victims to download an application that is supposedly a 2FA tool. With it, they can enhance their account’s safety – supposedly.
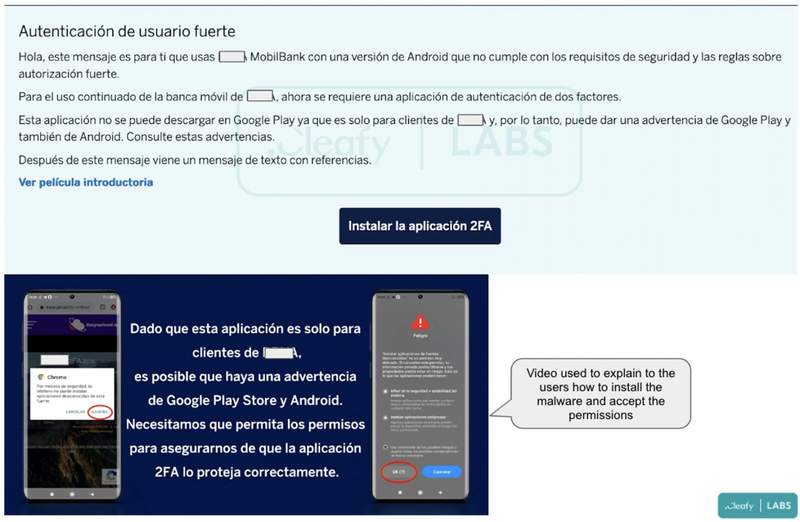
The phishing scam tells the user that the 2FA functionality in the actual bank app needs an upgrade for a safer approach. It prompts the user to download this fake tool to benefit from a fully operational 2FA mechanism.
The Malicious Permissions
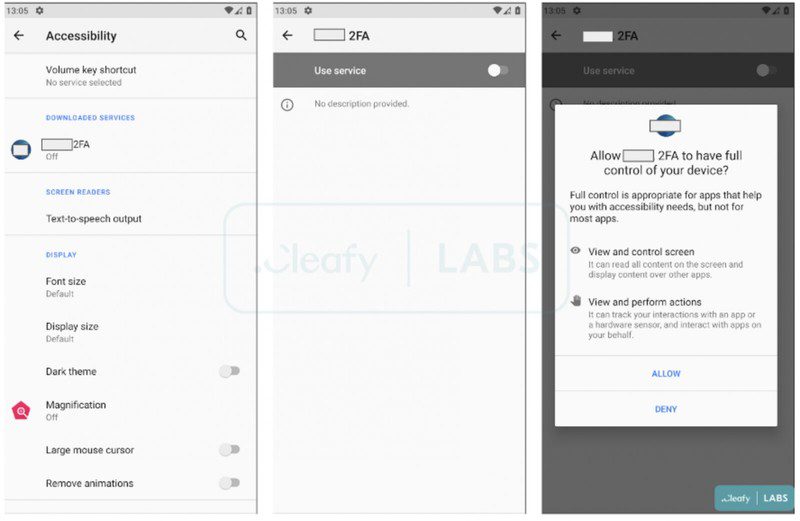
Once the target launches the installation file, the malware requests permission to use the Accessibility Service. In other words, asks for complete control of the screen.
Not only that, but if the user allows it, the malware will have the ability to tap the screen as well as commit navigation actions. This can be seen in the image below, courtesy of Cleafy’s full Revive report:
The user will also get a request to give the app permission to SMS and phone calls. This won’t look weird to them as it’s normal for a 2FA utility.
If allowed, the malware will stay in the background and commit all of its malicious practices. It will record everything the user inputs and send it directly to the C2.
That means when the users enter their banking credentials, the threat actor will be recording and receiving everything, gaining access to the accounts in the process.
Revive – From Spyware to Banking Trojan
According to Cleafy, every aspect of the malware clearly shows that it’s still in an early development phase. Revive got its name due to the fact that it keeps restarting in case the malware stops working.
Through dedicated websites, the malware is targeting Spanish citizens and harvesting their banking credentials. In other words, what starts with phishing can be avoided.
Users can easily halt downloading any application from unknown sources. Not only that, but they also have to make sure that the required permissions are reasonable. That way, they can avoid this entire predicament.





