DotRunpeX Malware Emerges – One Malvertisement, Multiple Malware Families
Cybercrime has evolved over time as cybercriminals come up with various methods to target their victims. However, using none other than Google to spread campaigns must be one of the most common ways to do so. Yes, another campaign is here, but this time, multiple malware families are included – Enter DotRunpeX.
To appear at the top of a Google search is a hard task, and the individuals behind DotRunpeX managed to do exactly that. In other words, this particular group is capable.
This malware, once in, can inject numerous known malware families, including none other than RedLine and Vidar. So, what’s up with this new campaign, and how is it implemented? Here’s what we know.
DotRunpeX Malvertising: An All-Star Malware Campaign
Online advertising is a source of revenue for many companies. And sometimes, it can be so as well for cybercriminals. If they have the right tools, they can end up at the top of the search results within whatever engine a user’s operating.
With the use of various advertising strategies, these threat actors can lure anyone to a fake page where the malware is present. Yes, anything is possible.
A while ago, a malicious group started spreading Youtube campaigns. Can you imagine? The legit streaming platform, Youtube, was impersonated.
After that, the threat actors disguise as “security alerts” from Windows Defender. And we know what happens next.
This time around, the cybercriminals are deploying DotRunpeX through the use of a downloader (aka loader) found in fake websites through Google Ads. (It’s also spread through phishing emails).
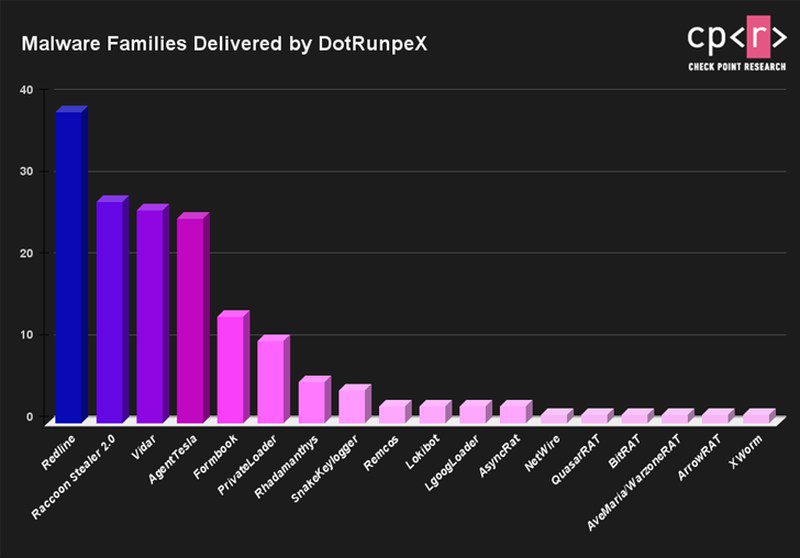
According to a report by Check Point, the DotRunpeX will take root inside a device and deliver multiple malware families as a next step. These are the families included in this malicious campaign:
- Agent Tesla
- Ave Maria
- BitRAT
- FormBook
- LokiBot
- NetWire
- Raccoon Stealer
- RedLine Stealer
- Remcos
- Rhadamanthys
- Vidar
We’re well aware of all the families in the list above. However, DotRunpeX seems to be very fond of the RedLine Info-Stealer, as it’s the most used in this attack.
The report also added that “each dotRunpeX sample has an embedded payload of a certain malware family to be injected,” so be careful what you’re downloading on your device. You don’t know what you’ll be getting if you’ve ended up on one of the fake websites.
Malvertising Got Bigger – Malware Families by the Dozen
According to the firm’s report, the individuals behind this campaign might be Russian-speaking actors based on the language references in the code.
With RedLine, Raccoon, Vidar, Agent Tesla, and FormBook being the most frequent families to be distributed through this campaign, it’s pretty obvious how big and dangerous it is.
Don’t click on ads. If you want to visit a certain website, make sure to go there manually. Not all of them are malicious, but that’s the only way to stay on the safe side.






