How to Secure Vulnerable Ports on Your PC or Mac
Computers use ports to access the Internet and communicate with several websites and apps online. Despite being a crucial factor, these ports don’t come without their drawbacks. The point here is that there is a large number of ports your devices are using to communicate with the outside world, and in turn, any malicious party that wants to snoop on your data or penetrate your systems targets them. What should you know to secure vulnerable ports on your PC? Find out in this comprehensive guide.

Computer Ports 101 – What You need to Know
Your computer can use up to 65,535 ports to connect to the Internet and communicate with websites and applications online.
Yes, the number is true, and you should be thankful that only the first 1023 ports are actually in use. They’re being reserved for incoming connections by the services you are running on your machine.
You access websites through port 80 as web servers traditionally communicate over Hypertext Transfer Protocol (HTTP) used in the World Wide Web on this port.
More recently, secure sites use port 443 for HTTP Secure (HTTPS) HTTP over TLS/SSL protocol. Your e-mail client listens on ports 25 and 110 while DNS services use port 53.
The Targeted Ports
The list is quite long, and you can find the complete listing of the officially assigned ports on the site of the Internet Assigned Numbers Authority (IANA).
A hacker can attack any of your networking ports, but in fact, there are a dozen ports that are being tested most often by malicious actors. Those are:
| Port Number | Port Usage |
| 20 | File Transfer Protocol (FTP) data transfer |
| 21 | File Transfer Protocol (FTP) command control |
| 22 | Secure Shell (SSH) |
| 23 | Telnet – Remote login service, unencrypted text messages |
| 25 | Simple Mail Transfer Protocol (SMTP) e-mail routing |
| 53 | Domain Name System (DNS) service |
| 80 | Hypertext Transfer Protocol (HTTP) used in the World Wide Web |
| 110 | Post Office Protocol (POP3) used by e-mail clients to retrieve e-mail from a server |
| 119 | Network News Transfer Protocol (NNTP) |
| 123 | Network Time Protocol (NTP) |
| 143 | Internet Message Access Protocol (IMAP) management of digital mail |
| 161 | Simple Network Management Protocol (SNMP) |
| 194 | Internet Relay Chat (IRC) |
| 443 | HTTP Secure (HTTPS) HTTP over TLS/SSL |
The average user rarely uses some of these ports despite them being considered the most common ports used to communicate and share data online.
For example, FTP services on port 21 were popular in the past. But now, large IT companies are seriously considering ceasing support for FTP at all.
The average computer user will also rarely use Secure Shell (SSH) on port 22 or other services that run on ports with higher numbers.
Secure Vulnerable Ports on Your PC
In any case, you need to secure your devices. How? You should close the outbound connections on certain ports and some ports altogether.
For instance, many Trojan viruses and worms use port 1080, and there should be no connections on this port unless you have specifically set it up for a socket secure proxy.
After you are aware of which ports to close and what inbound and outbound connections are legitimate, you need a firewall to define rules for incoming and outgoing traffic.
All major operating systems come with a built-in firewall. Below, we’re going to show you how to check for vulnerabilities and allow/restrict traffic on your computer by reading through the below paragraphs.
Scan Your Windows PC
The scanning technique is used to identify open ports and services available on a network host. It’ll help you audit your device for vulnerabilities.
First, let’s kick it off by how to portscan your Windows PC. To do so, you should download an application called SoftPerfect Network Scanner and follow these steps:
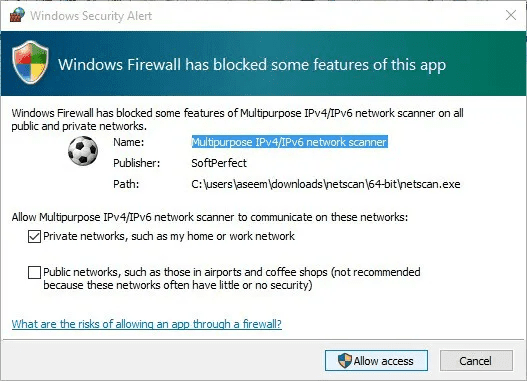
- When you download the app and run it, you might witness a message stating that Windows Firewall has blocked the program. Click on Allow Access.
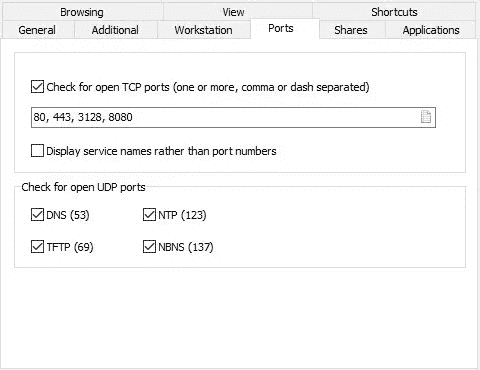
- Now, run the app and click on Ports.
- Type in the ports you want to check.
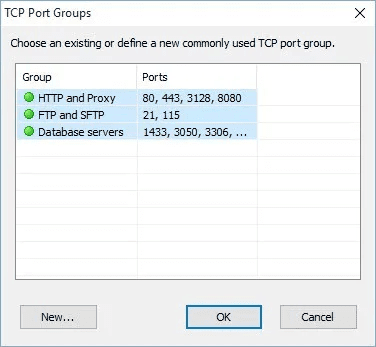
- This will open another window highlighting some TCP port groups. Click on HTTP and Proxy and then hit the SHIFT key and select Database servers to choose all three items.
- On the main screen, you’ll find a list of port numbers in a text box. There, you can check for open UDP ports.
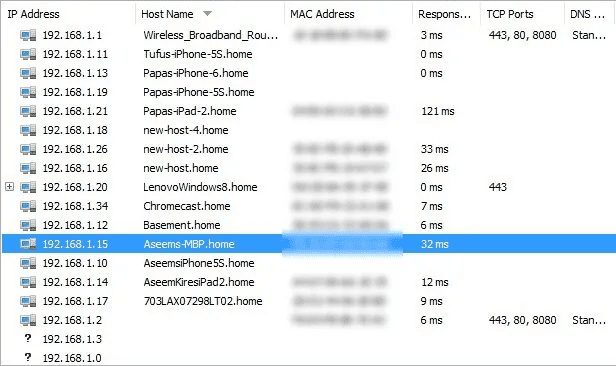
- Now, select Start Scanning and you should see results slowly added to the list. On the right of the next page, a list of open ports will be shown for the device.
Blocking Ports and Applications in Windows
All versions of the Windows operating system, starting from Windows XP through Windows 10, come with a built-in firewall.
You can change the Windows Firewall settings by opening:
- Windows Start Menu
- Control Panel
- Windows Firewall
Then, you can allow or deny a program or feature, or use the advanced settings (shown below) to configure specific ports/applications and create rules for inbound and outbound traffic.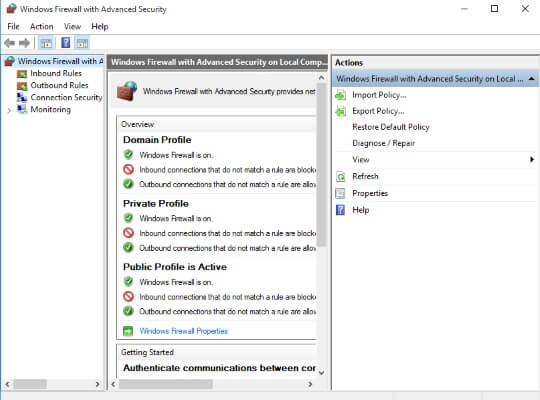
Actually, your Windows Firewall comes with pre-defined settings for home and public networks, which will work well for most users.
For instance, if you choose a network as a home network, it will grant more permissions to devices within the network and will open some ports for communication.
In contrast, if you specify a network as a public network e.g., your Wi-Fi network, the firewall will block all connections to any program that is not on your list of allowed programs.
Needless to say, but if you are working with sensitive data within a specific application, you may decide to use the advanced firewall settings and create a rule that prevents the app from connecting to other services.
You can also completely close the port this program is using to communicate if you know the port number.
Check Open Ports on Mac
Portscanning on Mac requires a different application, LanScan. It’s free and you can find it in the Mac store. It does a simple, yet fast scan and displays everything about your device.
We’re talking about MAC Adress, IP Address, Hostname, and Vendor. Now, to check for open ports, do the following:
- Download and install the application on your Mac.
- Launch it and this page will appear.
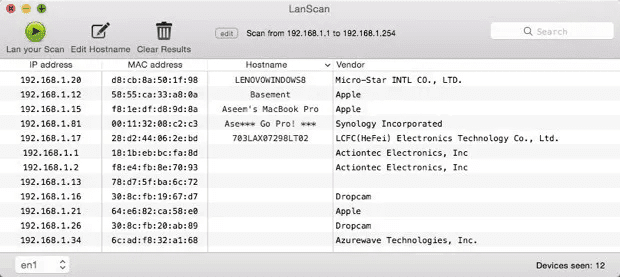
This application does not show much, but it’s one of the few options Mac users have. If you want a deeper, more comprehensive look, there’s another app that goes by the name of Angry IP Scanner. It looks like this: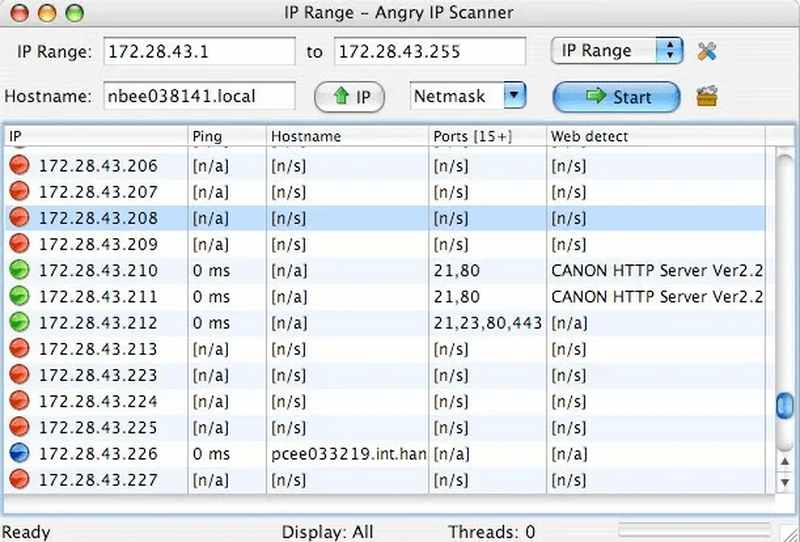
The software scans open ports by default, which is a feature that LanScan lacks. One thing to note: If you want to use Angry IP Scanner, you should have Java already installed on your device.
You might not know this, but Java is a big security risk. There’s a reason why Macs disable it by default.
Blocking Ports and Applications in macOS
Mac computer users can block incoming and outgoing data traffic in the very same way a Windows user is utilizing his firewall, with all Apple computers offering a built-in firewall as well.
You can access the macOS firewall by opening:
- Apple Start Menu
- System Preferences
- Security & Privacy
- Firewall
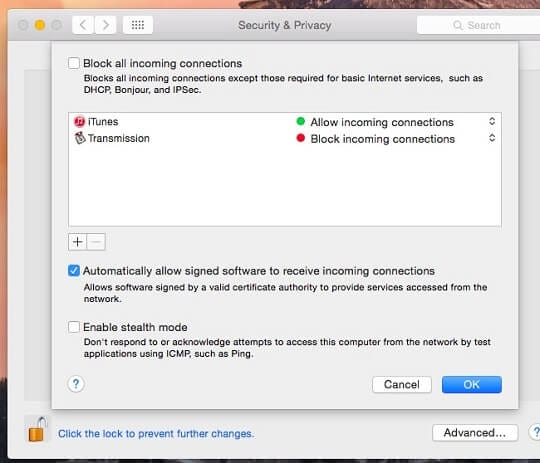
From this control panel, you can take advantage of pre-set firewall rules, add apps and services to the list of executables managed by the firewall or go to the advanced settings if you want to create your own rules for inbound and outbound connections.
You should be aware that despite Apple’s iOS operating system for iPhone and iPad is built on macOS; your iOS-powered device does not come with a built-in firewall.
Blocking Ports and Applications in Linux
A popular delusion is that only a bachelor in computer sciences can start and configure a Linux firewall. It is not true for at least a decade as user-friendly distributions, or releases, of the Linux operating system, are growing in popularity.
Linux distributions such as Linux Mint, Ubuntu, Zorin OS, or Manjaro Linux all come with a built-in firewall that users with basic tech skills can start and operate.
The problem with Linux firewalls is if you want to configure and operate them using the terminal console of the operating system where no graphic interface is available, and you should use commands instead of your mouse.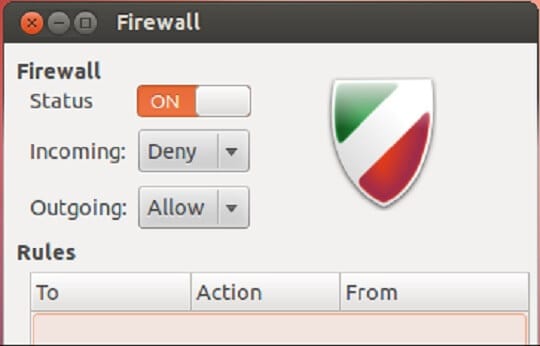
As you can see, the graphical user interface of an Ubuntu firewall is quite similar to the interface of Windows and Mac firewalls. It allows users to switch the built-in firewall on and off as well as to create their own rules what inbound or outbound traffic to block or allow.
In contrast, if you want to allow your website running on a Linux webserver to accept connections on ports 80 and 443, which are transporting HTTP and HTTPS traffic respectively, and you are doing this through the Linux terminal, the terminal command window will look like: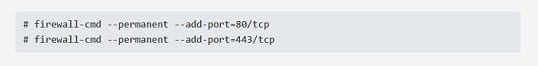
In fact, you should tell your Linux-based website server to specifically open these ports, as the firewall will block all incoming traffic by default, with some exceptions that allow system administrators to connect to the Linux command center.
Extra Security Tips
The tips we gave above are essential if you want to secure your PC ports. However, there’s not enough. There are a couple of things you can do to enhance that security – check them out below:
- Install Antivirus Software: A credible anti-virus software present on your computer. There are many of those that’ll help your device combat the likes malware, spyware, and Trojans.
- Update your OS: Keep your computer up-to-date. Always check if there are updates so that your device can fix certain irregularities in your system. If you forget to do so, set the updates on Automatic, it’ll do the job for you.
- Use Trusted Browsers: Alway operate on browsers that are common and known to be safe and trusted. These browsers have built-in security features that minimize the risk of your computer being infected with malware.
- Skeptic Downloading: A lot of browsers nowadays warn you when you’re downloading a certain file. They will inform you that your download contains materials that may harm your computer. Try to avoid that.
- Avoid Public Networks: If you’re using Wi-FI in cafes, restaurants, or a hotel, any hacker can secretly access your accounts or steal your passwords through the Wi-Fi. Avoid them at all costs, and if necessary, use a VPN to encrypt your data.
- Don’t use Public Computers: In an internet cafe or library, hackers might install malware to harvest data from whoever uses the same device. Do your research or get your work done on your own device.
The above tips are very important, yet easy to do. So do not take them lightly, your personal information is at risk here.
Concluding Words
The chance is good that you do not have permission to change the firewall settings on your office PC. However, do not experiment too much with your home firewall.
As we said, built-in Windows and macOS firewalls, as well as Linux firewalls on distributions designed for the average user, are providing sufficient protection by default.
Tweaking your firewall rules may result in preventing some legitimate apps or services from working properly without improving your security.
Finally, it is all about your browsing habits, after all. For example, a firewall cannot prevent you from downloading a file infected with a virus. Read the article well. If you have any more questions, please drop them in the comments below.





