Trezor Phishing Attack – Fake Breach, Real Crypto Stealer
In the world of cybersecurity, receiving a breach alert always demands attention, as well as immediate action. However, if this alert happens to be fake and “phishy,” drastic consequences are at hand. Unfortunately, this recently happened to Trezor users, where threat actors sent fake data breach notifications to steal cryptocurrency wallets.

The attack criterion is not new, as we’ve seen it before. But Trezor is used by a lot of people, and the damage can be huge.
How are the threat actors implementing their plan? What are the users doing wrong? Find out in the following article.
Trezor Phishing Attack – Fake It till You Make It
Phishing attacks are rising in popularity nowadays, targeting users on whatever device that can connect to the internet. A while ago, threat actors used fake Azure Static Web Pages to infect users’ operating systems.
Now, a new phishing attack revolved around none other than Trezor – a hardware cryptocurrency wallet that lets customers store their crypto assets offline.
As we mentioned, this is isn’t the first attempt on victims using fake data breach emails. In the past, a data breach on the Ledger website occurred, and users’ contact information was stolen.
With this information, Ledger users started receiving fake emails about a new data breach from Ledger, resulting in cryptocurrency theft at the end of the line.
This time, no website was breached, but a Trezor wallet mailing list was (by an insider), which gave the threat actors everything they needed to target victims.
Any tool requires some sort of password/recovery upon setting up. With Trezor, new users will obtain a 12 to 24-word recovery seed that helps them recover their wallets if their device is stolen or lost.
If this falls into the wrong hands, well, you know the rest. They can easily gain access to the wallet and its stored cryptocurrencies.
The Phishing Process
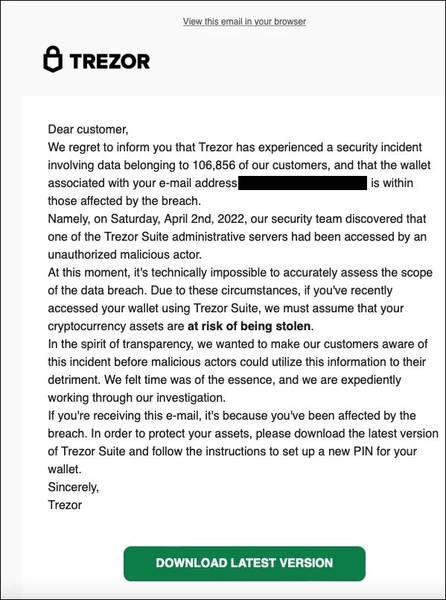
Now, since the threat actors have Trezor’s wallet mailing list, they can easily start sending their fake emails. Unfortunately, that’s exactly what happened, as the users did receive such emails.
“We regret to inform you that Trezor has experienced a security incident involving data belonging to 106,856 of our customers, and that the wallet associated with your e-email address [email here] is within those affected by the breach.”
Once the victims receive this email, the threat actors prompt them to download the latest Trezor Suite to set up a new PIN on their hardware wallet.
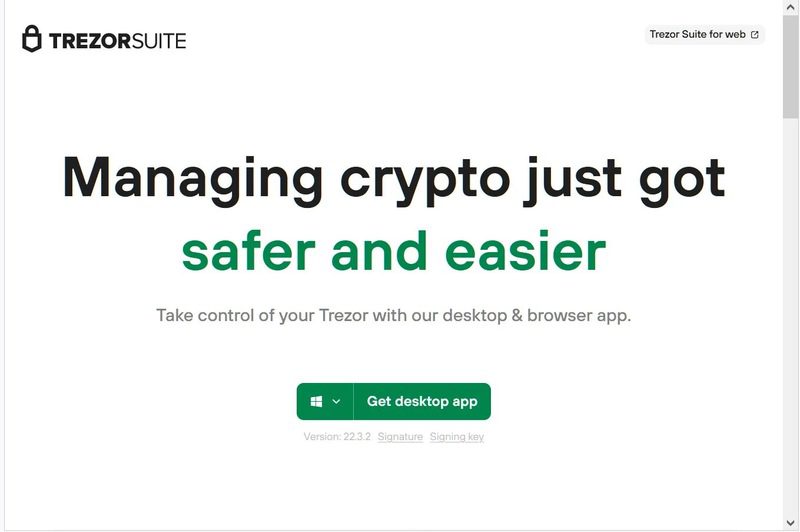
Yeah, you guessed it, that’s the key to infiltrating everything. Once the users press the ‘Download Latest Version’ button, they’ll be redirected to a phishing site, “suite.trezor.com.”
This is another trick crafted by the threat actors to resemble the actual thing. They’re using Punycode characters to hide the actual domain name suite.xn--trzor-o51b[.]com and replace it with the one we mentioned above.
The App!
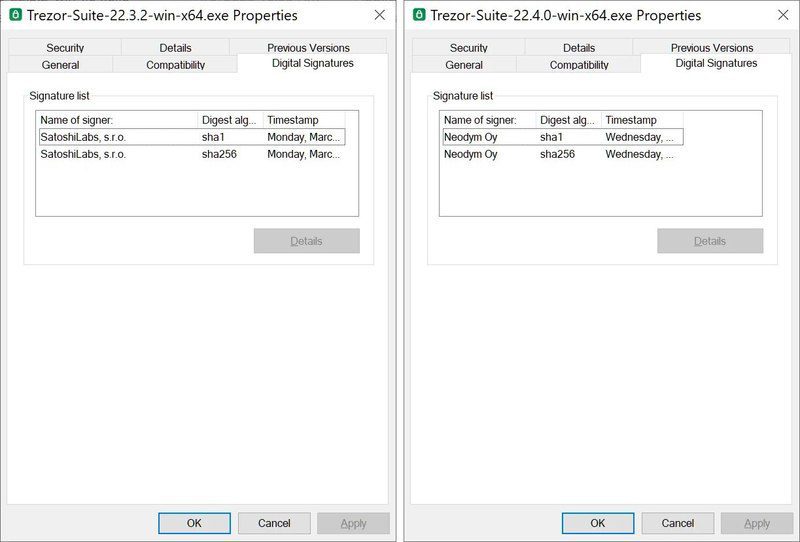
When the users click on”Get Desktop App,” they’ll download the fake suite’s installer. Now, since Trezor Suite is Open Source, any developer can tamper with codes and create some sort of a replica.
As you can see below, both apps resemble each other. However, if you look closer, you can see that the legitimate Trezor Suite application includes a certificate for “Satoshi Labs, s.r.o.”. The fake app version, however, has a certificate from “Neodym Oy.”
In fact, the fake app also has the same “phishing warning” sign the original presents once launched. Users can clearly see it on the top of the application.
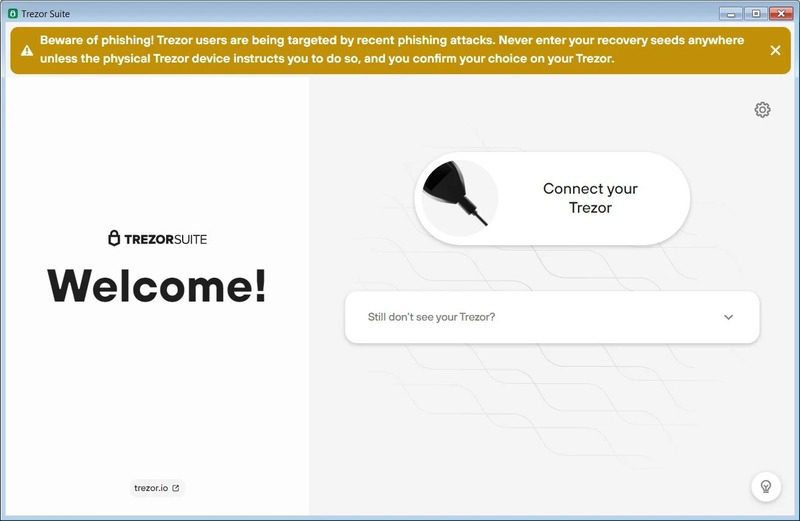
Finally, once the users click on “Connect your Trezor,” the app will ask them to enter their 12 to 24-word recovery phrase, which goes straight to the threat actors. As a result, they’ll import the recovery phrase into their own wallets and harvest the victims’ cryptocurrency assets.
Trezor Phishing Attack – Very Fake, Yet Believable
Using warning emails has proven very effective when it comes to anything “online.” Previous attempts include Twitter and Instagram, where users received warning emails as well, threatening to take away their “Verified Badge.”
Now, with emails informing victims of a data breach, things can get a bit more dangerous. The threat actors are playing on your fear factor, and it’s mostly working.
Whenever you receive such emails, make sure to check the source’s official website. If any data breach incidents have actually occurred, their website would definitely state it.
Always try to stay vigilant when downloading anything. Even if you trust the source of the email, make sure you go to the official source and get your file there.