GoodWill Ransomware – A Rising Cyber Robinhood?
When it comes to ransomware in general, there’s technically nothing new to talk about. The threat actors encrypt their victims’ data and ask for a certain ransom in exchange for decryption. However, when a ransomware gang’s main cause is to force victims into providing financial assistance to people in need, that’s when things fall out of the ordinary – enter GoodWill Ransomware.

The individuals behind this ransomware aren’t targeting anyone for self-beneficial reasons. Instead, they pick their victims, encrypt their files, and then ask them to do unusual things that help those who are financially in need.
This Robin Hood-like group is stealing from the rich and giving to the poor, but it’s still cybercrime. What is GoodWill ransomware? How do the gang’s victims pay their ransom? Find out below.
Where There’s GoodWill, There’s Ransomware
Ransomware attacks have become a very common practice lately, targeting big companies and random targets all over the world.
A few days ago, an old inactive group resurfaced with over 21 victims within a month. Talk about a shocking return. Speaking of shocking, GoodWill – a new ransomware strain piqued our interest due to its unusual ransomware activity.
The group does whatever ransomware users do – lock a target’s file and ask for a ransom. But surprisingly, the ransom isn’t what we’d expect in terms of payment and the receiving entity.
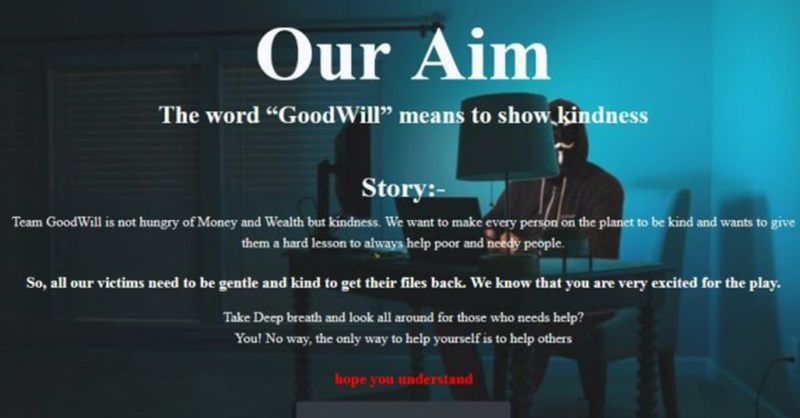
Apparently, the individuals behind GoodWill are not looking to harness the money for themselves. Instead, they want to give it to the poor. Well, force the victims to pay those with financial needs.
According to CloudSEK researchers:
“The ransomware group propagates very unusual demands in exchange for the decryption key. The Robin Hood-like group claims to be interested in helping the less fortunate, rather than extorting victims for financial motivations.”
The research states GoodWill is India-based and the people behind it speak Hindu. CloudSEK identified this threat back in March 2022. These are the ransomware’s features as per CloudSEK’s research:
- The ransomware is written in .NET and packed with UPX packers.
- It sleeps for 722.45 seconds to interfere with dynamic analysis.
- It leverages the AES_Encrypt function to encrypt, using the AES algorithm.
- One of the strings is “GetCurrentCityAsync,” which tries to detect the geolocation of the infected device.
The attack renders sensitive files inaccessible without decrypting them. Also, once the device is infected, the injected malware uses military-grade encryption to lock everything, including documents, photos, videos, databases, and other important files.
The Robinhood Mechanism – The Process
So, what happens after the encryption is in place? Well, as common ransomware operates, for decryption, a certain ransom has to be paid.
The threat actors send some sort of message, alerting users that their systems have been compromised. Within the text, they usually ask the victims to transfer a certain amount of money, mainly through BitCoin payments.
However, with GoodWill, the message is there, but the content is different. Again, they’re not after the money, they’re helping those in need. They ask the victim to go through three socially-driven activities to be able to obtain the decryption kit.
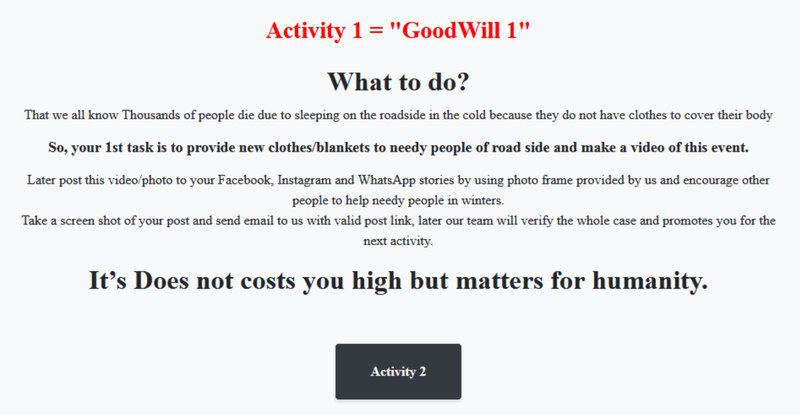
- First, give clothes to homeless individuals, record everything, and share it on social media.
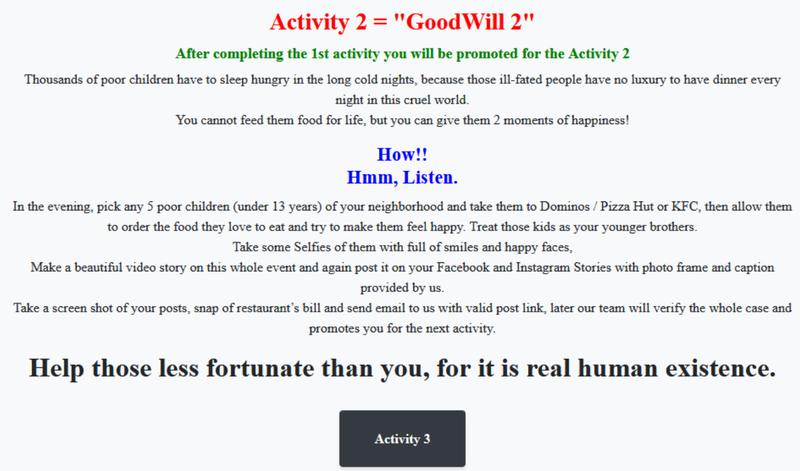
- Accompany five poor children for a meal at places like Dominos, Pizza Hut, or KFC. Also, record videos and take pictures to post on social media.
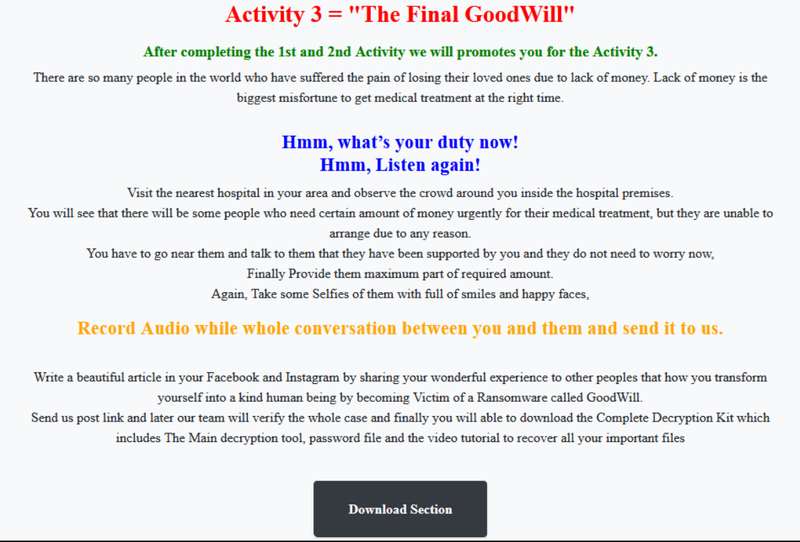
- Make some sort of payment to those who need urgent medical attention at a hospital nearby. This has to be recorded via audio and sent directly to the operators.
As mentioned, the group seems to be operating from India. At least that’s what the analysis of the email address and network artifacts suggests.
It doesn’t stop here. Apparently, further investigations revealed a lot more information about this ransomware. As it turned out, GoodWill ransomware showed significant overlaps with another Windows-based strain- HiddenTear.
It gained the status of being the first open-sourced proof-of-concept (PoC) ransomware by a Turkish programmer in 2015.
GoodWill Ransomware – Thanks, but No Thanks
The people behind this ransomware may have good intentions in mind, but there are better ways than cybercrime to achieve them.
Ransomware is ransomware and it’s illegal. Regardless of the outcome, you’re still considered cybercriminals. So far, there are no known victims of GoodWill, but at this rate, we’re bound to hear about some.