Sharkbot Swims Swiftly within Play Store’s Library … Again!
Google Play Store is having a very bad year when it comes to malware infiltration, especially that involving Sharkbot. The infamous banking trojan is back again, but this time, it comes in the form of harmless “File Manager” applications.

Android users don’t seem to have any time to recover from one campaign to receive another. Cybercriminals around the world have come up with several new techniques to bypass the store’s security measures – and they’re succeeding.
Evading detection when submitted on Google Play can come in different ways, but with Sharkbot, it has become very common. Here’s everything that’s been going on with this malicious attack.
LACK in Security – Back with Sharkbot
As we mentioned, Google Play Store had a rough year as it doesn’t seem to be able to keep up with continuous cyberattacks of this caliber.
A few weeks back, the Android store also saw apps masqueraded as popular lifestyle apps. These fake tools were used to spread the Xenomorph banking malware – a dangerous trojan that does a lot of damage once it takes root.
Sharkbot is a banking trojan that can easily steal credentials by presenting fake login pages. Once the user submits the needed information through (What they think is their banking application), the malware will harvest the credentials and send it to the threat actors.
The new campaign sees fake File Manager apps spreading the malware. Google Play Store did not detect the malware as it’s not technically present.
In other words, the apps don’t carry malware. Instead, they fetch it later from a remote resource once they’re installed on the device.
The first application goes by the name of X-File Manager. It has more than 10,000 downloads, which shows how big this campaign is.
The other application used in this campaign is ‘FileVoyager.’ As seen in the image below, this fake file manager has more than 5000 downloads on Google Play Store.

What makes this campaign very effective is that the applications are file managers. In other words, asking for any kind of permission would not make the users suspicious at all.
Sharkbot targets banking apps, and according to analysts at Bitdefender, this list represents all of the targeted applications:
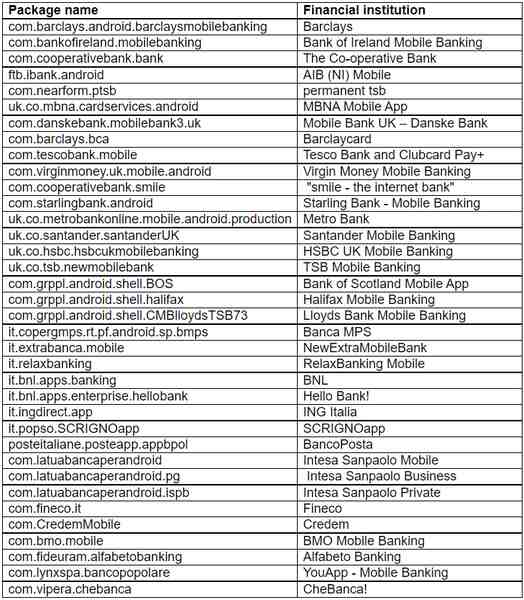
The applications have been removed from Google Play Store’s library. However, the damage has been done as can be seen in the number of downloads. What’s recommended now is an immediate uninstallation.
Play Store Struck Again – Sharkbot’s Perfect Evasion Technique
Such incidents are happening regularly with Google Play Store. In fact, this is not the first time that Sharkbot managed to infiltrate its library.
Aside from uninstalling the apps, we highly recommend downloading a reputable antivirus. That way you can detect any irregular activity on your device and sniff out any malware residue.





