SeaFlower Strikes – iOS and Android Crypto Users Beware
Cryptocurrency has become very popular in the past couple of years. This type of payment proved to be a reliable, long-term store of value that grants its operator total anonymity. However, as its popularity spikes, cybercriminals have deemed it a good source of income. Apparently, a threat actor that goes by the name of SeaFlower has been targeting Android and iOS users in an attempt to drain their crypto funds.
The attacker has the technical sophistication to perfectly mimic official cryptocurrency wallet websites. That’s more than enough to trick users into falling for this trap.
Based on research, SeaFlower seems to be of Chinese origin. So, what would we expect from this malicious group? What cryptocurrency applications are being targeted in this campaign? We have everything you need to know in the following article.
Backdoored Web3 Wallets – A Not So Delicate SeaFlower
As mentioned, one of the main reasons to use cryptocurrencies is to maintain your anonymity while making any kind of purchase. There are several cryptos that promise the highest levels of privacy during your transactions.
However, we also stated that as the popularity of this payment method rises, the percentage of attracting cybercriminals also increases. A while ago, Trezor users were targeted by a malicious campaign, which injects a crypto stealer into their devices.
Now, SeaFlower’s attack seems to be more broad as it’s attacking its victims using several fake applications. Before we present the entire operation, here’s what Confiant’s Taha Karim stated in his report:
“SeaFlower doesn’t alter the original functionality of the wallet in any way but adds code to exfiltrate the seed phrase, and does it using different techniques increasing in complexity.”
To sum it up, SeaFlower is targeting applications such as Coinbase Wallet, MetaMask, TokenPocket, and imToken. The entire operation begins with cloned websites.
When the user visits those websites, the page prompts them to download trojanized versions of the wallet applications. The pages look exactly the same as the original counterparts, but the attackers have tampered with the code to exfiltrate the seed phrase to a remote domain.
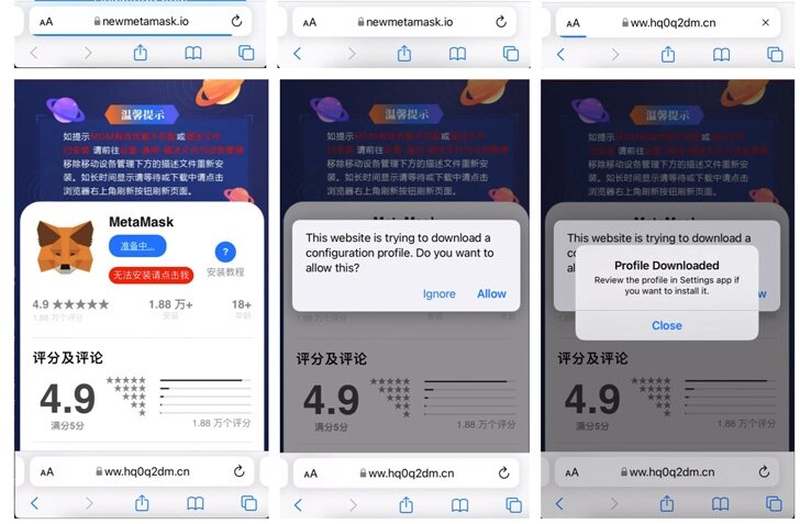
The images above represent an example of one of the apps – MetaMask. As seen, it has “CHINESE” written all over it.
According to the research, the macOS usernames, source code comments in the backdoor code, and the use of Alibaba’s Content Delivery Network (CDN) indicated the actors have some sort of a relationship with a Chinese Entity.
A SeaFlower with Remarkable Phishing Techniques
When we speak of phishing, we directly think about emails, ads, and malicious videos on social media platforms. This represents what a typical phishing campaign is all about.
However, SeaFlower took a new route to “phishing” and it’s using none of the above. Instead, SeaFlower makes use of SEO poisoning techniques on Chinese search engines.
We’re referring to the likes of Sogou and Baidu where search terms such as “download MetaMask iOS” end up as download pages on top of the search results page.
Not the real thing, but the trojanized versions of the app. These are some high-level capabilities that make SeaFlower a force in the cybercrime industry.
Give Us Your Crypto – A Flower in a Malicious Sea
Threat actors are increasingly setting their sights on popular Web3 platforms, which means you have to be extra careful when downloading any app over the web.
Why would you want to use a website to download them? If you can’t find them in your native app store, don’t head elsewhere, especially when Chinese writing is all over the page.
Stay vigilant and be careful. It’s your earnings that are at risk. This is a big deal and you should always try to protect it, not jeopardize everything with a single click.





