.ZIP Domains Weaponized – A New Clever Phishing Lure
You browse a lot, you see a lot, and we’ve been seeing more than our fair share of innovative techniques used by threat actors. From malvertising campaigns to phishing ones, cybercriminals have always come up with new ways to target their victims. Speaking of new ways, Google’s new Top Level ZIP Domains (TLD) are not even a month old, and malicious actors are already utilizing them.

Google stated that 8 new Top Level Domains (TLD) are now available. However, there were many concerns among security researchers that the new TLDs could be mistaken for file extensions.
That’s due to the fact that two of them come in the form of .ZIP and .mov. Now, you might ask yourself: Are their concerns in place? How can cybercriminals implement their phishing tactics? We’ve discussed everything below.
Google’s TLD – New ZIP Domains, New Threat
The letters at the end of a website’s address reflect what we call top-level domain (TLD). They always vary as each one gives a certain idea about the website.
We’re referring to, for example, its purpose, the organization that owns it, or the geographical area it was created in.
We all know (.com) – it’s the most popular TLD out there. However, there are several others, including .info, .org, .dev, and more. Each of these has its purpose, as seen in the table below:
| TLD | Purpose/Entity |
|---|---|
| .com | Shows that the entity that owns domain this domain is a commercial organization. |
| .org | This proves that this domain name is registered to nonprofit organizations. |
| .edu | Short for education, this TLD shows that the domain is registered with educational and academic institutions such as universities and colleges. |
| .gov | An abbreviation of the word “Government.” This TLD shows that an internet address belongs to a government organization. |
There are more examples to show, but we’re here to talk about what’s recently been going on. Google introduced the new TLD domains to provide better representation for certain areas. The new TLDs are the following:
- .dad
- .phd
- .prof
- .esq
- .foo
- .zip
- .mov
- .nexus
The announcement of 8 new TLDs is quite beneficial for a lot of departments, especially law firms that will be using the .esq domain.
The word esquire (commonly abbreviated as Esq.) is a title lawyers use in the United States. However, these domains don’t come without a price.
Apparently, these domains are available at early access prices. They cost $11,500 to register and then $30/year thereafter.
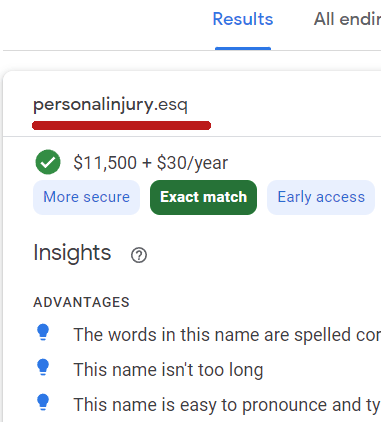
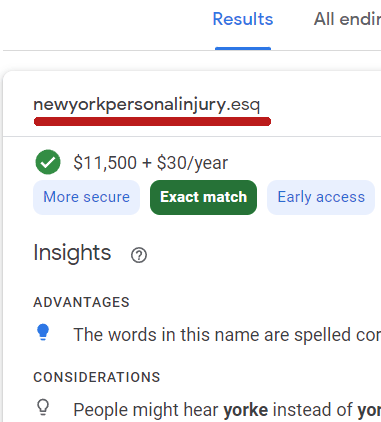
Unfortunately, not only do these domains come with a price, but they also come with security risks.
These TLDs caused controversy among security professionals since many have considered them too dangerous. And they were right!
The New Phishing Campaign
While providing new TLDs gives more opportunities and recognition, cybersecurity experts have been worried that they also pose a huge security threat.
If you haven’t noticed, two of these TLDs stand out. We’re referring to the .zip and .mov. These domains are well-known to be file extensions. But where’s the risk?
Well, various messaging platforms and social networks will automatically convert file names with .zip and .mov extensions to URLs. An example of these platforms would be none other than Twitter.
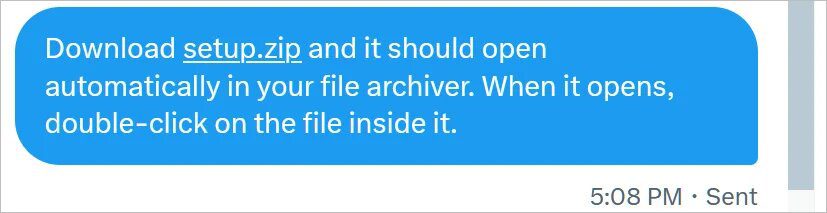
When the users click on the link, the browser will attempt to open the https://setup.zip site, leading to another website that could be created by a threat actor.
In this particular campaign, cybercriminals are presenting fake WinRAR or Windows File Explorer windows in the browser to trick their victims into downloading infected files.
Cybersecurity researcher mr.d0x created a clever phishing toolkit to explain further how the campaign is carried through.
“With this phishing attack, you simulate a file archiver software (e.g., WinRAR) in the browser and use a .zip domain to make it appear more legitimate.”
The toolkit allows anyone to create fake in-browser WinRar instances as well as File Explorer Windows displayed on ZIP domains, tricking users into thinking they have opened .zip file.
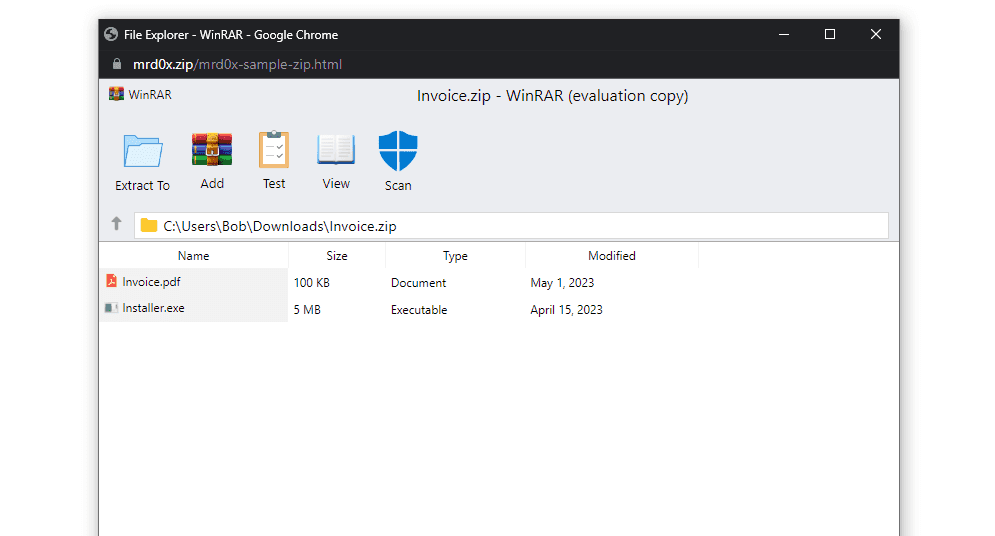
With WinRAR, the threat actors can benefit from features that definitely increase the legitimacy of the phishing page. For example, the ‘Scan’ icon generates a message box that states that the files are safe.
When the users click the file, they might end up on pages with all sorts of capabilities. That includes credential harvesting ones.
Yes, the page might have a section where the victims are asked for their login credentials to view the file. It doesn’t end here.
There are more possible outcomes to this, and mr.d0x has explained every single one of them in his report.
From Clever to Malicious – Let the Phishing Begin
mr.d0x creates clever ways to show that certain stuff online can instantly become phishing attacks. Unfortunately, what he presents, cybercriminals utilize.
With the new TLDs, cybercriminals can also come up with clever phishing attacks, which easily lead to malware delivery and credential theft.
So, what can a user do in this situation? All you need to do is remain vigilant when handling such file extensions. If you end up on a random page, close it immediately. Don’t submit any information.
As for PDF files, we highly recommend not clicking them. They might end up injecting malware into your device. Stay safe.





