A Large-Scale Click Fraud Alert – Gamers Beware
Threat actors are evolving, especially when it comes to creating different forms of attacks to target their victims. Now, the gaming industry is once again in the spotlight as it’s involved in a large-scale click fraud campaign.

Fortunately, none other than Microsoft discovered the campaign and discussed everything in detail. Apparently, the attackers are using a browser node-WebKit and malicious browser extensions in their practices.
This is not the first time that gamers were targets of such attacks. However, we might know what the end result is: Installing crypto-miners and info-stealers. We’ve discussed the entire operation in the following article.
The Ultimate Fraud – Get Cheats, Get Hacked
Gamers have had their fair share of cyberattacks in 2022. Unfortunately, these campaigns can have a huge impact as games now harness millions of users.
A few months back, one of the most popular games “Valorant“ saw an attack where hackers trick players into downloading the RedLine malware.
Now, Krunker – another first-person shooter game – is the new target. Players around the world want to be the best. However, some of them like to take the shorter route, i.e, use cheats.
When someone posts such files on the web, millions will try to obtain them. In Krunker’s case, the files are definitely malicious.
It all begins with an ISO file. The user can download it straight from a malicious ad or comment on Youtube. Once the victim downloads the file, it’ll install a browser node-WebKit (aka NW.js) or rogue browser extension.
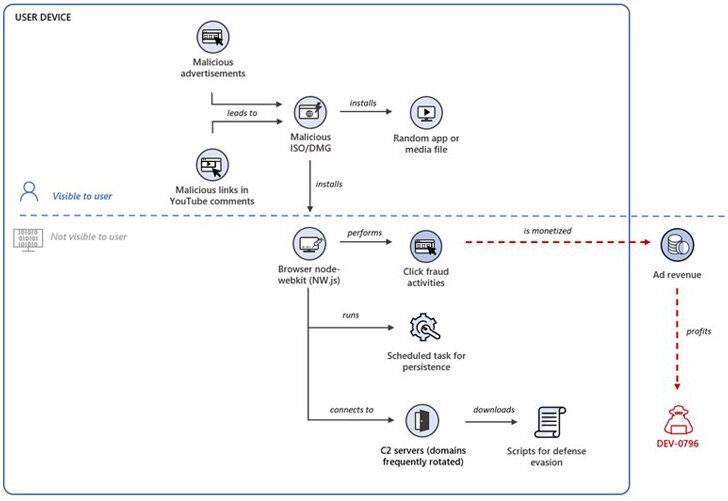
The entire process is presented in the image above. This time around, having an advantage beyond the available capabilities during gameplay may cost a lot.
Aside from ISO formats, Microsoft noted that DMG files are also present in the attack. These are Apple Disk Images, indicating that the attack is targeting several operating systems.
Here’s what Microsoft’s Security Team shared via their Twitter account:
“Microsoft researchers are tracking an ongoing wide-ranging click fraud campaign where attackers monetize clicks generated by a browser node-webkit or malicious browser extension secretly installed on devices. Microsoft attributes the attack to a threat actor tracked as DEV-0796.”
Aside from that, Microsoft is urging users to turn on PUA protection. This process blocks the installation of malicious and unwanted programs.
Moreover, users should enable Defender SmartScreen to block themselves from visiting any malicious download sites.
Krunker Click Fraud – From Cheats to Large-Scale Attacks
Cyber attacks are on the rise and everyone has become a target. Threat actors are running full-scale campaigns with different techniques that ensure high success rates.
The gaming industry is an easy target as users may fall for any trick if they think it’s going to help elevate their skills (Cheats). If you’re a gamer, make sure to take proper precautions and stay vigilant all the time.
Finally, cheats are for, well, cheaters. The game won’t be fun when you use such tactics. Try to avoid them at all costs.





