Enter Nexus: The New Banking Trojan Targeting Financial Android Apps
Android users have had a rough 2022 thanks to the constant malicious practices on the OS itself. However, 2023 doesn’t look so good, as the first couple of months introduced various new malware families, big malicious campaigns, and data breaches. Speaking of malware families, the new banking trojan, Nexus, is targeting Android financial applications.

The malware is relatively new, but it’s definitely capable. Available on hacking forums, anyone can get their hands on it for a specific fee. Can you imagine the damage?
Well, in this particular campaign, Nexus targets more than 450 financial applications for various intents, including fraud. But how does it infiltrate the device? Can it harvest information? How much is it? Find out in the following article.
Nexus Trojan – The Account Takeover Specialist
When it comes to AndroidOS, a lot of risks might emerge out of nowhere. The problem here is that no source can be fully trusted, even Google Play Store.
In the past, Android users suffered multiple campaigns, be it from third-party sources or through applications within the Store’s library.
A while ago, malicious applications carrying the Xenomorph malware spread all over the Play Store. Not to mention that one incident where Sharkbot took over as well.
Now, the Nexus Trojan is making its debut by targeting over 450 banking applications with one goal in mind – ATO attacks (Account Takeover).
According to the Italian cybersecurity firm Cleafy:
Nexus provides all the main features to perform ATO attacks (Account Takeover) against banking portals and cryptocurrency services, such as credentials stealing and SMS interception.”
As we mentioned, the trojan is available on hacking forums in exchange for a monthly subscription. In other words, if anyone can shell out $3000 a month, they can utilize Nexus for their own malicious practices.
The trojan is still in its early stages and is just being utilized recently by cyber criminals. Nexus appeared on various hacking forums at the start of 2023.
However, according to a study by Cyble, the malware isn’t actually new. In fact, it’s been around since June 2022, as it’s been used in real-world attacks six months before its official announcement on darknet portals.
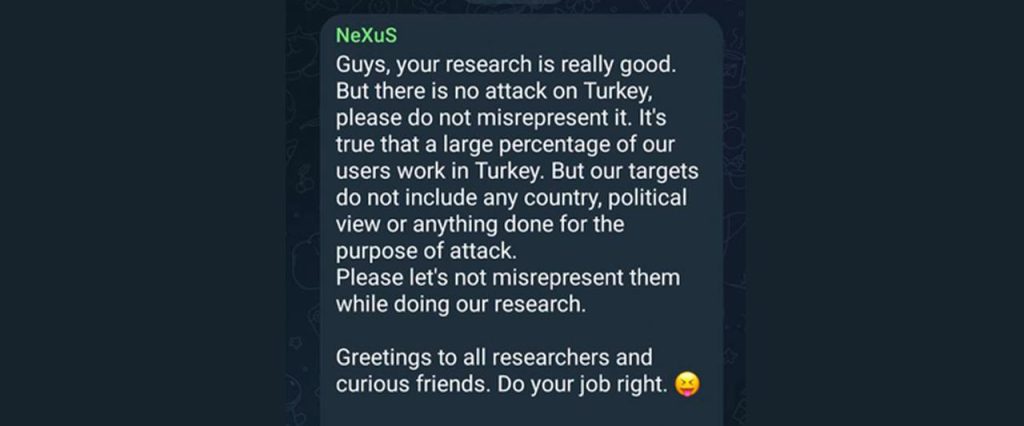
The authors behind Nexus confirmed on their Telegram channel that the majority of the Nexus infections had been reported in Turkey. Are they, though?
The report also states that Nexus uses parts of a banking trojan dubbed SOVA. In the future, Nexus might develop its capabilities to incorporate a ransomware module.
A New Day, A New Trojan – Enter Nexus
Malware families and banking trojans are being created every day. It’s very rare for threat actors to limit the use of their malware, especially when it’s sold publically on hacking forums.
However, the individuals behind Nexus did. Apparently, the group doesn’t allow the use of their trojan in certain countries such as Russia, Tajikistan, Azerbaijan, Armenia, Belarus, Kazakhstan, Kyrgyzstan, Moldova, Uzbekistan, Ukraine, and Indonesia.
This malware-as-a-service is dangerous, and it comes with various capabilities, such as performing overlay attacks and keylogging to steal users’ credentials. Be careful and stay safe.





