Parental Control – Kids Place: Five Million Downloads, Five Vulnerabilities
Downloading applications is a handful. You never know what to expect, even if the software you’re downloading is from a trusted source such as Google Play Store. While the Android store has had its fair share of infiltrations, some innocent apps may cause damage as well. We’re talking about Parental Control – Kids Place – the widely popular kids app that is hosting 5 major vulnerabilities.

The app has more than five million downloads on Google Play. It’s widely popular among parents who want to keep tags over what their children are accessing on their devices.
In general, the app does exactly what it’s supposed to. However, with five vulnerabilities, cybercriminals can easily take advantage of it. What can they do with these flaws? What are the vulnerabilities? We’ve explained everything below.
Parental Control – Kids Place: An Innocent App Turned Malicious
Vulnerabilities are everywhere. Even the highly-secure Apple devices have had a lot of them in the past year or so.
Now, we will cover what’s going on with the Android app Kiddowares’ Parental Control – Kids Place.
This particular tool allows parents to track what their kids are doing on their phones. This includes:
- Geo-location monitoring
- Internet access and purchasing habits
- Screen time management
- Harmful content blocking
- Remote device access
As good as this app is, security researchers have found out that it hosts five vulnerabilities that can have devastating consequences, including allowing cross-site scripting or cross-site request forgery. Here’s what can happen if any malicious actor decides to utilize these flaws:
- Upload arbitrary files on protected devices
- Steal user credentials
- Allow children to bypass restrictions without the parents’ consent.
Now, newer versions are out (3.8.50+). It’s highly recommended to update the app to cover these vulnerabilities and avoid any future predicaments.
The Flaws
To have a better idea of the flaws in question, we’ve listed them below based on the research done by one of the leading consultancies in the area of cyber and application security – SEC Consult:
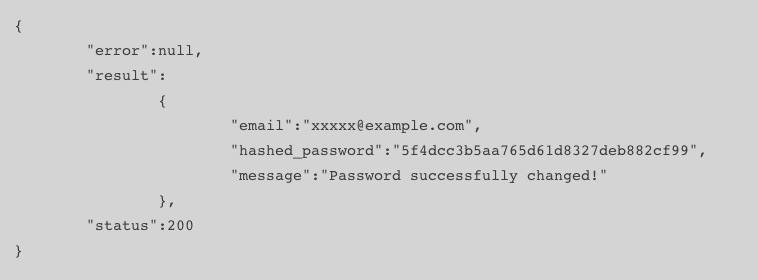
- Login/Registration returns password as MD5 hash:
Login and registration requests return the unsalted MD5 hash of the password. In other words, the app stores passwords on a server that’s deemed insecure. Please note that MD5 hashing is outdated, and more secure options are available for modern apps.
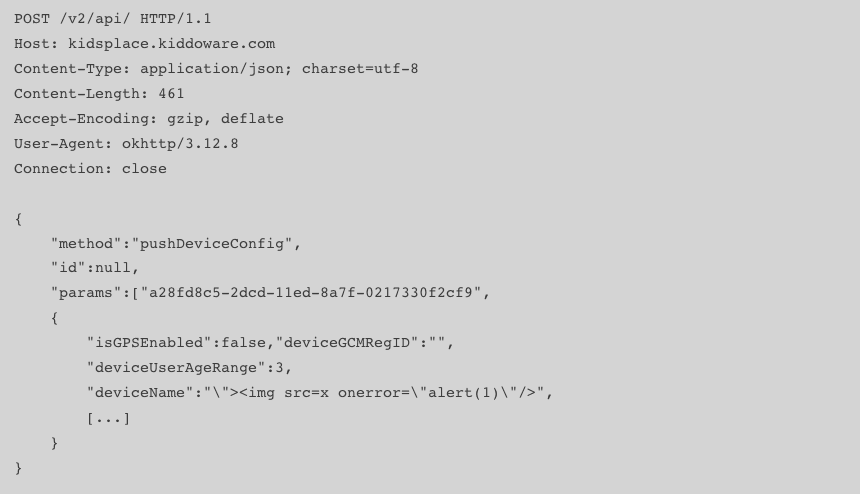
- Stored XSS via device name in parent Dashboard (CVE-2023-29079)
The name that parents can customize for the child’s device can be utilized to initiate the XSS payload hosted on the parent web dashboard. The child could have the ability to attack the parents’ account.
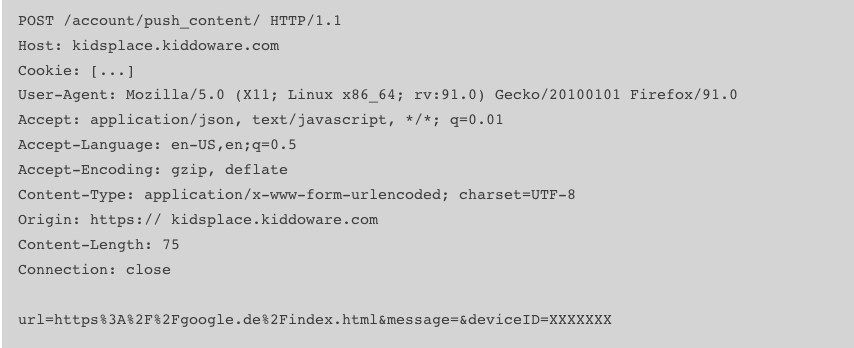
- Possible CSRF attacks in parent Dashboard (CVE-2023-29078)
The requests on the web dashboard are entirely susceptible to CSRF (Cross-site request forgery) attacks. Since any request made through the app contains the device’s ID, attackers can exfiltrate that through the browser history and successfully attack the device.
- Arbitrary File Upload to AWS S3 bucket
When the parent-child devices are connected, the app allows the parents to send files to the child’s devices. Since the file is uploaded to an AWS S3 bucket, the returned link would be publicly available, allowing threat actors to spread malware.
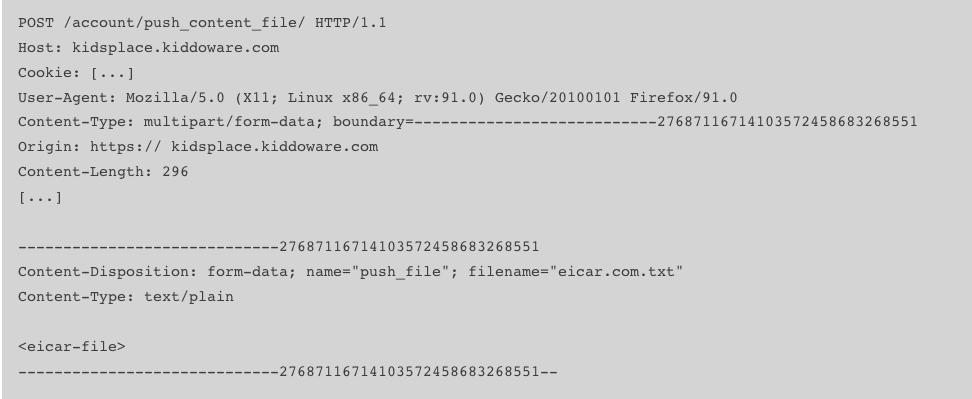
- Disable Child App Restriction without Parent’s notice (CVE-2023-28153)
This flaw allows the children to disable the restrictions applied by the parents without their knowledge or consent.
These vulnerabilities’ impact is high. While most of them don’t seem like a real threat, others are, especially those that allow malicious activities.
Update the Application Now
Parents should be concerned about what their children are accessing on the internet. However, they should also look out for such vulnerabilities as they can have drastic consequences.
We highly recommend updating the app to a version where the vulnerabilities are resolved. If you haven’t done that yet, do it now.
The vulnerabilities can cause a real threat to you and your children. You don’t want an outside entity to take over your devices. Stay safe.





