KamiKakaBot Malware – South Asian Government and Military Entities Under Cyber
Cyberattacks have taken a habit of targeting all sorts of institutions around the world. That also includes government and military entities. Recently, a cybercriminal group known as Dark Pink has been issuing multiple malicious campaigns in the South Asian region.
The group’s fresh set of attacks includes none other than the KamiKakaBot malware, which can easily run arbitrary commands and exfiltrate sensitive information from government and military institutions.
As reported, Dark Pink has been suspected to be active since at least mid-2021, and it seems that it’s not stopping anytime soon. So, what is this campaign all about? Find out in the following article.
Dark Pink Strikes – KamiKaka Everywhere
Wherever there’s sensitive information they can benefit from, cybercriminals will always be there. No matter what department the company specializes in, if there’s data, there’s cybercrime.
Threat actors will always look for the perfect opportunity to strike. Whether it’s utilizing vulnerabilities or targeting specific users with phishing campaigns, it’s inevitable.
In Dark Pink’s case, the intentions are pretty clear – harvest all the information the group can get from government and military entities in the South Asian sector.
According to Dutch cybersecurity company EclecticIQ,
“The latest attacks, which took place in February 2023, were almost identical to previous attacks. The main difference in the February campaign is that the malware’s obfuscation routine has improved to better evade anti-malware measures.”
Basically, the campaign kicks off with a phishing email that contains an ISO image file, which delivers the malware once downloaded and executed.
Within the ISO image, there’s an executable (Winword.exe), a decoy Microsoft Word Document, and a loader (MSVCR100.dll), which contains the KamiKakaBot payload.
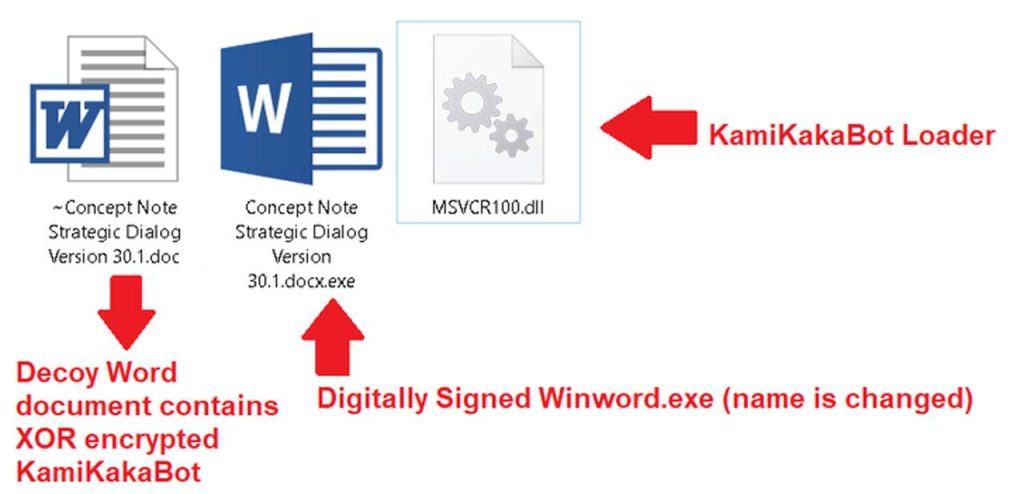
The malware is well-designed to bypass any installed security measurements and load itself into the memory of the Winword.exe binary.
Once KamiKaka takes root, it can harvest the data in web browsers and execute remote code using Command Prompt (cmd.exe).
Not only that, but it can also blend in within the victims’ system environments and avoid several detection methods. As reported, the harvested information is subsequently exfiltrated to a Telegram bot as a ZIP archive.
“The use of legitimate web services as a command-and-control (C2) server, such as Telegram, remains the number one choice for different threat actors, ranging from regular cyber criminals to advanced persistent threat actors.”
The malware is dangerous, and the threat actors behind it seem to be very determined to gather information from South Asian government facilities.
A New Attack – KamiKaKa Lurks Stealthly
The cybersecurity firm states that Dark Pink exploits relations between ASEAN and European nations. Why? Well, according to the report, the group takes advantage of the information it steals to create phishing lures.
So far, we don’t know what data the group has gathered. Anyone is susceptible to such attacks. Whether it’s a company or an individual, internet users should always take proper precautions, especially when downloading content via a received email.





