RomCom Returns: Google Ads Utilized Once More
Ever since 2023 kicked off, threat actors started coming up with new ways to target victims. Their most common tactic would be creating fake websites and apps, tricking users into downloading and launching malicious installers. The latest incident involves the RomCom malware – one very dangerous backdoor lurking around disguised as popular apps.
RomCom is distributed through employing phishing or social engineering to approach targets. Unfortunately, this tactic is still working, especially since the threat actors are masquerading as very in-demand apps and websites.
Recently, Google advertisements have become the first taken step in malicious campaigns, and it’s no different in this one.
But the questions remain: What can RomCom do? What websites is it impersonating? Who’s behind this malicious backdoor? We’ve answered everything below.
The RomCom Campaign – Fake Apps Everywhere
When it comes to cybercrime, threat actors must elevate their techniques to ensure higher success rates. If they keep using their outdated utilities, they won’t keep up with the latest updated security measures.
Phishing attacks are the most effective way to infiltrate a target’s device, as the victim can easily fall for the trick if it’s convincing enough.
And what better way to trick them than with Google itself? Threat actors have managed to utilize Google ads, in which their fake websites are presented at the top of the search results. This is exactly how RomCom is being delivered.
RomCom has been around for some time, spreading its activities across multiple platforms in so many ways. Not only that, but it doesn’t only focus on a specific region – its activity has been monitored through various countries.
In this particular campaign, RomCom is impersonating legitimate software such as Devolutions’ Remote Desktop Manager, Gimp, Go To Meeting, WinDirStat, AstraChat, and System Ninja.
What’s worse is that it’s even masquerading as the most popular platform in recent times, ChatGPT. This AI ChatBot harnessed millions of users in its first week only.

According to the report published by Trend Micro, this campaign is mostly targeting users in Eastern Europe, which shows a slight shift in the malware’s behavior. However, its capabilities and execution method remain as risky as always.
The Infection Process
The fake pages include MSI installers that impersonate the promised app. Unbeknownst to the victim, these installers are actually trojanized with a malicious DLL file (“InstallA.dll”).
Once launched, three other DLLs would be extracted onto the victim’s %PUBLIC%\Libraries folder.
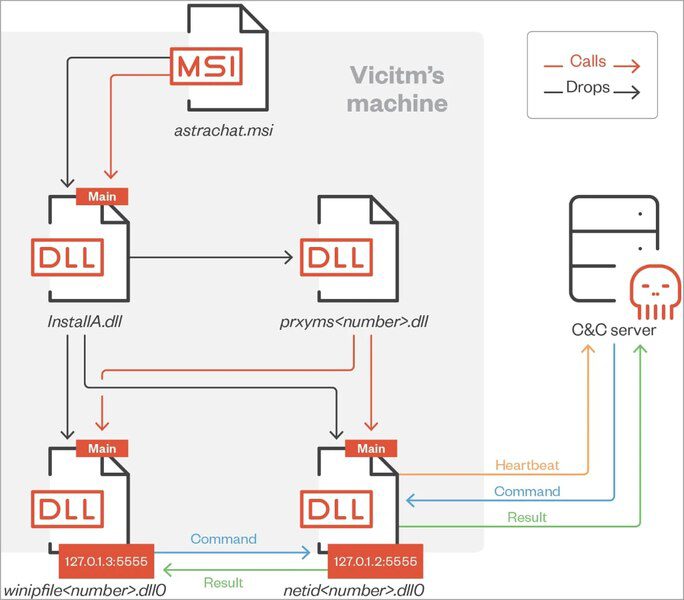
Once everything is in place, further commands can be pushed on the device, allowing actors to extend their attack using more and more utilities:
- Start cmd.exe
- Drop additional payloads (Screenshot tools, wallet-stealing tools, etc…)
- Harvest sensitive information.
- Use SSH to set up a proxy.
- Keep the malware updated.
- Send files to the attackers’ server in compressed form.
- Run AnyDesk on a hidden window.
Trend Micro also states that the creators of this malware operate using VMProtect software for code protection and anti-VM capabilities.
In other words, everything about RomCom is highly dangerous, and users should make sure not to fall for such phishing tricks even if they’re at the top of their Google search results.
Google Ads Utilized Maliciously – Stay Vigilant
RomCom has been monitored in the past, particularly attributed to the Cuba ransomware affiliate Trend Micro named ‘Void Rabisu’ to track their campaigns.
Now, in this campaign, the threat actors are using very popular applications to target a wide range of users all over Eastern Europe.
When you stumble upon an ad for an app you’re searching for, it’s always recommended to use the actual URL, not the “Ad” version.
This is the perfect example of how Google Ads are being utilized by threat actors. Stay vigilant and be safe.





