Amadey Info-Stealing Malware: A Backdoor-Backdoor Infection Process
Cybercriminals are elevating their techniques to infect as many victims as they can. One way to do so is to masquerade as some sort of software to inject backdoors into the device – this is the perfect method for info-stealing malware. A couple of months ago, the RedLine malware targeted Windows devices. Now, a new malware – Amadey – is being distributed by means of another backdoor called SmokeLoader.

The attackers trick the users into downloading some sort of software cracks, which later installs the backdoor Smokeloader. And then, Smokeloader continues the job by injecting Amadey.
The info-stealing malware has been around for a couple of years now, and unfortunately, threat actors have been updating it since. What information is at risk? What are the attackers after? We discussed everything below.
Amadey Malware – You Install, They harvest
Info-stealing malware attacks are on the rise, and we’ve encountered several of them in the past few months. A while ago, phishing emails were sent to 27,655 addresses in hopes of stealing information. The campaign saw the attackers disguise themselves as WhatsApp agents.
Now, the threat actors masquerade as software cracks that install Smokeloader, which further deploys the Amadey info-stealing malware.
As we mentioned, cybercriminals have been updating Amadey for around 4 years. It first appeared on Russian underground forums where it was sold for around $600 and used by various attackers.
According to a study by the AhnLab Security Emergency Response Center (ASEC):
“SmokeLoader provides various additional features related to info-stealing as plug-ins. It is normally used to install additional malware strains as a downloader.
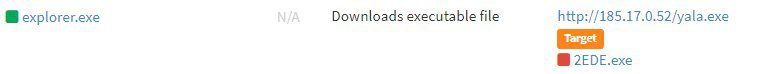
When SmokeLoader is run, it injects Main Bot into the currently running explorer process (explorer.exe). This means Bot that performs actual malicious behaviors operates inside the explorer process.
The figure below shows AhnLab’s ASD log of SmokeLoader, which has been injected into explorer, downloading Amadey.”
Once Amadey sets root in the device, it can siphon credentials, capture screenshots, system metadata, information about antivirus engines, and additional malware that might be on the machine.
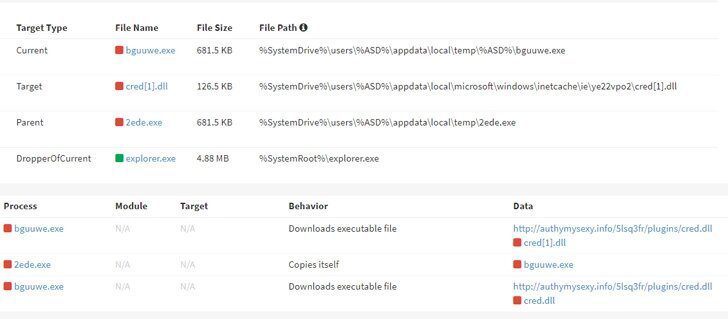
The malware collects the device’s information and sends it to the C&C server in an appropriate format. Next, the server sends the URL of additional malware strains that Amadey will download to make it operate as a downloader.
Aside from stealing the information, Amadey’s main goal is to install additional plugins and remote access trojans such as Remcos RAT and RedLine Stealer. As a result, it’ll allow the attacker to commit all sorts of malicious practices whenever he/she wants.
The Amadey Info-Stealer – Cracking Down Your Defenses
As usual, to avoid such attacks, we highly recommend users update their devices to the latest versions of the operating system. This might fix any security flaw present at the moment.
Moreover, antivirus software should always be present regardless of the device you’re using. At the very least, these two steps will minimize potential infections and detect any malicious software.