Shutterfly Takes a Hit – Conti Ransomware Strikes Again
Injecting ransomware is now a state-of-the-art type of cyber attack that most hackers are using. Aside from gaining sensitive information, they get to ask for a certain ransom in exchange for unlocking the encrypted material.
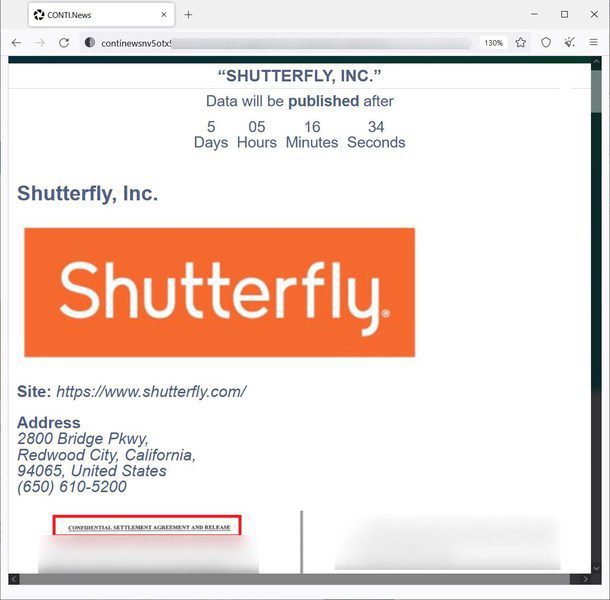
Recently, Shutterfly – the photography and personalized photo giant fell victim to a very dangerous ransomware attack – Conti. The hacking group claims to have encrypted over 4,000 devices and 120 VMware ESXi servers, which is huge, compared to other ransomware attacks.
To make it worse, the group is demanding millions of dollars as a ransom. This is a big hit for Shutterfly and all the affected victims. The question is: How did this happen? Find out in the article below.
The Conti Ransomware – Shutterfly Hit Hard
Conti is not new to the scene. In fact, it has hit several big names in the past. A while ago, the major US cable provider, Frontier, fell victim to the ransomware attack that affected over 80,000 government employees.
Now, the attack involves one of the biggest photography companies in the world – Shutterfly. This company offers services through several brands, including GrooveBook, BorrowLenses, Shutterfly.com, Snapfish, and Lifetouch.
Unfortunately, the attack doesn’t just involve Shutterfly. Usually, attackers don’t directly start the encryption process. Instead, they take their time, harvesting data and documents for several days or weeks.
Since there are more than 4000 devices affected, we can assume how much data the attackers got their hands on. They could easily blackmail targets and ask them to pay a ransom.
If they don’t comply, the attackers might publicly release or sell the data to other hackers. Sadly, it doesn’t end here.
The Conti group is very proud of its accomplishment. They even created a private Shutterfly page that shows the data leak.
This page contains the files and documents they got a hold of during the attack. If Shutterfly doesn’t pay the ransom, the attackers would make the page public.
According to Bleeping Computer, the page includes very sensitive information. That includes login credentials for corporate services, legal agreements, bank & merchant account info, and spreadsheets.
Unfortunately, it doesn’t stop here. The page also shows customer information, including the last four digits of credit cards.
Moreover, the attackers also claim to have the source code for Shutterfly’s store. However, they did not specify which store was it, be it Shutterfly.com itself or any other.
Shuttefly Addresses!
Bleeping Computer contacted the giant company a few days ago. Shutterfly clearly stated that the attack does not include its Shutterfly.com, Snapfish, TinyPrints, or Spoonflower sites.
Also, Shutterfly did claim that the attack did not disclose any financial information. However, the screenshots do include the last 4 digits of credit cards. You can find the full statement below:
“Shutterfly, LLC recently experienced a ransomware attack on parts of our network. This incident has not impacted our Shutterfly.com, Snapfish, TinyPrints or Spoonflower sites.
However, portions of our Lifetouch and BorrowLenses business, Groovebook, manufacturing and some corporate systems have been experiencing interruptions.
We engaged third-party cybersecurity experts, informed law enforcement, and have been working around the clock to address the incident.”
“As part of our ongoing investigation, we are also assessing the full scope of any data that may have been affected. We do not store credit card, financial account information or the Social Security numbers of our Shutterfly.com, Snapfish, Lifetouch, TinyPrints, BorrowLenses, or Spoonflower customers, and so none of that information was impacted in this incident.
However, understanding the nature of the data that may have been affected is a key priority and that investigation is ongoing. We will continue to provide updates as appropriate.”
Bleeping Computer did reach out again considering the screenshots. Sadly, Shutterfly only responded by reverting them back to the original statement.
The Ransomware Conti-nues to Terrorize Big Names
Conti has hit big companies in the past, and it doesn’t to be stopping any time soon. The attackers can easily gain access to an internal system, harvest data, and deploy ransomware.
With Conti attacks rising, even the FBI, CISA, and NSA are worried. All you need to do is be careful. The attackers can hack into big companies. In other words, they can easily get to you.