You’ve Got a Voice Message: A WhatsApp Malware Campaign
Phishing campaigns are probably a trend now among cybercriminals, especially when they impersonate big social media platforms to get to their victims. In the past, threat actors sent fake emails in the name of Instagram and Twitter for their ransomware campaigns. Now, we can add WhatsApp to the mix, as threat actors are using its Voice Message feature to spread information-stealing malware.
Emails can travel so fast to reach hundreds of thousands of victims. And when the email comes from WhatsApp, we definitely assure you that a lot will fall victim. To be exact, emails were sent to at least 27,655 email addresses.
The aim of this is quite clear – Info-stealing. In other words, the threat actors prompt users to go through several steps, leading to the installation of the malware, and finally, credential theft. How are they pulling this off? Find out below.
A Fake Voice Message – Press Play, Fall Prey
Cybercriminals usually use emails to lure victims into their traps. In some cases, they prey on the users’ feat factor, informing them about a data breach or any type of incident that needs immediate action.
Now, they’re targeting their curiosity by sending emails that include a fake WhatsApp Voice Message. The email does show received a new private message with an embedded “Play” button and an audio clip.
To make this even more convincing, the criminals added the duration and creation time details of the audio clip.
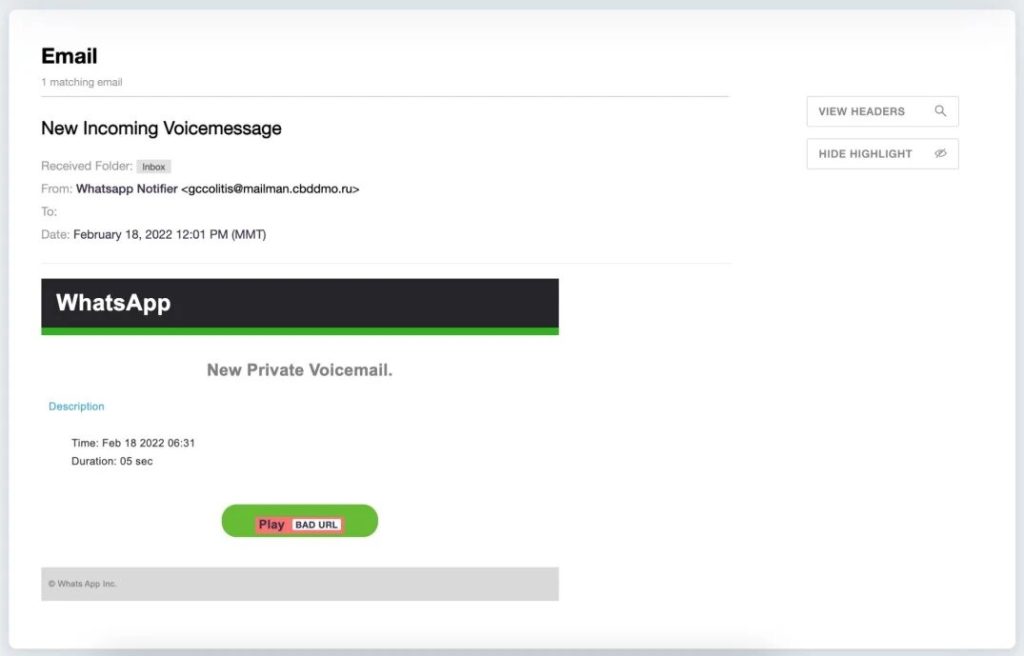
The problem here is that the threat actors are using a genuine and legitimate entity. That’s why the email security solutions did not flag the emails as fake or block them, to begin with.
According to Armorblox, the hackers somehow exploited the domain to reach these end results, and apparently, they succeeded.
Just like most similar phishing emails, the users have to click on the button to activate the process. Once done, they’ll be redirected to a website where the JS/Kryptic trojan is present.
The installation process does not commence immediately as the page includes an allow/block prompt first. To guarantee an “allow” click, the threat actors had to make this more legitimate.
That’s when a web page stating that the user needs to tap on ‘Allow’ to confirm he/she is not a robot appears.
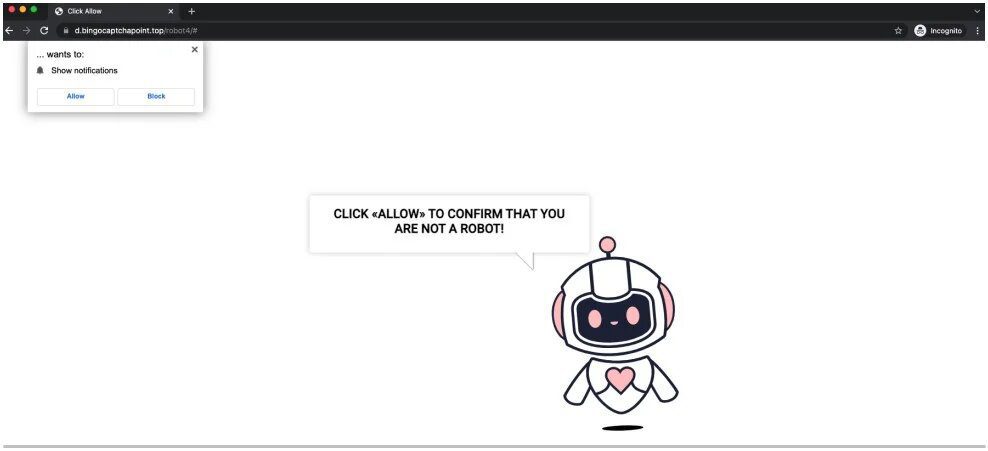
When it’s clicked, it will trigger unwanted subscriptions to web notifications that send in-browser advertisements for malware, adult webpages, as well as scams.
Not only that, but the page will also prompt users to install the payload. As a result, the victims will have new information-stealing malware on their devices.
WhatsApp Malware Campaign – A Voice Best Left Unheard
Emails containing phishing links are pretty common nowadays. With hackers impersonating big companies, anyone could become a victim at the end of the line.
To protect yourself, make sure you stay vigilant when it comes to handling your emails. Never trust a source no matter how trustworthy it is.
Always turn to the official source itself – that way, you’ll at least know that whatever is going on is legitimate and not a scam. Stay Safe.






